Overview
A critical buffer overflow vulnerability (CVE-2020-14871) was addressed in Oracle Critical Patch Update (CPU) released in October 2020. This vulnerability was present in the Pluggable authentication module, which is a component of Oracle Systems. Successful exploitation of this flaw could result in taking complete control over vulnerable systems with network access.
FireEye security researchers reported that the threat group – UNC1945 was exploiting this bug when it was a zero day, long before a patch was released. UNC1945 utilized a remote exploitation tool called “EVILSUN” to exploit this bug.
Description
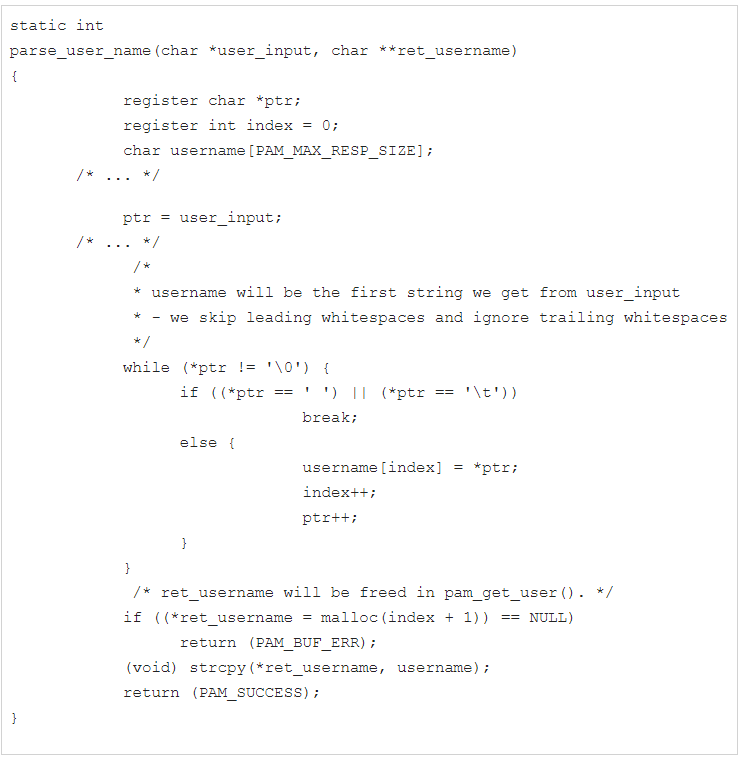
This is a stack buffer overflow vulnerability, located in the parse_user_name function of the Pluggable Authentication Modules (PAM) library. The vulnerability is triggered whenever a username longer than PAM_MAX_RESP_SIZE (512 bytes) is passed to parse_user_name.
Image Source: www.fireeye.com
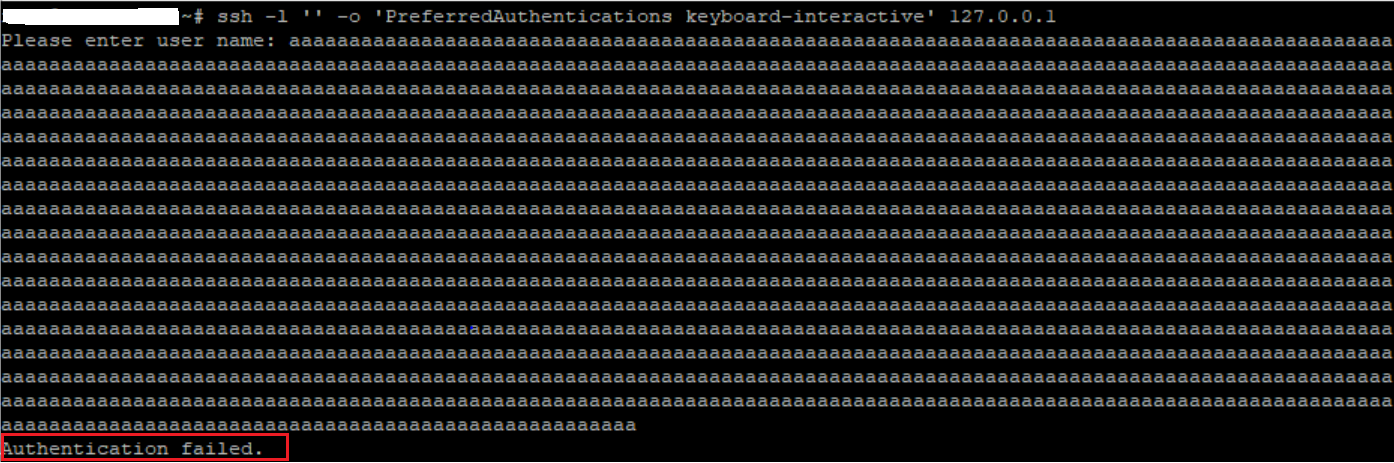
FireEye developed a POC to test this vulnerability on different versions of Oracle Solaris. Solaris is found to be vulnerable if the SSH client prints “Authentication failed”; whereas, non-vulnerable Solaris causes the SSH server to repeatedly prompt for a username, if it receives one that is too long.
Image Source: Qualys Lab
This is a trivially exploitable vulnerability that enables an attacker to take complete control over the vulnerable Oracle Solaris operating system.
Affected Operating Systems
Oracle Solaris 10 and 11.
Qualys Detection
Qualys customers can scan their network with QIDs 296047 and 296046 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
Workaround
It is recommended to apply the following workaround:
- Editing the /etc/ssh/sshd_config file to add the lines ChallengeResponseAuthentication no and KbdInteractiveAuthentication no and restart the SSH server.
This workaround will remove the opportunity to exploit the vulnerability using SSH Keyboard-Interactive authentication. There may be other ways to attack the parse_user_name function; however, and it is recommended that users apply this workaround only as a stopgap until Solaris 9 systems can be upgraded, or until the October patch is installed on the supported Solaris versions.
Workaround/Mitigation Detection
Qualys Policy Compliance customers can evaluate workaround based on following Controls
- 5276 Status of the ‘KbdInteractiveAuthentication’ setting in the ‘/etc/ssh/sshd_config’ file
- 5365 Status of the ‘ChallengeResponseAuthentication’ setting in the ‘/etc/ssh/sshd_config’ file
References
- oracle.com/security-alerts/cpuoct2020.html
- https://www.fireeye.com/blog/threat-research/2020/11/live-off-the-land-an-overview-of-unc1945.html
- https://www.fireeye.com/blog/threat-research/2020/11/critical-buffer-overflow-vulnerability-in-solaris-can-allow-remote-takeover.html