Summary:
September MSPT has come with a local privilege-escalation vulnerability in Microsoft Windows.
Description:
Windows AppX Deployment Server improperly handles junctions resulting into privilege escalation. An attacker would first have to gain execution on the victim system, aka ‘Windows Elevation of Privilege Vulnerability‘ to exploit this vulnerability,
A Poc is available that demonstrates on Microsoft Edge. This PoC works only for all version of Windows 10 that are not patched with September (2019) update. The exploit firstly kills the processes named on “microsoftedge or edge” that is running on the system, if any. Furthermore, it creates junction from “C:\Users\{Environment.UserName}\AppData\Local\Packages\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\Settings“ and modifies the permission level to NT AUTHORITY\Authenticated Users” -> NT AUTHORITY\Authenticated Users:(I)(M)
This vulnerability Assigned to CVE-2019-1253 – Windows Elevation of Privilege Vulnerability.
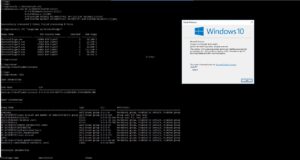
Above image depicts the windows 10 version that is not yet patched to September’s update, hence we can try to exploit it.
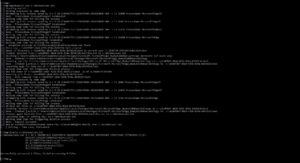
After successful execution of the exploit following behavior is observed:
It should open Microsoft Edge and it will “write” permissions to the target file.
To justify it, we’ve tried to create an appropriate presentation below:
Affected Products:
Microsoft Windows 10 ARM64-based/x64-based/32-bit Systems.
Microsoft Windows Server.
Advisory:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1253
Mitigation:
Updates are available. Please see the references or vendor advisory for more information. Qualys customers can scan their network with QID# 91572 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/padovah4ck/CVE-2019-1253
- https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-1253