CrushFTP warned its users about active exploitation of a zero-day vulnerability tracked as CVE-2025-54309. Successful exploitation of this vulnerability may allow remote attackers to obtain admin access via HTTPS on vulnerable servers.
The vendor mentioned in the advisory that they observed many exploits on the morning of July 18th; the actual exploits may have occurred a day earlier. Threat actors reverse-engineered their software, discovered this new bug, and exploited it on devices not running the latest versions of CrushFTP. Hackers re-used scripts from prior exploits to deploy scripts on CrushFTP servers.
CrushFTP is a cross-platform file transfer server that supports various protocols like FTP, SFTP, FTPS, and HTTPS. It’s designed for secure file transfers and offers user management, event handling, and remote synchronization features. Both home users and enterprises use it.
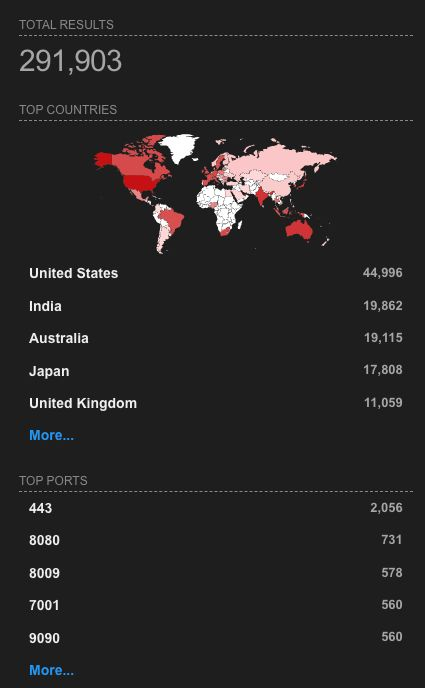
A quick search revealed over 250,000 targets on Shodan at the time of writing.
Qualys Threat Intelligence provided a Qualys Vulnerability Score (QVS) of 92 for the vulnerability. Qualys Vulnerability Score (QVS) is a Qualys-assigned score for a vulnerability based on multiple factors associated with the CVE, such as CVSS and external threat indicators like active exploitation, exploit code maturity, CISA known exploitable, and many more.
Affected Versions
- CrushFTP versions 10 before 10.8.5
- CrushFTP versions 11 before 11.3.4_23
Mitigation
Users must upgrade to the following versions to patch the vulnerability:
- CrushFTP 11.3.4_26
- CrushFTP 10.8.5_12
For more information, please refer to the CrushFTP Security Advisory.
Future Mitigation Steps
Users can apply the following:
- Limit IPs allowed for administration.
- Whitelist IPs that can connect to the server.
- Enterprise users use a DMZ CrushFTP instance in front.
- Allow automatic and frequent updating (Preferences, Updates).
Indicators of Compromises
- The MainUsers/default/user.XML has “last_logins”. This would not be normal.
- The modified date on your default user.XML is recent.
- Default user has admin access.
- Long random user IDs were created, for example, 7a0d26089ac528941bf8cb998d97f408m.
- Other usernames recently created with admin access.
- Buttons from the end-user WebInterface disappeared, and formerly regular user now has Admin buttons.
- Threat actors have been making the version display fake to give a false sense of security. Vendor provides the validate hashes function on the About tab to compare MD5 hashes. Users can look for extra code they may have installed into CrushFTP.
Qualys Detection
Qualys customers can scan their devices with QID 383614 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.crushftp.com/crush11wiki/Wiki.jsp?page=CompromiseJuly2025