In the month of July 2018 Oracle had released advisory addressing many vulnerabilities in its suit of products. In this post will discuss about CVE-2018-2894. It is a remote file upload vulnerability in WebLogic server due to improper authentication enforcement. Normally this page should not be accessible without authentication. The affected versions are 10.3.6.0, 12.1.3.0, 12.2.1.2, 12.2.1.3.
Vulnerability
Allows unauthenticated access to Weblogic Web Service Test client. Upon successful exploitation an attacker can achieve command execution by exploiting arbitrary file upload vulnerability. To exploit the target the attackers must access the Web Services Test client configuration page. From here the attacker can upload the desired .jsp file that will execute commands in the target environment. The following section will provide more details on exploitation of CVE-2018-2894.
Exploitation
A PoC for this vulnerability is available online. First we access the /ws_utc/config.do page.
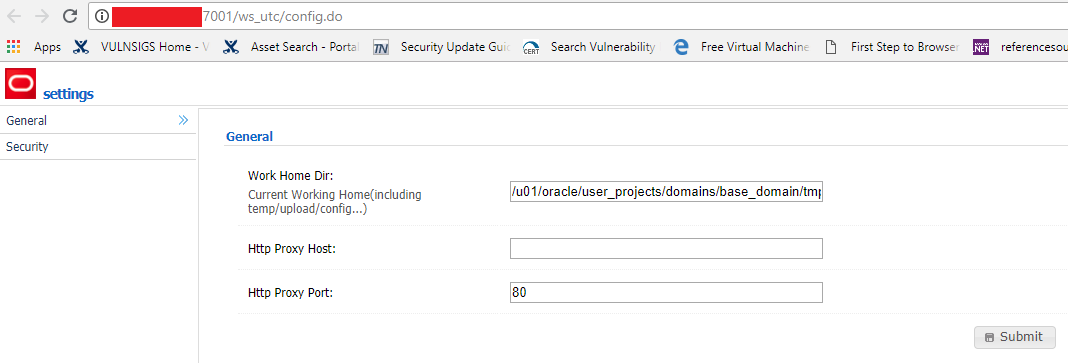
We set the working directory path and access the ‘Security’ and upload our .jsp file. The path is/u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle .webservices.wls.ws-testclient-app-wls/4mcj4y/war/css
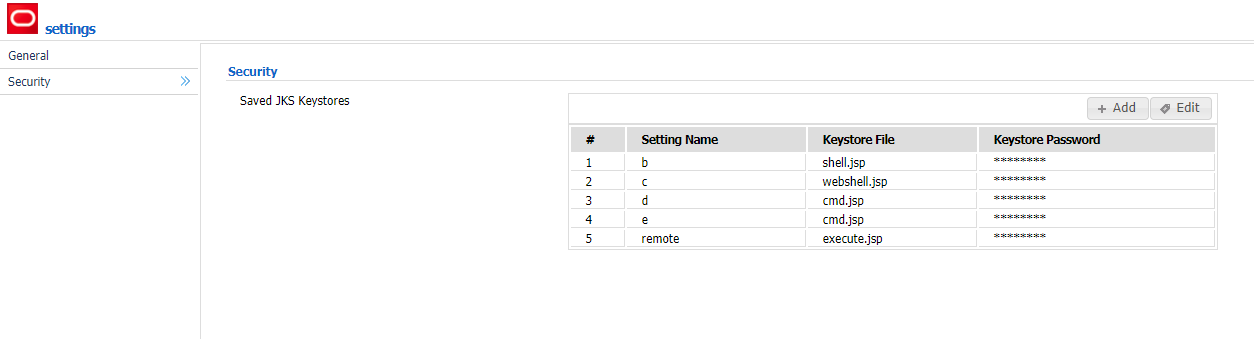
We obtain the timestamp of the uploaded file from packet trace.
 timestamp
timestamp
After uploading the file we access it via url http://<Server IP>:7001/ws_utc/css/config/keystore/<Timestamp>_<JSP file name>.jsp.
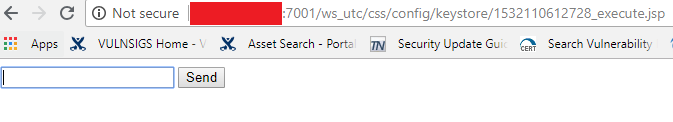
We can enter commands of or choice and it will be executed in the target environment. There limitation to the commands that can be executed via this method.
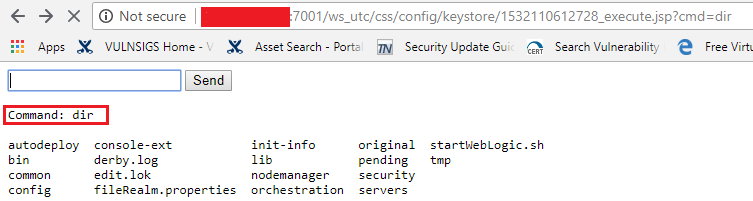
The uploaded JSP file can be a backdoor that can be used by an attacker for post exploit operations.
Mitigation
We request organizations to apply the latest patches released by Oracle to address this vulnerability. Qualys customers can scan their network with QID:87338 to detect vulnerable machines.
Qualys Detection
The QID sends HTTP GET request to ws_utc/config.do to check for authentication enforcement.
Please continue to follow Qualys Threat Protection for coverage on this vulnerability.
References
CVE-2018-2894
Oracle Critical Patch Update Advisory – July 2018