Microsoft’s May 2025 Patch Tuesday rolls out critical security updates, addressing multiple vulnerabilities across Windows, Office, and other key products. Here’s a quick breakdown of what you need to know.
In this month’s Patch Tuesday, May 2025 edition, Microsoft addressed 76 vulnerabilities. The updates include five critical and 66 important severity vulnerabilities. In this month’s updates, Microsoft has addressed five zero-day vulnerabilities being exploited in the wild. Microsoft also addressed one publicly disclosed vulnerability.
Microsoft has addressed six vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, May edition includes updates for vulnerabilities in Windows Routing and Remote Access Service (RRAS), Windows Virtual Machine Bus, Windows Installer, Windows Drivers, Windows File Server, Azure, Windows Win32K – GRFX, Microsoft Scripting Engine, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, and Remote Code Execution (RCE).
The May 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 2 | Important: 2 |
| Denial of Service Vulnerability | 7 | Important: 7 |
| Elevation of Privilege Vulnerability | 18 | Important: 18 |
| Information Disclosure Vulnerability | 14 | Important: 14 |
| Remote Code Execution Vulnerability | 28 | Critical: 5 Important: 23 |
| Security Feature Bypass Vulnerability | 2 | Important: 2 |
Zero-day Vulnerabilities Patched in May Patch Tuesday Edition
CVE-2025-26685: Microsoft Defender for Identity Spoofing Vulnerability
Microsoft Defender for Identity is a cloud-based security solution that helps organizations monitor and secure their identities across hybrid environments. It enhances security by providing an identity-centric approach to threat detection, leveraging data from on-premises Active Directory and cloud-based identities.
The improper authentication vulnerability could allow an unauthenticated attacker with LAN access to perform spoofing over an adjacent network.
CVE-2025-30400: Microsoft DWM Core Library Elevation of Privilege Vulnerability
The Microsoft Desktop Window Manager (DWM) Core Library is a crucial system component in Windows that manages the display of all visual elements on a computer screen.
The use-after-free vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
CISA added CVE-2025-30400 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before June 3, 2025.
CVE-2025-32701: Windows Common Log File System Driver Elevation of Privilege Vulnerability
The Windows Common Log File System (CLFS) is a high-performance, general-purpose logging subsystem used by kernel and user-mode applications. It’s designed for building transactional logs and is frequently employed in applications like database systems, messaging systems, and online transactional processing (OLTP).
The use-after-free vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
CISA added CVE-2025-32701 to its Known Exploited Vulnerabilities Catalog and requested that users patch it before June 3, 2025.
CVE-2025-32706: Windows Common Log File System Driver Elevation of Privilege Vulnerability
The improper input validation vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
CISA added CVE-2025-32706 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before June 3, 2025.
CVE-2025-30397: Scripting Engine Memory Corruption Vulnerability
A scripting engine is a software component that interprets and executes instructions written in a scripting language. It’s essentially a runtime environment that processes scripts, allowing them to interact with an application or system.
An attacker must convince an authenticated user to click a link to initiate remote code execution. Successful exploitation of the vulnerability may allow an unauthenticated attacker to execute code over a network.
CISA added CVE-2025-30397 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before June 3, 2025.
CVE-2025-32709: Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
The Windows Ancillary Function Driver (AFD) is a kernel-mode driver that serves as the entry point for the Windows Sockets (Winsock) API. It handles the low-level details of network communication, acting as a bridge between applications using the Winsock API and the network stack.
The use-after-free vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
CISA added CVE-2025-32709 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before June 3, 2025.
Critical Severity Vulnerabilities Patched in May Patch Tuesday Edition
CVE-2025-29966 & CVE-2025-29967: Remote Desktop Client Remote Code Execution Vulnerability
A Remote Desktop Protocol client is a software application that allows users to connect to and control a remote computer or server, using a secure network connection. It essentially enables users to operate a remote machine as if they were physically sitting in front of it.
The heap-based buffer overflow vulnerability may allow an unauthenticated attacker to execute code remotely.
CVE-2025-30377 & CVE-2025-30386: Microsoft Office Remote Code Execution Vulnerability
The use-after-free vulnerability could allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-29833: Microsoft Virtual Machine Bus (VMBus) Remote Code Execution Vulnerability
The Microsoft Virtual Machine Bus (VMBus) is a virtual communication channel used within the Microsoft Hyper-V virtualization environment. It facilitates communication and data transfer between the parent (host) and child (guest) partitions, enabling virtual machines (VMs) to access and interact with resources on the host system.
Time-of-check time-of-use (toctou) race condition in Windows Virtual Machine Bus could allow an authenticated attacker to achieve remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2025-24063 is an elevation privilege vulnerability in the Kernel Streaming Service Driver. The heap-based buffer overflow vulnerability could allow an authenticated attacker to gain SYSTEM privileges.
- CVE-2025-30388 is a remote code execution vulnerability in Windows Graphics Component. The heap-based buffer overflow vulnerability could allow an unauthenticated attacker to achieve remote code execution.
- CVE-2025-30385 is an elevation privilege vulnerability in the Windows Common Log File System Driver. Upon successful exploitation, an authenticated attacker could potentially gain the ability to crash the system.
- CVE-2025-29841 is an elevation privilege vulnerability in the Universal Print Management Service. Successful exploitation of the vulnerability requires an attacker to win a race condition. Upon successful exploitation of the vulnerability, an authenticated attacker could elevate privileges locally.
- CVE-2025-29971 is a denial of service vulnerability in Web Threat Defense (WTD.sys). Successful exploitation of the vulnerability could allow an unauthenticated attacker to deny service over a network.
- CVE-2025-29976 is an elevation of privilege vulnerability in Microsoft SharePoint Server. An improper privilege management flaw could allow an authenticated attacker to elevate privileges locally.
- CVE-2025-30382 is a remote code execution vulnerability in Microsoft SharePoint Server. The deserialization of untrusted data could allow an unauthenticated attacker to achieve remote code execution.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Visual Studio Code, Windows Kernel, .NET, Visual Studio, and Build Tools for Visual Studio, Remote Desktop Gateway Service, Microsoft Defender for Endpoint, Microsoft Defender for Identity, Windows Secure Kernel Mode, Windows Hardware Lab Kit, Azure DevOps, Microsoft Edge (Chromium-based), Microsoft Dataverse, Azure Automation, Windows Trusted Runtime Interface Driver, Windows Media, Universal Print Management Service, UrlMon, Windows LDAP – Lightweight Directory Access Protocol, Windows Hyper-V, Windows SMB, Windows Deployment Services, Windows Remote Desktop, Active Directory Certificate Services (AD CS), Windows Fundamentals, Microsoft Brokering File System, Web Threat Defense (WTD.sys), Azure Storage Resource Provider, Azure File Sync, Microsoft PC Manager, Microsoft Office SharePoint, Microsoft Office Excel, Microsoft Office PowerPoint, Microsoft Office, Windows Common Log File System Driver, Windows DWM, Visual Studio, Microsoft Office Outlook, Windows NTFS, Windows Ancillary Function Driver for WinSock, and Microsoft Power Apps.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
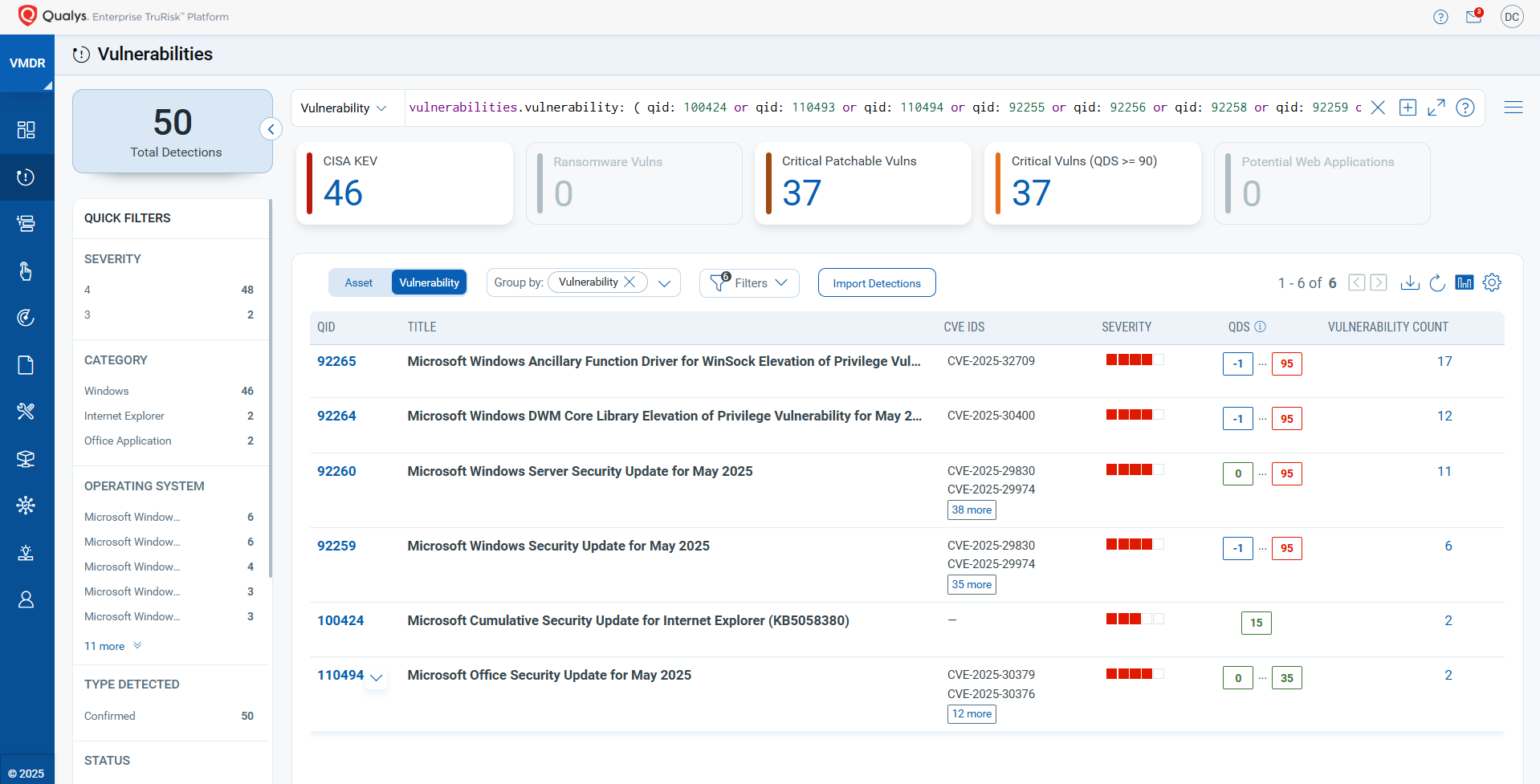
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 100424 or qid: 110493 or qid: 110494 or qid: 92255 or qid: 92256 or qid: 92258 or qid: 92259 or qid: 92260 or qid: 92261 or qid: 92262 or qid: 92263 or qid: 92264 or qid: 92265 )
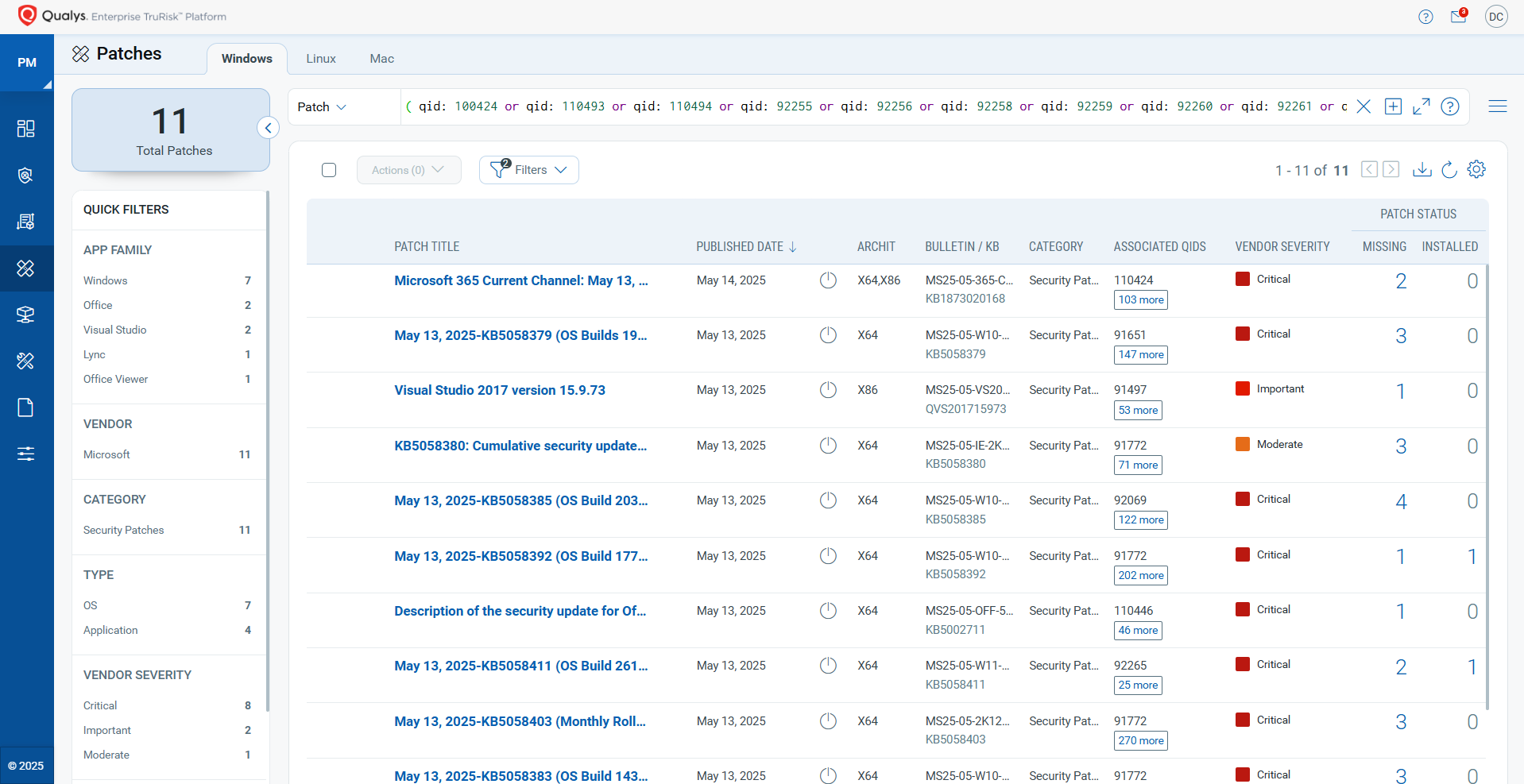
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select the respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 100424 or qid: 110493 or qid: 110494 or qid: 92255 or qid: 92256 or qid: 92258 or qid: 92259 or qid: 92260 or qid: 92261 or qid: 92262 or qid: 92263 or qid: 92264 or qid: 92265 )
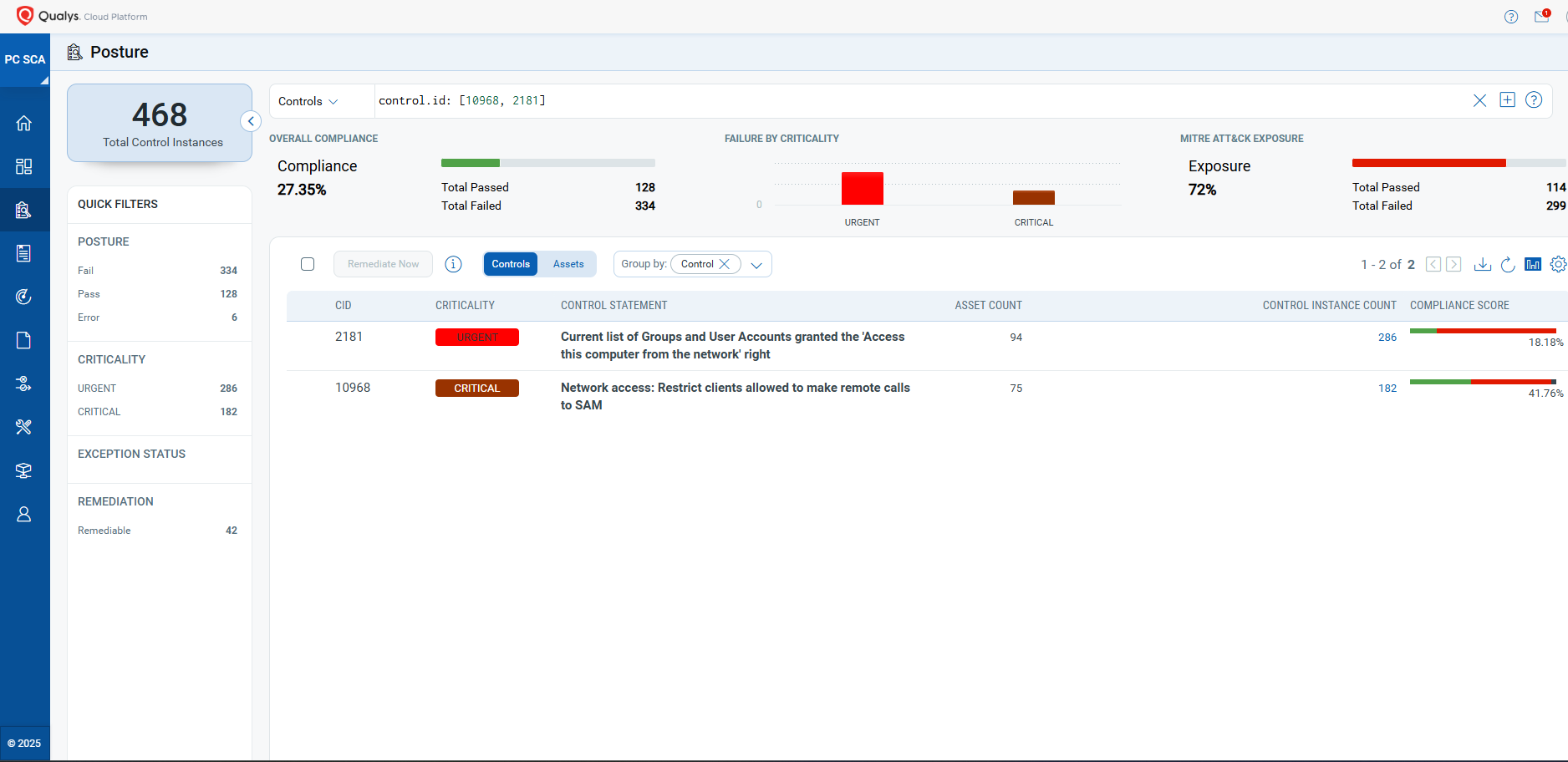
EVALUATE Vendor-Suggested Mitigation with Policy Audit
With Qualys Policy Audit’s Out-of-the-Box Mitigation or Compensatory Controls, reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now; these security controls are not recommended by any industry standards, such as CIS, DISA-STIG.
Qualys Policy Audit team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice that exists in a default state and could reduce the severity of a vulnerability’s exploitation.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Audit Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2025-26685: Microsoft Defender for Identity Spoofing Vulnerability
This vulnerability has a CVSS: 3.1 6.5 / 5.7
Policy Audit Control IDs (CIDs):
- 10968 Network access: Restrict clients allowed to make remote calls to SAM
- 2181 Current list of Groups and User Accounts granted the ‘Access this computer from the network’ right
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [10968, 2181]
Visit the May 2025 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 100424, 110493, 110494, 92255, 92256, 92258, 92259, 92260, 92261, 92262, 92263, 92264, and 92265 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2025-May
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-26685
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-30400
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-32701
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-32706
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-30397
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-32709
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-29966
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-29967
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-30377
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-30386
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-29833