Ivanti released a security advisory to address critical and high severity vulnerabilities on January 8, 2025. Tracked as CVE-2024-0282 and CVE-2025-0283, the vulnerabilities may allow remote unauthenticated attackers to achieve remote code execution or local authenticated attackers to escalate their privileges on a targeted system.
Ivanti mentioned in the advisory that “a limited number of customers whose appliances have been exploited due to CVE-2025-0282.”
CISA added the CVE-2024-0282 to its Known Exploited Vulnerabilities Catalog, acknowledging its active exploitation. CISA urged users to patch the vulnerability before January 15, 2025.
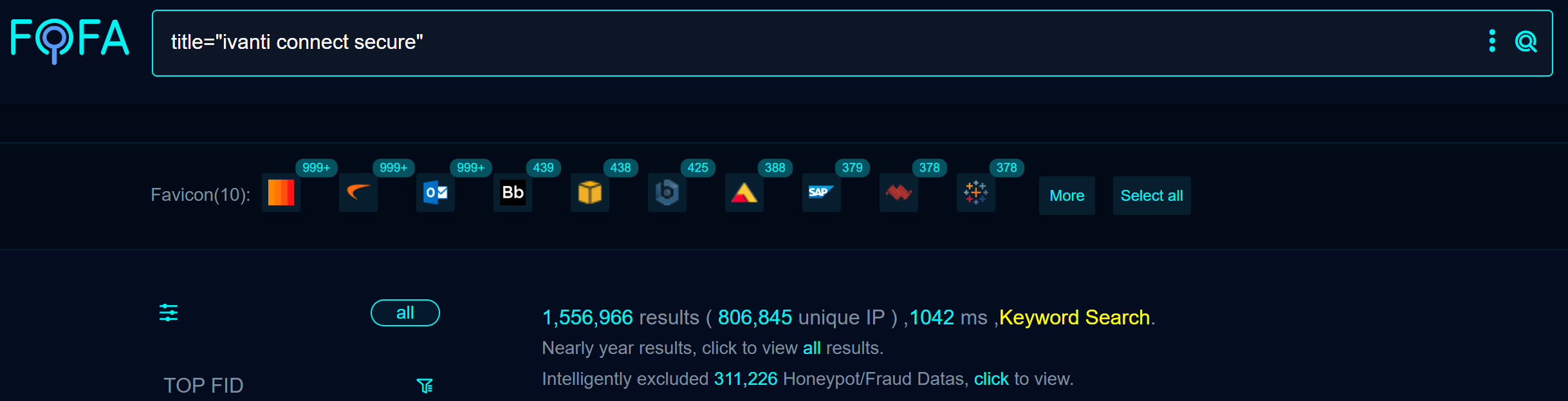
A quick search revealed more than 1,550,000 targets on Fofa at the time of writing.
Ivanti Cloud Services Application (CSA) is a landing page for Ivanti Endpoint Manager and Endpoint Security for Endpoint Manager. It provides access to product downloads, documentation, configuration and troubleshooting guides, and knowledge base.
Ivanti Policy Secure (IPS) is a Network Access Control (NAC) solution that provides authorized and secured users and devices with access. It’s a central policy management server that validates the user’s identity and determines the endpoint’s security compliance.
CVE-2025-0282
The vulnerability has a critical severity rating with a CVSS score of 9.0. This stack-based buffer overflow vulnerability impacts Ivanti Connect Secure, Policy Secure, and Neurons for ZTA gateways. Successful exploitation of the vulnerability may allow a remote unauthenticated attacker to achieve remote code execution.
CVE-2025-0283
The vulnerability has a high severity rating with a CVSS score of 7.0. This stack-based buffer overflow vulnerability impacts Ivanti Connect Secure, Policy Secure, and Neurons for ZTA gateways. Successful exploitation of the vulnerability may allow a local authenticated attacker to escalate their privileges.
Exploitation Details
Ivanti has mentioned in the security advisory that the exploitation of CVE-2025-0282 can be identified by the Integrity Checker Tool (ICT). Ivanti urges customers to closely monitor their internal and external ICT to ensure the integrity and security of the entire network infrastructure.
Mandiant, a Google-owned company, analyzed multiple compromised Ivanti Connect Secure appliances from various organizations. The organization utilized insights collected from the analysis of the exploited devices.
Mandiant observed the deployment of the previously observed SPAWN malware ecosystem on some of the analyzed devices. UNC5337, a cluster of activity moderately confidently identified as belonging to UNC5221—further explained in the Attribution section—has been credited with deploying the SPAWN malware ecosystem after targeting Ivanti Secure Connect appliances.
Affected and Patched versions
| CVE | Product Name | Affected Versions | Resolved Versions | Patch Availability |
| CVE-2025-0282 | Ivanti Connect Secure | 22.7R2 through 22.7R2.4 | 22.7R2.5 | Download Portal https://portal.ivanti.com/ |
| CVE-2025-0283 | Ivanti Connect Secure | 22.7R2.4 and prior,
9.1R18.9 and prior |
22.7R2.5 | Download Portal https://portal.ivanti.com/ |
| CVE-2025-0282 | Ivanti Policy Secure | 22.7R1 through 22.7R1.2 | Patch planned availability: January 21 | |
| CVE-2025-0283 | Ivanti Policy Secure | 22.7R1.2 and prior | Patch planned availability: January 21 | |
| CVE-2025-0282 | Ivanti Neurons for ZTA gateways | 22.7R2 through 22.7R2.3 | 22.7R2.5 | Patch planned availability: January 21 |
| CVE-2025-0283 | Ivanti Neurons for ZTA gateways | 22.7R2.3 and prior | 22.7R2.5 | Patch planned availability: January 21 |
Please refer to the Ivanti Security Advisory for more information.
Qualys Detection
Qualys customers can scan their devices with QIDs 732166, 732167, 152593, 152594, 152595, and 152596 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://cloud.google.com/blog/topics/threat-intelligence/ivanti-connect-secure-vpn-zero-day
https://forums.ivanti.com/s/article/Security-Advisory-Ivanti-Connect-Secure-Policy-Secure-ZTA-Gateways-CVE-2025-0282-CVE-2025-0283?language=en_US