libssh is open source framework in C that implements SSHv2 protocol. Users can execute programs remotely, transfer files, build secure tunnels etc. An authentication bypass vulnerability was found in the server side implementation of libssh. All version of libssh from 0.6 and above are vulnerable. CVE-2018-10933 has been assigned to track this issue. The vulnerability has been addressed in versions 0.8.4 and libssh 0.7.6.
Vulnerability
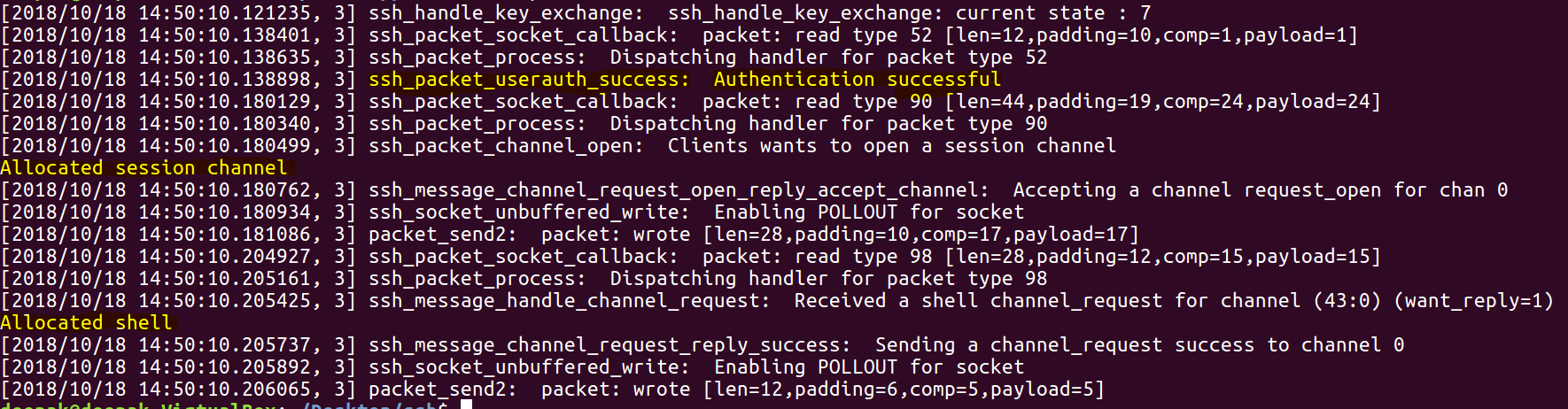
As mentioned previously it is authentication bypass vulnerability. Attackers (malicious client) can send a SSH2_MSG_USERAUTH_SUCCESS message instead of SSH2_MSG_USERAUTH_REQUEST. By doing so attackers can authenticate providing without valid credentials. PoC‘s targeting CVE-2018-10933 are available online . We have setup a simple libssh server to demo the exploit. the logs below are from a client that sends SSH2_MSG_USERAUTH_SUCCESS message, and is able to open channel to the target server with out any credentials.
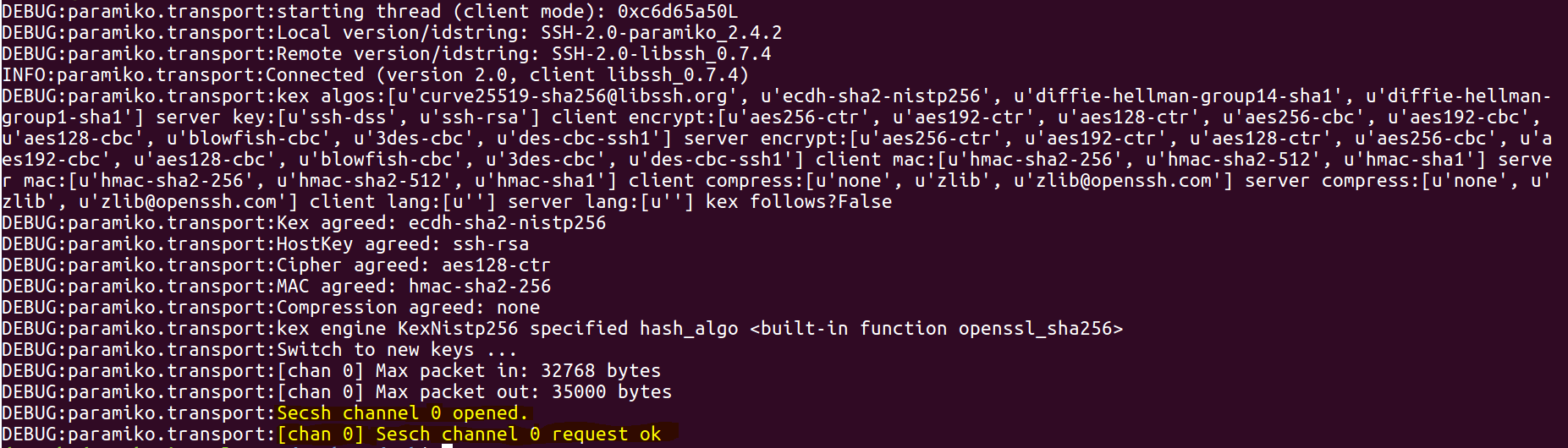
We can see the corresponding log on the server where it shows authentication was successful.
Mitigation
We request organizations to update libssh to the latest versions to address CVE-2018-10933. Qualys customers can scan using QID : 38747, to detect vulnerable machines. This QID detects vulnerable libssh versions based on SSH banner. Qualys will continue add more detections as vendors release their patches addressing this vulnerability.
Please continue to follow Qualys Threat Protection for more information on vulnerabilities.
References
Authentication bypass in server code
CVE-2018-10933
K52868493: libssh vulnerability CVE-2018-10933