Broadcom released a security advisory to address three vulnerabilities impacting VMware ESXi, Workstation, and Fusion. Tracked as CVE-2025-22224, CVE-2025-22225, & CVE-2025-22226, the vulnerabilities are being exploited in the wild. Security researchers at Microsoft Threat Intelligence Center discovered and reported the vulnerabilities to Broadcom.
CISA added the vulnerabilities to its Known Exploited Vulnerabilities Catalog, urging users to patch the flaw before March 25, 2025.
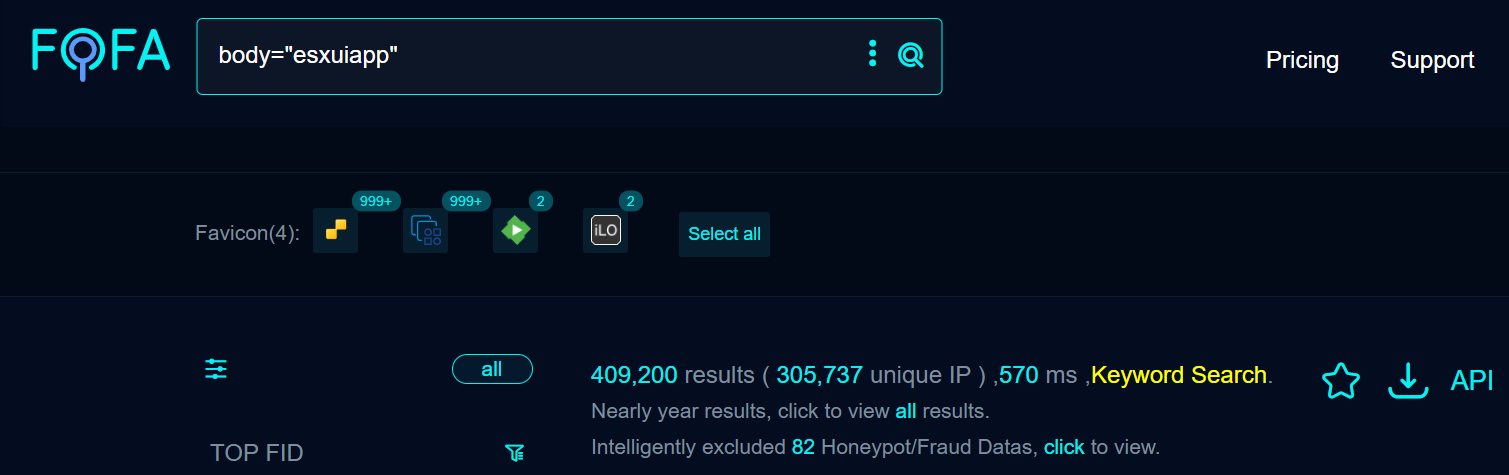
A quick search revealed more than 409,000 targets on Fofa at the time of writing.
VMware ESXi is a hypervisor that allows users to create and manage virtual machines (VMs) on physical servers. It’s a key part of VMware’s infrastructure software suite.
VMware Workstation is a program that allows users to run multiple operating systems on a single computer. It’s a hypervisor that creates virtual machines (VMs) that run alongside the host machine.
VMware Fusion is a software hypervisor explicitly designed for macOS systems. It enables virtual machines with guest operating systems like Microsoft Windows, Linux, or macOS to run within the host macOS operating system.
CVE-2025-22224: VMCI heap-overflow vulnerability
The vulnerability has a critical severity rating with a CVSS score of 9.3. The TOCTOU (Time-of-Check Time-of-Use) vulnerability in VMware ESXi and Workstation may lead to an out-of-bounds write. An attacker with local administrative privileges on a virtual machine may exploit the vulnerability to execute code as the VMX process runs on the host.
CVE-2025-22225: VMware ESXi arbitrary write vulnerability
The vulnerability has an important severity rating with a CVSS score of 8.2. the arbitrary write vulnerability impacts VMware ESXi. An attacker with privileges within the VMX process may trigger an arbitrary kernel write that leads to an escape from the sandbox.
CVE-2025-22226: HGFS information-disclosure vulnerability
The vulnerability has an important severity rating with a CVSS score of 7.1. The information disclosure vulnerability originates from an out-of-bounds read in HGFS and impacts VMware ESXi, Workstation, and Fusion. An attacker with administrative privileges to a virtual machine may exploit the vulnerability to leak memory from the vmx process.
Affected Versions
- VMware ESXi 7.0
- VMware ESXi 8.0 2D
- VMware ESXi 8.0 3D
- VMware Fusion 13.x
- VMware Workstation 17.x
Mitigation
Customers must upgrade to the following versions to patch the vulnerabilities:
- VMware Fusion 13.6.3
- VMware Workstation 17.6.3
- VMware ESXi 7.0 patch ESXi70U3s-24585291
- VMware ESXi 8.0 2D patch ESXi80U2d-24585300
- VMware ESXi 8.0 3D patch ESXi80U3d-24585383
For more information, please refer to the VMware Advisory (VMSA-2025-0004).
Qualys Detection
Qualys customers can scan their devices with QIDs 216335, 216336, 382908, and 382910 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.