SAP issued a new security advisory on July 13 in their SAP Security Patch Day – July 2020 addressing ten security vulnerabilities in multiple SAP products.
Among these multiple vulnerabilities, CVE-2020-6287 is a critical vulnerability with a CVSSv3 base score 10/10. Rest other vulnerabilities are of High and Medium severity.
Description:
SAP identified several vulnerabilities in their products like SAP NetWeaver, SAP Business Client, SAP Disclosure Management, SAP Business Objects Business Intelligence Platform. Approximately 10 vulnerabilities including Cross-Site Scripting (XSS), Missing Authentication, Server-Side Request Forgery, Information Disclosure, Path Traversal and few other vulnerabilities were disclosed.
As per reports the vulnerability was discovered and reported by cloud security firm Onapsis according to which CVE-2020-6287 also known as RECON allows malicious threat actors to create an SAP user account with maximum privilege on SAP application giving the attackers full control over SAP resources. RECON bug is assigned CVSSv3 score 10 out of 10 that means the bug is probably very easy to exploit and can be automated for remote attacks that might not require the attacker to have an account on SAP app already or valid credentials. CVE-2020-6286 was identified as Path Traversal vulnerability due to insufficient input path validation of certain parameters in web service, however some of these vulnerabilities may require the tc~lm~ctc~cul~startup_app application to be enabled on target system in order to get exploited.
Other applications running the SAP NetWeaver Java technology stack are also impacted by this vulnerability. Approximately around 40,000 SAP customers are affected by RECON bug. In a scan carried out by Onapsis around 2,500 SAP systems were discovered that were directly exposed to the internet that might be vulnerable.
Here’s a detailed list of the other affected SAP products and the CVEs:
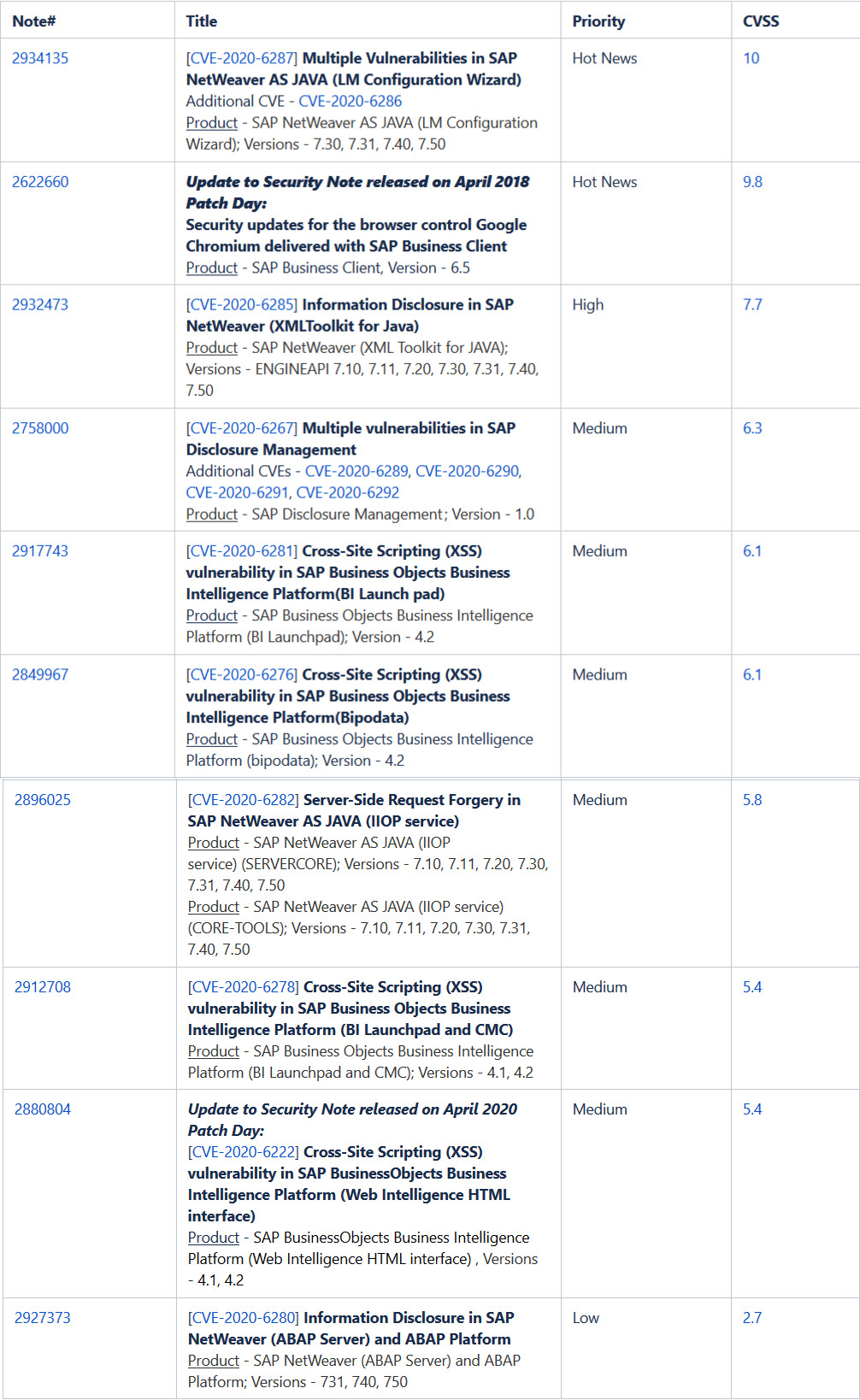
Qualys is unaware of any active exploitation of these vulnerabilities at the time of publishing the blog. However, the vulnerabilities are highly likely to have a PoC and active exploitations because patches have been publicly released, the underlying vulnerabilities could be reverse engineered to create exploits that target unpatched systems.
Affected SAP Products:
SAP NetWeaver AS JAVA
SAP Business Client
SAP Disclosure Management
SAP Business Objects Business Intelligence Platform
SAP NetWeaver (ABAP Server) and ABAP Platform
Remediation:
SAP has officially released public advisory for affected products and their patches. Customers are advised to visit the Support Portal and apply patches on a priority to remediate these vulnerabilities. Customers are also advised to prioritize patching on external facing systems followed by internal systems.
It’s highly recommended to disable the tc~lm~ctc~cul~startup_app application unless required.
Detection:
Qualys customers can scan their network with QID# 13849 to detect vulnerable SAP NetWeaver assets. Please continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References & Sources: