Ivanti released a security advisory to address a security flaw impacting Ivanti Connect Secure, Ivanti Policy Secure, and ZTA gateways. Tracked as CVE-2025-22457, the vulnerability has a critical severity rating with a CVSS score of 9.0. Successful exploitation of the buffer overflow vulnerability may allow a remote, unauthenticated attacker to execute arbitrary code, leading to critical data loss and possible system compromise.
Ivanti mentioned in the advisory, “We are aware of a limited number of customers whose Ivanti Connect Secure (22.7R2.5 or earlier) and End-of-Support Pulse Connect Secure 9.1x appliances have been exploited at the time of disclosure. Pulse Connect Secure 9.1x reached End-of-Support on December 31, 2024, and no longer receives code support or changes.”
Ivanti patched the vulnerability in Ivanti Connect Secure 22.7R2.6 in February 2025. Initially, the vulnerability was identified as a product bug.
Mandiant, who discovered the vulnerability, mentioned in their article that it has been exploited since mid-March 2025. The reports suggested that the vulnerability was used to deploy two newly identified malware families, TRAILBLAZE and BRUSHFIRE, using a shell script dropper. Additionally, there is proof that the vulnerability is used to deploy the SPAWN malware ecosystem (UNC5221). UNC5221 is a suspected China-nexus espionage actor used in conducting zero-day exploitation of edge devices dating back to 2023.
CISA added the CVE-2025-22457 to its Known Exploited Vulnerabilities Catalog, urging users to patch the flaw before April 11, 2025.
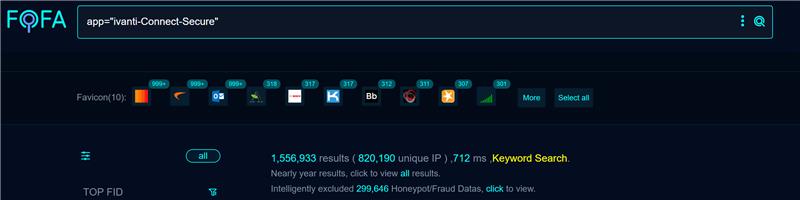
A quick search revealed more than 1,550,000 publicly available targets on Fofa at the time of writing.
Affected Versions
- ZTA Gateways versions before 22.8R2
- Ivanti Policy Secure versions before 22.7R1.4
- Ivanti Connect Secure versions before 22.7R2.5
- Pulse Connect Secure (EoS) versions before 9.1R18.9
Mitigation
Users must upgrade to the following versions to patch the vulnerability:
- ZTA Gateways version 22.8R2
- Ivanti Policy Secure version 22.7R1.4
- Ivanti Connect Secure version 22.7R2.6 (released in February 2025)
- Pulse Connect Secure (EoS) version 22.7R2.6
For more information, please refer to the Ivanti Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 732234, 732410, 152917, and 152918 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-exploiting-critical-ivanti-vulnerability
https://forums.ivanti.com/s/article/April-Security-Advisory-Ivanti-Connect-Secure-Policy-Secure-ZTA-Gateways-CVE-2025-22457?language=en_US