Overview:
On 8 June 2020, A new vulnerability has been disclosed in public domain for Universal Plug and Play (UPnP). The vulnerability has been given a name CallStranger. Exploitation of this bug, could result into exfiltration of data, distributed denial of service (DDoS) attack or scanning your network etc.
Universal Plug and Play (UPnP) is a set of networking protocols which allows networkdevices like printers, Internet gateways, Wi-Fi access points and mobile devices to find other devices on network and establish connection for data sharing, communications, and entertainment.
POC is available on GitHub.
Description:
Vulnerability caused by Callback header value in UPnP SUBSCRIBE function can be controlled by an attacker and results into Server Side Request Forgery(SSRF) vulnerability.
To subscribe to a UPnP event, send following SUBSCRIBE request with NT and CALLBACK header fields.
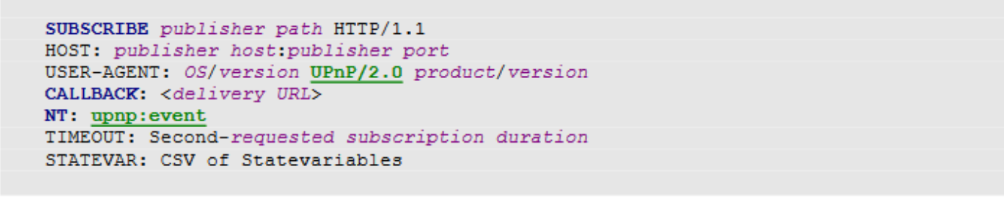
Image Source: Open Connectivity Foundation(OCF)
Where CALLBACK header contains the URL to be notified. UPnP supports multiple callback URL’s, when the service sends events, it will try these URL’s in order until one succeeds.
Attacker can use this vulnerability for,
SYN Flood:
If TCP ports of these callback URL’s are closed, large network traffic of TCP handshake with multiple SYN packets will generate and result into SYN flood attack.
PORT scanning:
In case of multiple callback URL, if TCP connection failed then it tries the next URL. Using this method attacker can easily find out which ports are open
Exfiltration of data:
HTTP does not place a limit on request line length, sender and recipient should support a limit on request line length.
Researcher Çadırcı, successfully sent 16MB data with just 1 request via Philips TV.
Billions of devices are using UPnP implementation. All these devices are vulnerable to this attack.
Affected devices: (Source: https://callstranger.com/)
- Windows 10 (All other windows and server versions may be affected) – upnphost.dll 10.0.18362.719
- Xbox One- OS Version 10.0.19041.2494
- ADB TNR-5720SX Box (TNR-5720SX/v16.4-rc-371-gf5e2289 UPnP/1.0 BH-upnpdev/2.0)
- Asus ASUS Media Streamer
- Asus Rt-N11
- Belkin WeMo
- Broadcom ADSL Modems
- Canon Canon SELPHY CP1200 Printer
- Cisco X1000 – (LINUX/2.4 UPnP/1.0 BRCM400/1.0)
- Cisco X3500 – (LINUX/2.4 UPnP/1.0 BRCM400/1.0)
- D-Link DVG-N5412SP WPS Router (OS 1.0 UPnP/1.0 Realtek/V1.3)EPSON EP, EW, XP Series (EPSON_Linux UPnP/1.0 Epson UPnP SDK/1.0)
- HP Deskjet, Photosmart, Officejet ENVY Series (POSIX, UPnP/1.0, Intel MicroStack/1.0.1347)
- Huawei HG255s Router – Firmware HG255sC163B03 (ATP UPnP Core)
- NEC AccessTechnica WR8165N Router ( OS 1.0 UPnP/1.0 Realtek/V1.3)
- Philips 2k14MTK TV – Firmware TPL161E_012.003.039.001
- Samsung UE55MU7000 TV – Firmware T-KTMDEUC-1280.5, BT – S
- Samsung MU8000 TV
- TP-Link TL-WA801ND (Linux/2.6.36, UPnP/1.0, Portable SDK for UPnP devices/1.6.19)
- Trendnet TV-IP551W (OS 1.0 UPnP/1.0 Realtek/V1.3)
- Zyxel VMG8324-B10A (LINUX/2.6 UPnP/1.0 BRCM400-UPnP/1.0)
For updated list of affected devices please check: https://callstranger.com/
Advisory:
OCF updated UPnP specification on 17.04.2020, check specification on following webpage
https://openconnectivity.org/upnp-specs/UPnP-arch-DeviceArchitecture-v2.0-20200417.pdf
Mitigations:
Qualys Threat Research Lab provides protection with the QID(s)# 45187. Kindly continue to follow on Qualys Threat Protection for more coverage on vulnerabilities.
References & Sources:
- https://github.com/yunuscadirci/CallStranger
- https://callstranger.com/
- https://openconnectivity.org/upnp-specs/UPnP-arch-DeviceArchitecture-v2.0-20200417.pdf