On December 23rd, 2020, Zyxel published an advisory for a hardcoded credential vulnerability. More than 100,000 Zyxel firewalls, access point controllers and VPN gateways are prone to this vulnerability.
Vulnerability Details
Zyxel firewalls and AP controllers contain hardcoded admin-level backdoor account, which can grant attackers root access to devices via either the SSH interface or the web administration panel.
According to the Zyxel Security Advisory,
“A hardcoded credential vulnerability was identified in the “zyfwp” user account in some Zyxel firewalls and AP controllers. The account was designed to deliver automatic firmware updates to connected access points through FTP.”
The vulnerability was reported to Zyxel by Niels Teusink, security researcher at EYE . Researcher also published a technical report on Undocumented user account in Zyxel products (CVE-2020-29583).
Explaining the seriousness of the vulnerability, the researcher said
“As the zyfwp user has admin privileges, this is a serious vulnerability. An attacker could completely compromise the confidentiality, integrity and availability of the device. Someone could for example change firewall settings to allow or block certain traffic. They could also intercept traffic or create VPN accounts to gain access to the network behind the device. Combined with a vulnerability like Zerologon this could be devastating to small and medium businesses.”
Password for this undocumented user account is easy to discover, it is available in one of the binaries on the system in plaintext format. However, the researcher did not publish the password in his initial report as the vulnerability is easy to exploit.
Some other researchers have disclosed the password ‘PrOw!aN_fXp’ for undocumented user account ‘zyfwp’.
Affected Versions
Firewalls
- Advanced Threat Protection (ATP) series running firmware ZLD V4.60
- Unified Security Gateway (USG) series running firmware ZLD V4.60
- USG FLEX series running firmware ZLD V4.60
AP controllers
- NXC2500
- NXC5500
The ATP, USG, USG FLEX and VPN firewalls running firmware versions earlier than ZLD V4.60 and the VPN series running the SD-OS are NOT affected.
Mitigation
Patches are currently available only for the ATP, USG, USG Flex, and VPN series.
- ZLD V4.60 Patch1 for Firewalls
- V6.10 Patch1 for AP controllers
Patches for the NXC series are expected in April 2021.
PoC
Security Researchers were provided the details of undocumented user account in their report.
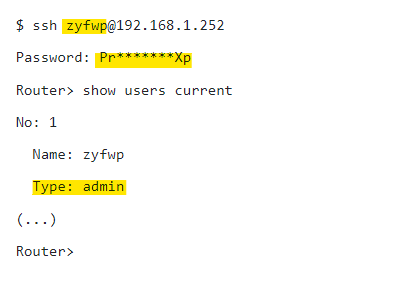
Detection
Qualys customers can scan their network with QID 374803 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://www.zyxel.com/support/CVE-2020-29583.shtml
https://www.eyecontrol.nl/blog/undocumented-user-account-in-zyxel-products.html