Apache released a security advisory to address a critical severity vulnerability in Struts2. Tracked as CVE-2024-53677, successful exploitation of the vulnerability may allow a remote attacker to execute arbitrary code, leading to critical data loss and possible system compromise.
A quick search revealed more than 3,555,000 targets on Fofa at the time of writing.
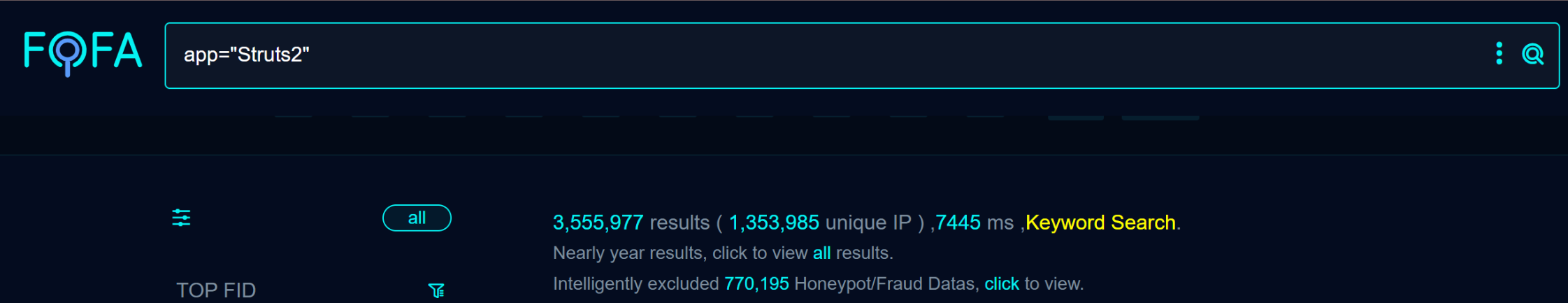
Apache Struts 2 is an open-source framework for developing Java web applications based on the Model-View-Controller (MVC) architecture. The framework allows developers to build enterprise-ready web applications with features like data validation and integration with other frameworks like Hibernate.
Vulnerability Details
The vulnerability exists in Apache Struts’s file upload mechanism. An attacker may exploit the vulnerability by manipulating file upload parameters to enable path traversal, bypass security mechanisms to upload files to arbitrary locations within the server, or execute malicious code by uploading and triggering executable files, such as .jsp scripts or binary payloads. Apache Struts advisory says the vulnerability is not backward compatible with older file upload mechanisms.
Affected Versions
- Struts 2.0.0 – Struts 2.3.37 (End-of-life)
- Struts 2.5.0 – Struts 2.5.33 (End-of-life)
- Struts 6.0.0 – Struts 6.3.0.2
Mitigation
Customers must upgrade to Apache Struts 6.4.0 or later and migrate to the new file upload mechanism to patch the vulnerability.
Please refer to the Apache Struts2 Security Advisory for more information.
Qualys Detection
Qualys customers can scan their devices with QIDs 382578, 382573, and 732114 to detect vulnerable assets and QID 152528 to detect vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://cwiki.apache.org/confluence/display/WW/S2-067
https://github.com/TAM-K592/CVE-2024-53677-S2-067