On June 9th 2020, Microsoft issued a security advisory addressing Elevation of Privilege vulnerability (CVE-2020-1313) in Windows Update Orchestrator Service that has a CVSS score of 7.8 and severity marked as Important.
Vulnerability Details:
Windows Update Orchestrator Service is a DCOM service which is used by other components to install windows updates that are already downloaded. Update Orchestrator Service was found vulnerable to Elevation of Privileges vulnerability due to an improper authorization of the callers. CVE-2020-1313 was discovered and reported by security researcher Imre Rad. As per the researcher, UniversalOrchestrator service implemented in usosvc.dll runs as NT_AUTHORITY\SYSTEM and it was configured with access permissions for BUILTIN\Users. Successful exploitation of this vulnerability allows attackers to run processes in an elevated context.
To exploit this vulnerability, ScheduleWork method can be used to schedule a command to be executed in the context of service without any authorization of the requestor. It requires the target executable itself digitally signed and located under C:\windows\system32 or common files in Program Files. This allows attackers to launch C:\windows\system32\cmd.exe and gain arbitrary code execution under NT_AUTHORITY\SYSTEM resulting in privilege escalation. The work created in registry is not executed instantly, it is scheduled to be executed.
Affected Products:
- Windows 10 Version 1903
- Windows 10 Version 1909
- Windows 10 Version 2004
- Windows Server core version 1903
- Windows Server core version 1909
- Windows Server core version 2004
Exploitation:
At Qualys Labs, we’ve tried to reproduce the issue, reported for CVE-2020-1313. We’ve used a publicly available PoC on github to exploit the vulnerability on a vulnerable Windows 10 version 1903 target.
The PoC configures a work with cmdLine c:\windows\system32\cmd.exe and parameters:
- /c “whoami > c:\Qualys.txt”
- /c “whoami /priv >>c:\Qualys.txt”
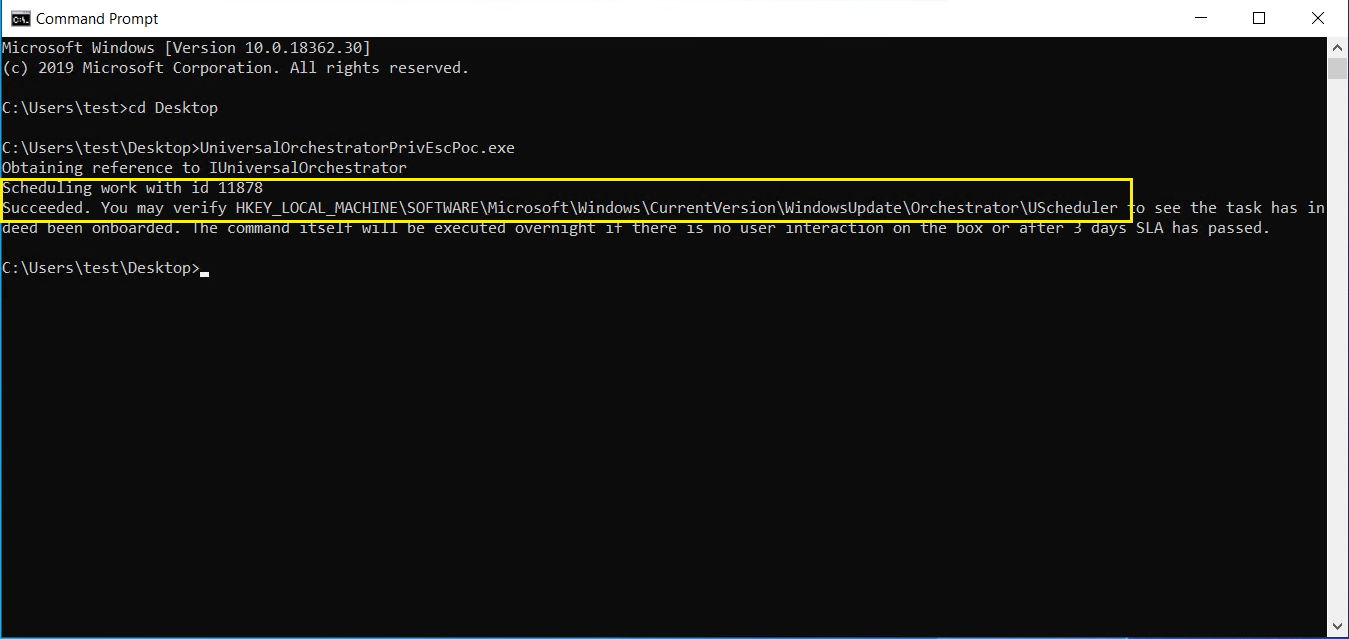
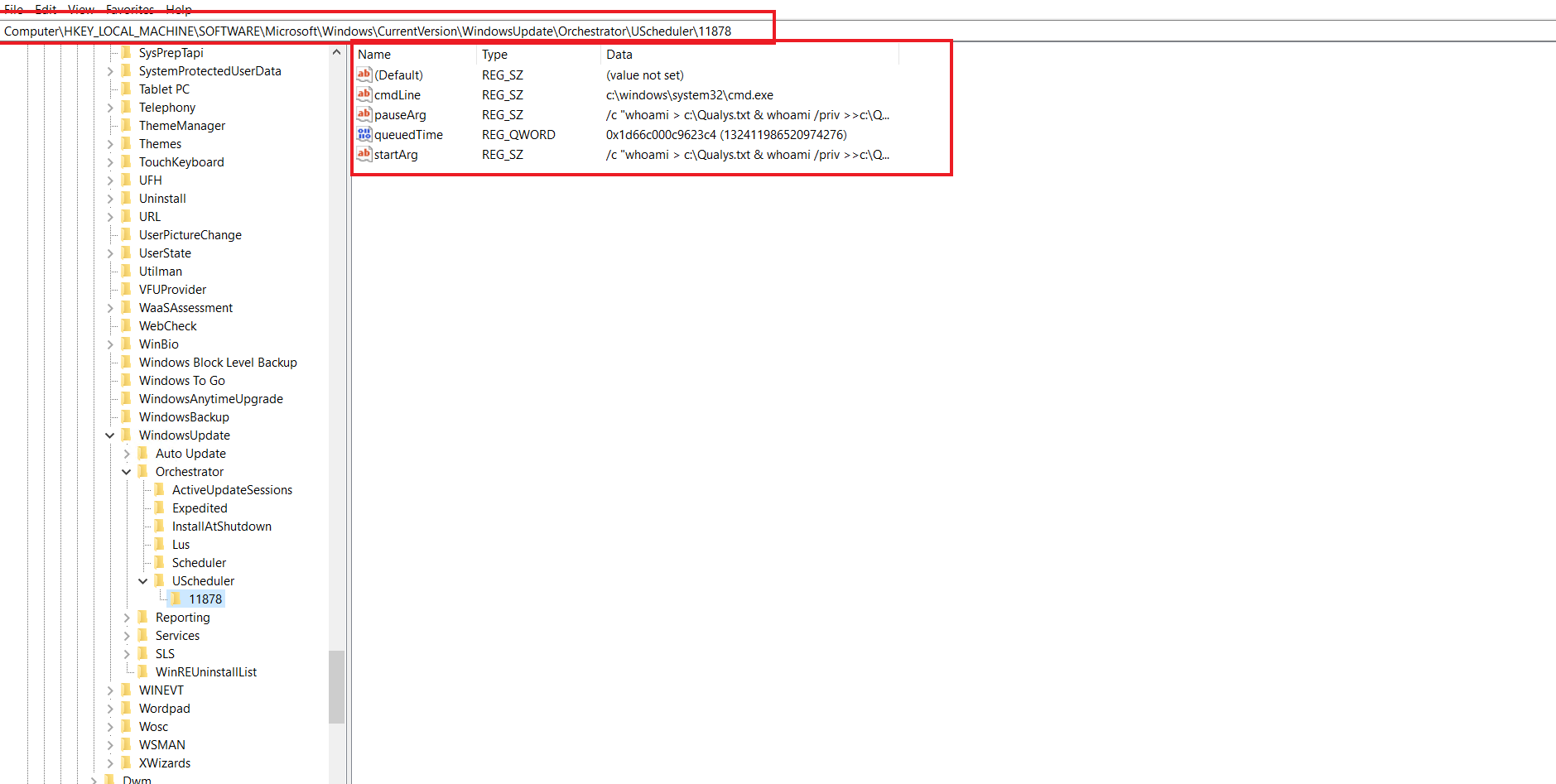
We can see a work is successfully added under registry hive HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator\UScheduler to be executed with c:\windows\system32\cmd.exe under context of NT_AUTHORITY\SYSTEM without authorization.
Microsoft has published an official advisory to address this vulnerability. Customers are recommended to patch their vulnerable assets.
Detection:
Qualys customers can scan their network with QID 91646 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1313
https://github.com/irsl/CVE-2020-1313