Overview:
This January Patch Tuesday, Microsoft released patches related to Windows Remote Desktop Gateway (RD Gateway) that address the CVE-2020-0610 and CVE-2020-0609.
Microsoft Remote Desktop Gateway (RDG), previously known as Terminal Services Gateway, allows users on public networks to access Windows desktops and applications hosted in cloud environment. The RD Gateway component uses Secure Sockets Layer (SSL) to encrypt the communications channel between clients and the server. The RD Gateway machine must be accessible through a public IP address that allows inbound TCP connections to port 443 and inbound UDP connections to port 3391. This will allow users to connect remote systems through the HTTPS communications transport protocol and the UDP protocol.
Affected server version and patches:
Windows Server 2012: KB4534283 (Monthly Rollup), KB4534288 (Security-only)
Windows Server 2012 R2: KB4534297 (Monthly Rollup), KB4534309 (Security-only)
Windows Server 2016: KB4534271 (cumulative Update)
Windows Server 2019: KB4534273 (cumulative Update)
Vulnerabilities:
RDG supports three different protocols: HTTP, HTTPS, and UDP. The vulnerabilities exist in the UDP handler function that processes UDP packets. These vulnerabilities can be exploited before the RDP authentication and require no user interaction. An unauthenticated, remote attacker could send crafted RDP requests to execute arbitrary code on the target system.
Researcher made a PoC (DoS + scanner) to detect these vulnerabilities remotely,
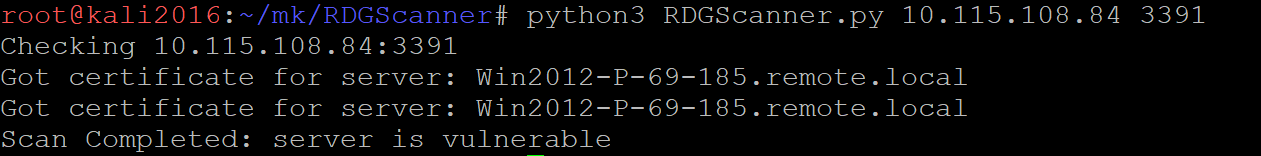
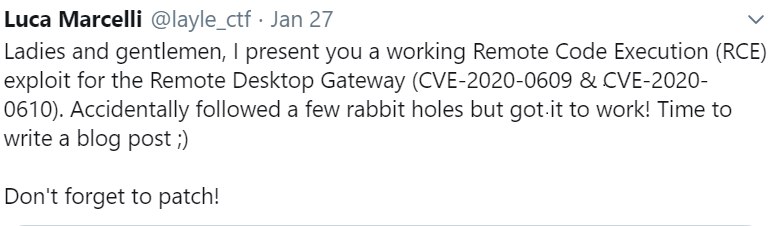
Recently, a researcher developed a working remote code execution exploit for these vulnerabilities; however, code has not been publicly released.
Mitigation:
We request organizations to apply the latest patches from Microsoft to address CVE-2020-0610 & CVE-2020-0609.
These vulnerabilities can be exploitable via RD Gateway service listening on UDP/3391. We request organizations to disable UDP transport option or block UDP port 3391 on firewall to prevent exploitation.
Qualys customers can use QID:91596 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources:
https://github.com/ollypwn/BlueGate
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0610
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0609