Kentaro Kawane from GMO Cybersecurity discovered a vulnerability of critical severity impacting FortiWeb. Tracked as CVE-2025-25257, the vulnerability has a CVSS score of 9.6. Upon successful exploitation of the vulnerability, an unauthenticated attacker can execute unauthorized SQL code via crafted HTTP or HTTPS requests.
FortiWeb is a web application firewall (WAF) designed to protect web applications and APIs from various attacks, including those targeting known vulnerabilities and zero-day exploits. It uses machine learning and other techniques to detect and block malicious traffic, helping organizations maintain compliance with regulations.
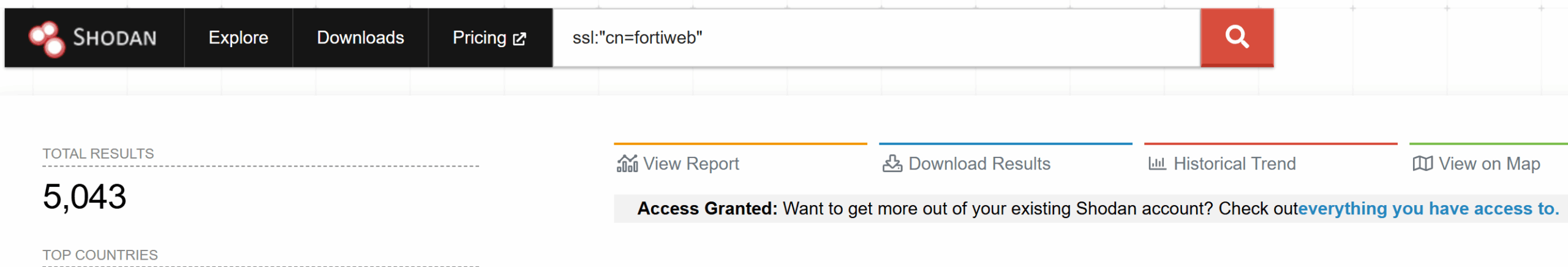
A quick search revealed more than 5,000 targets on Shodan at the time of writing.
CISA acknowledged the vulnerability’s active exploitation by adding it to its Known Exploited Vulnerabilities Catalog and urging users to patch it before August 8, 2025.
Vulnerability and Exploitation Details
The unauthenticated SQL injection exists in the /api/fabric/device/status endpoint. The flaw originates from automatically formatting an SQL query with the Bearer token from the HTTP Authorization header without sanitization.
An attacker may further exploit the SQL injection flaw to achieve remote code execution. The injected SQL enters a MySQL INTO OUTFILE query, allowing arbitrary file writes. An attacker can locate the CGI‑enabled ml-draw.py in the /cgi-bin folder. The Python’s .pth files in site-packages can be exploited to run code.
The Qualys Threat Research Unit has recreated the issue and tested it on the vulnerable version successfully.
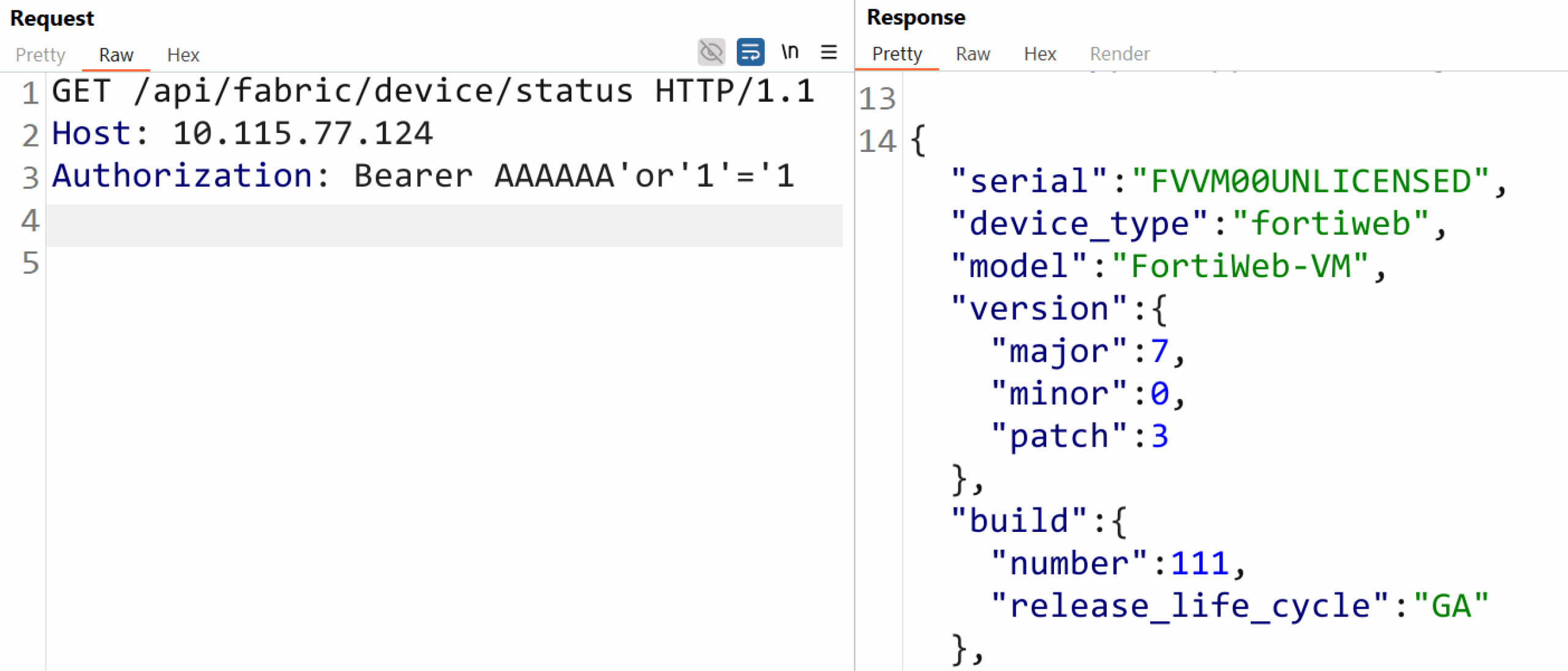
Image Source: Qualys Threat Research Unit (TRU)
Affected Versions
- FortiWeb 7.6.0 through 7.6.3
- FortiWeb 7.4.0 through 7.4.7
- FortiWeb 7.2.0 through 7.2.10
- FortiWeb 7.0.0 through 7.0.10
Mitigation
Users must upgrade to the following versions to patch the vulnerability:
- FortiWeb 7.6.0 through 7.6.4
- FortiWeb 7.4.0 through 7.4.8
- FortiWeb 7.2.0 through 7.2.11
- FortiWeb 7.0.0 through 7.0.11
Please refer to the Fortinet PSIRT Advisory (FG-IR-25-151) for more information.
Workaround
Users can disable the HTTP/HTTPS administrative interface as a temporary workaround.
Qualys Detection
Qualys customers can scan their devices with QIDs 44706, 530308, and 732762 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
Reference
https://www.fortiguard.com/psirt/FG-IR-25-151
https://labs.watchtowr.com/pre-auth-sql-injection-to-rce-fortinet-fortiweb-fabric-connector-cve-2025-25257/
The SQL injection vulnerability allows an attacker to exploit the MySQL INTO OUTFILE feature to write arbitrary files to the server, potentially leading to remote code execution.