A critical remote code execution vulnerability (CVE-2025-47916) in the Invision Community has come to light. The vulnerability may allow attackers to execute arbitrary code on the target system. The vulnerability puts countless forums and online communities at serious risk because of the popularity of the Invision Community.
Invision Community is a platform for building online communities. It provides tools for creating forums, blogs, file sharing, and other features to foster user engagement and collaboration. The platform aims to help businesses enhance customer loyalty, reduce support costs, and drive sales by building strong online communities.
The vulnerability
The vulnerability exists in the IPS\core\modules\front\system\themeeditor::customCss() method within the /applications/core/modules/front/system/themeeditor.php script. This method improperly processes user input from the content request parameter through the template engine. Successful exploitation of the vulnerability could allow unauthenticated attackers to inject and execute arbitrary PHP code.
The Qualys Threat Research Unit confirmed the vulnerability by successfully testing the proof of concept in the lab environment.
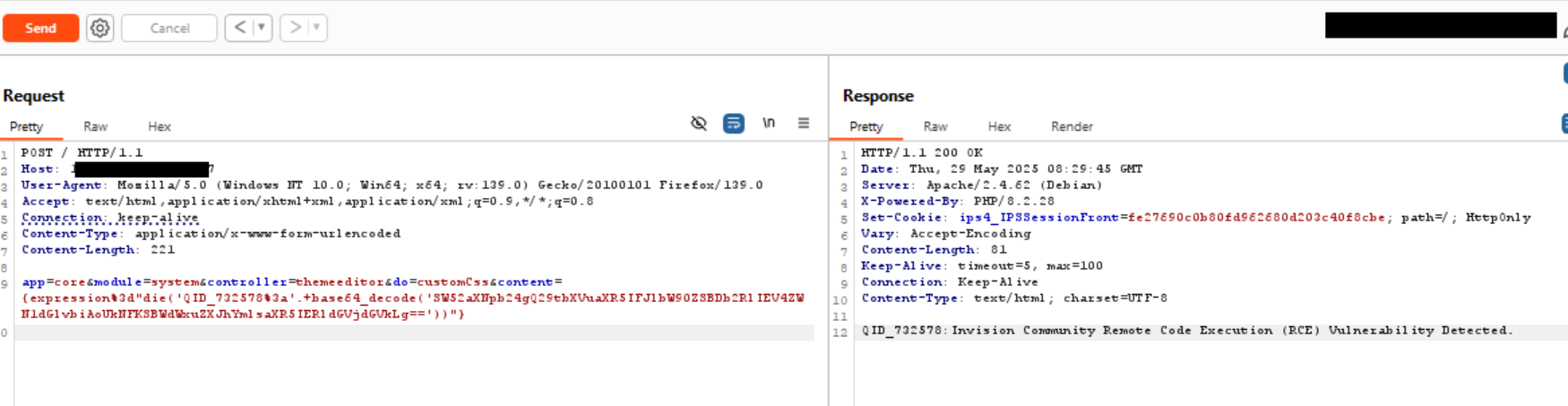 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
The vulnerability affects Invision Community versions from 5.0.0 to 5.0.7.
Mitigation
Users must upgrade to the Invision Community version 5.0.7 or later to patch the vulnerability.
For more information, please refer to the Invision Community Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 732578 and 530114 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://karmainsecurity.com/KIS-2025-02
https://invisioncommunity.com/release-notes-v5/507-r41/