Overview
Recently, SaltStack announced three severely critical bugs and has recommended users to prioritize and immediately apply the appropriate patches.
Let’s understand all three bugs one by one:
CVE-2020-16846 – If SSH client is enabled, sending crafted requests to Salt API results in shell injection. Thus, a client with network access to SaltStack Salt API can inject code remotely without authentication.
CVE-2020-25592 – Authentication can be bypassed due to improper validation of eauth tokens and credentials. While using Salt via SSH, authentication can be bypassed by giving any value to the “token” that grants the permission to access Salt remotely.
CVE-2020-17490 – This is a low-severity vulnerability as it involves lax assessment of key validity. Weak file permissions observed in the TLS module while creating certificated within SaltStack Salt through 3002. “This CVE affects any Minions or Masters that previously used the create_ca, create_csr, and create_self_signed_cert functions in the TLS module,” reads the November 3rd advisory.
Below image is a Github page for SaltStack commits. It clearly shows that the option of “shell-True” when calling “subprocess.call” was removed to prevent shell injection when SSH client in enabled on SaltStack framework.
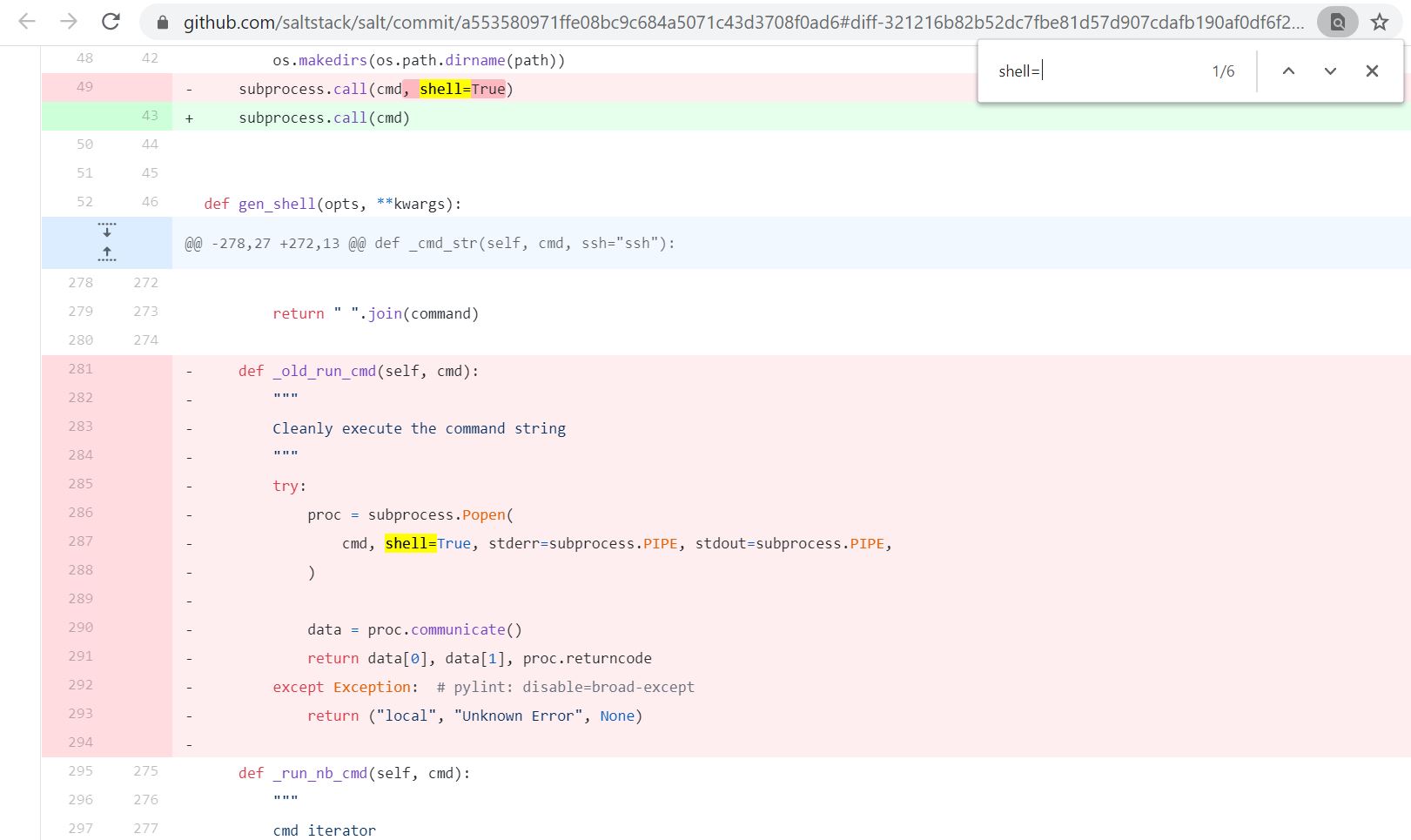
Image Source: Github
At the time of this blog being created, a simple string search on Shodan showed that over 6000 Salt-master were available, majorly running in the United States.
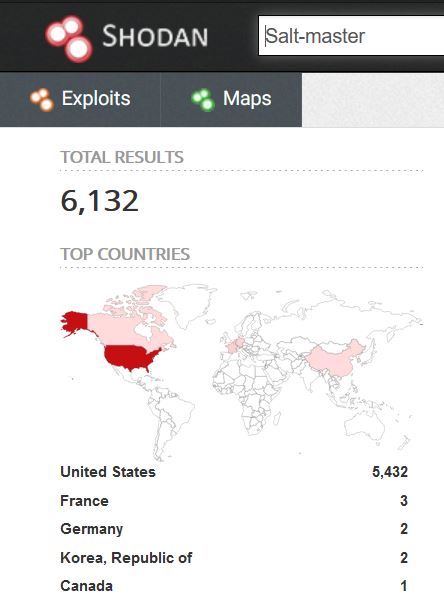
Image Source: Shodan
No POC was published in the wild, nor were any active attacks observed while this blog was being published.
Affected SaltStack Versions
SaltStack Salt through 3002.
Mitigation
SaltStack recommends updating the patch as early as possible. Apart from patching, SaltStack recommends some tips and tricks to harden Salt framework in the article – Hardening Salt.
Qualys Detection
Qualys customers can scan their network with QIDs 373917 and 373916 to detect vulnerable assets. Kindly continue to follow Qualys Threat Protection for more coverage on these vulnerabilities.
References
https://docs.saltstack.com/en/latest/topics/hardening.html#general-hardening-tips
https://www.saltstack.com/blog/on-november-3-2020-saltstack-publicly-disclosed-three-new-cves/
https://www.theregister.com/2020/11/04/saltstack_security/?&web_view=true
https://gitlab.com/saltstack/open/salt-patches
https://gitlab.com/saltstack/open/salt-patches/-/blob/master/patches/2020/09/02/README.md
https://gitlab.com/saltstack/open/salt-patches/-/blob/master/patches/2020/09/25/README.md