Security researchers at Project Discovery discovered two critical zero-day vulnerabilities in Versa Concerto, a popular SD-WAN and network orchestration platform. When exploited together, the vulnerabilities may allow attackers to fully compromise the application and the underlying host system.
The vulnerabilities affect key elements of the platform, which are based on Docker containers, Spring Boot, and the Traefik reverse proxy. The problems range from critically misconfigured Docker volumes, and vulnerable Traefik behavior to inconsistent URL parsing and uncontrolled file writes.
Versa Concerto provides enterprises with seamless policy management, analytics, and automation. It delivers end-to-end orchestration functions of services, including configuration design, implementation, zero-touch provisioning, deployment, monitoring, and analytics capabilities for our SD-WAN, NGFW, UTM, Routing, uCPE, and Versa Secure Access (VSA) services.
CVE-2025-34025
The privilege escalation and container escape vulnerabilities originate from an unsafe default mounting of host binary paths that allows the container to modify host paths. Depending on the operating system configuration, the escape can trigger remote code execution or direct host access.
CVE-2025-34026
The authentication bypass vulnerability in the Traefik reverse proxy configuration could allow an attacker to access administrative endpoints. The internal Actuator endpoint can be leveraged to access heap dumps and trace logs.
CVE-2025-34027
The authentication bypass vulnerability in the Traefik reverse proxy configuration could allow an attacker to access administrative endpoints. The vulnerability exists in the /portalapi/v1/package/spack/upload endpoint in the web-service component that could allow arbitrary file writes. The Spack upload endpoint can be leveraged for a Time-of-Check to Time-of-Use (TOCTOU) write in combination with a race condition to achieve remote code execution via path loading manipulation, resulting in unauthenticated remote code execution.
The Qualys Threat Research Unit confirmed the vulnerability by successfully testing the proof of concept in the lab environment.
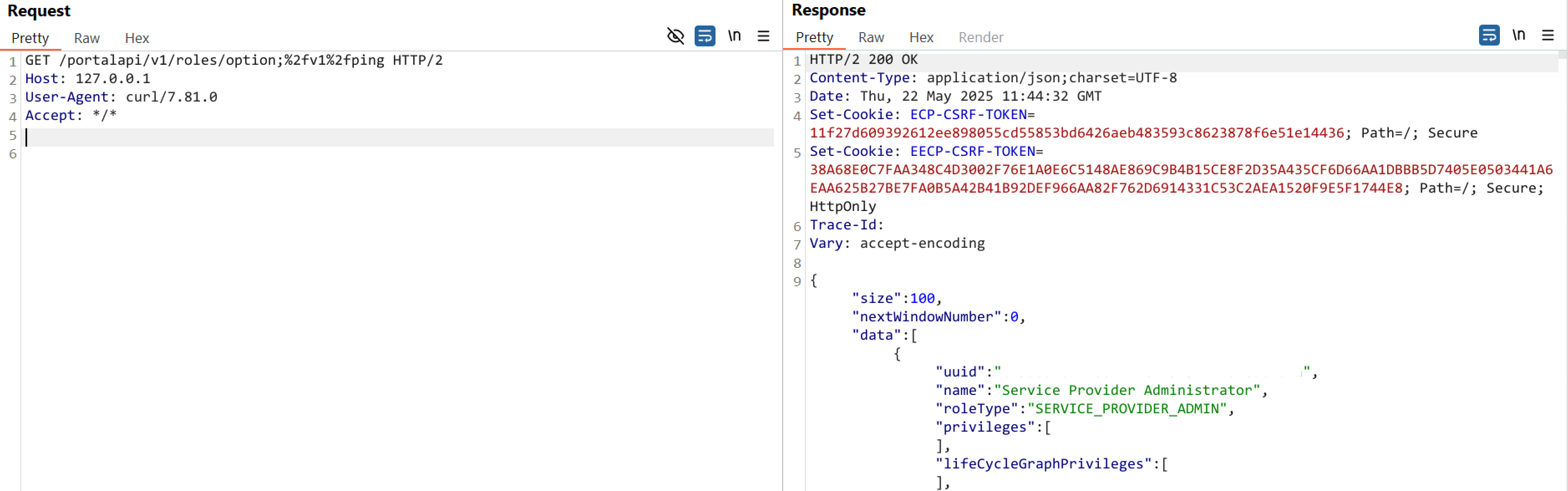 Image Source: Qualys Threat Research Unit
Image Source: Qualys Threat Research Unit
Recommended Mitigation
Since the vendor has not acknowledged the vulnerabilities yet, Project Discovery recommended some mitigation measures listed below:
- Block Semicolons in URL Paths: Implement rules to reject requests containing semicolons (;) in URL paths to prevent exploitation of the URL decoding issue.
- Filter-Specific Connection Headers: Configure reverse proxies or web application firewalls to drop requests where the Connection header includes X-Real-Ip, mitigating unauthorized access to Actuator endpoints.
Qualys Detection
Qualys customers can scan their devices with QID 732555 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://projectdiscovery.io/blog/versa-concerto-authentication-bypass-rce