Microsoft has released patches for the four zero-days exploited in the attacks (CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065), discovered during the subsequent investigation. These bugs were observed by Microsoft Threat Intelligence Center (MSTIC) since January 2021. The OS giant, said that Hafnium operators used the four Exchange zero-days as part of a multi-part attack chain to bypass authentication procedures, gain admin privileges, and then install an ASPX web shell on the compromised servers.
Microsoft is providing the following details to help our customers understand the techniques used by HAFNIUM to exploit these vulnerabilities and enable more effective defense against any future attacks against unpatched systems. Active attacks have been observed in the wild.
- CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server. The Indicator of Compromise (IOCs) for CVE-2021-26855:
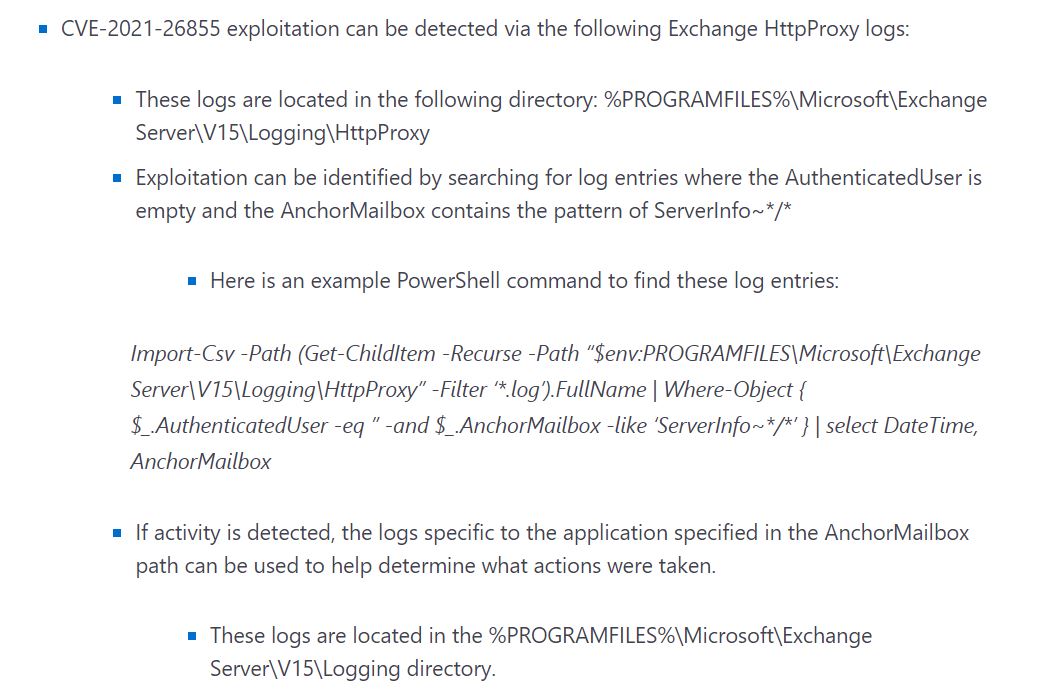
Image Source: Microsoft
- CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit. IOCs for CVE-2021-26857:
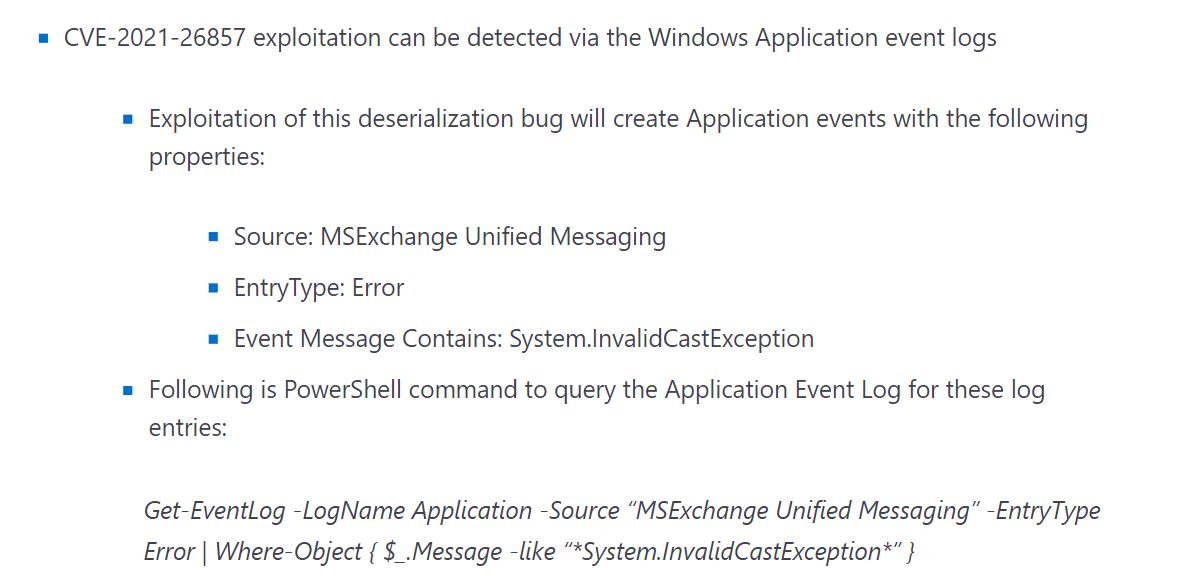
Image Source: Microsoft
- CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
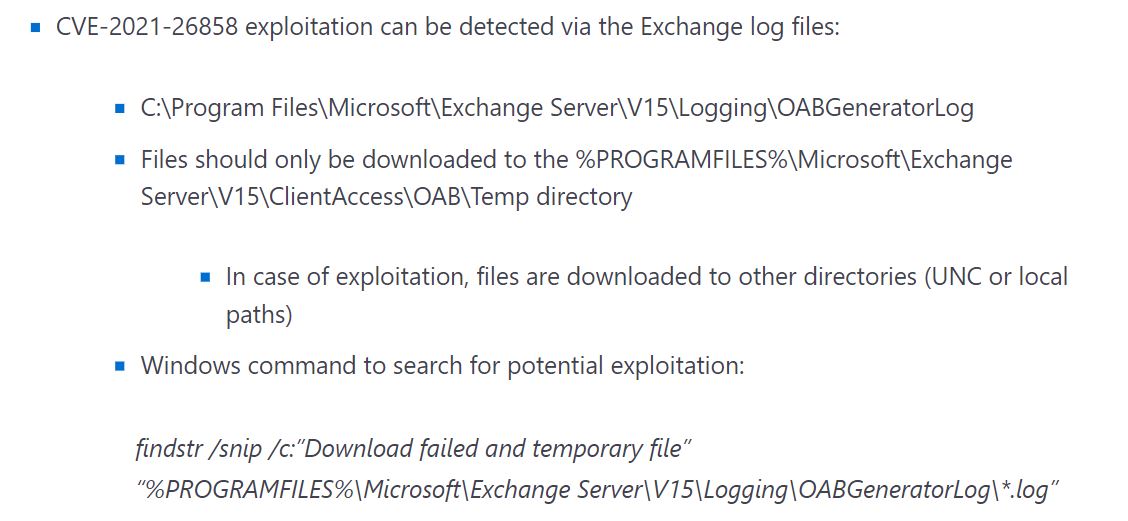
Image Source: Microsoft
- CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
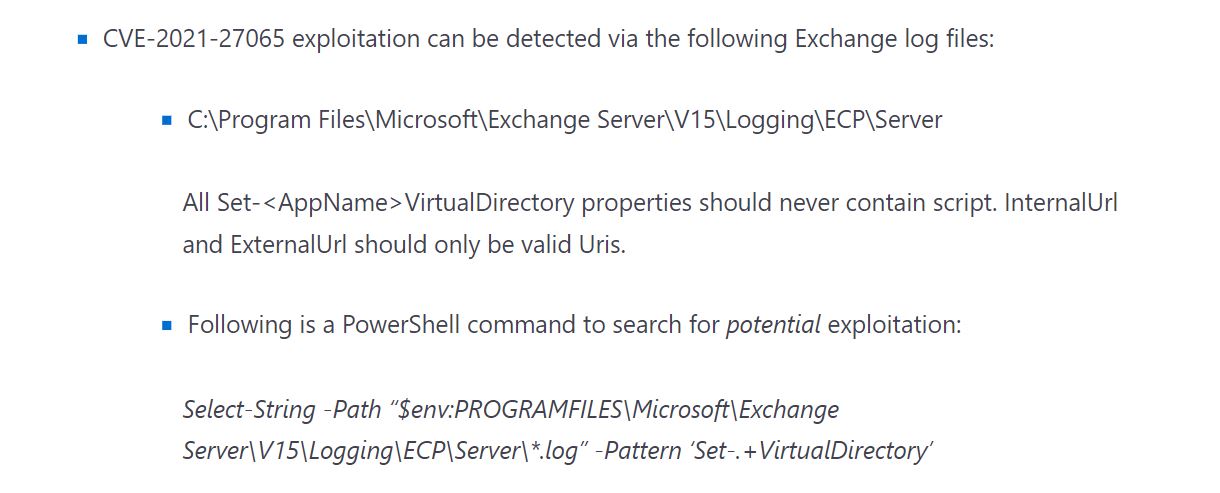
Image Source: Microsoft
Some of the common web shells disclosed by Microsoft:
– web.aspx
– help.aspx
– document.aspx
– errorEE.aspx
– errorEEE.aspx
– errorEW.aspx
– errorFF.aspx
– healthcheck.aspx
– aspnet_www.aspx
– aspnet_client.aspx
– xx.aspx
– shell.aspx
– aspnet_iisstart.aspx
– one.aspx
Check for suspicious .zip, .rar, and .7z files in C:\ProgramData\, which may indicate possible data exfiltration.
As per the OS giant, Microsoft Threat Intelligence Center (MSTIC) attributes this campaign with high confidence to HAFNIUM, a group assessed to be state-sponsored and operating out of China, based on observed victimology, tactics, and procedures. The details of which can be studied more at hafnium-targeting-exchange-servers.
Mitigation
Microsoft recommend prioritizing installing updates on Exchange Servers that are externally facing. Install Patches for Exchange 2010, 2013, 2016, and 2019 ASAP. This vulnerability is part of an attack chain. The initial attack requires the ability to make an untrusted connection to Exchange server port 443.
- Exchange Server 2010 (RU 31 for Service Pack 3). This is an out-of-band update for an unsupported server to ensure that organizations have defense in depth.
- Exchange Server 2013 (CU 23).
- Exchange Server 2016 (CU 19, CU 18).
- Exchange Server 2019 (CU 8, CU 7).
NOTE: Exchange Online is not affected.
Qualys Detection
Qualys customers can scan their network with QID 50107 to detect vulnerable assets. Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26857
https://www.microsoft.com/security/blog/2020/06/24/defending-exchange-servers-under-attack/
https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
https://therecord.media/chinese-apt-targeted-exchange-servers-with-four-zero-days-microsoft-says/
https://blogs.microsoft.com/on-the-issues/2021/03/02/new-nation-state-cyberattacks/