Microsoft has released a patch for a highly severe Exchange Server vulnerability in its November 2021 Patch Tuesday. This vulnerability can allow authenticated attackers to execute codes remotely on vulnerable servers.
The CVE-2021-42321 security issue is caused by inappropriate validation of command-let (cmdlet) parameters. To execute this vulnerability, the attacker needs to be authenticated. This vulnerability only affects on-premises Microsoft Exchange servers, including those used by users in Exchange Hybrid mode. (Exchange Online clients are safe and no user actions are needed.
Use the newest version of the Exchange Server Health Checker script to quickly inventory any of the Exchange servers in your environment that do not have the latest updates (CUs and SUs).
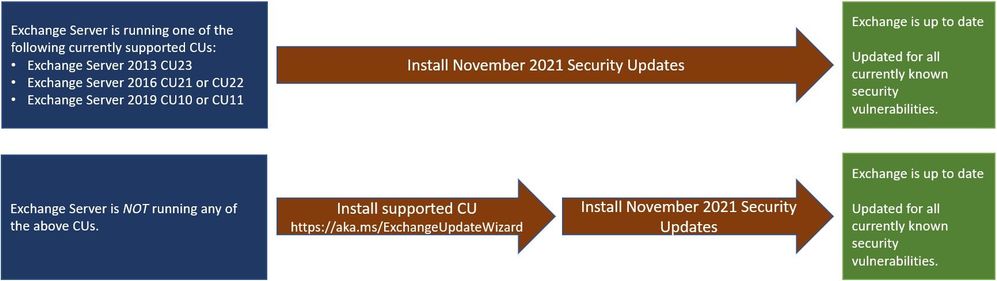 Image source: Microsoft
Image source: Microsoft
Microsoft Exchange Emergency Mitigation (EM) is a new Exchange Server feature released in September 2021. This feature provides automated security for vulnerable Exchange servers.
It is accomplished by automatically applying interim mitigations for high-risk security issues to protect on-premises systems from incoming attacks, while also giving administrators more time to install security upgrades.
Affected on-premises Exchange servers
Exchange administrators have been dealing with two significant waves of assaults targeting the ProxyLogon and ProxyShell vulnerabilities since the beginning of 2021.
Multiple state-backed and financially motivated threat actors have been using ProxyLogon exploits to deploy web shells, cryptominers, ransomware, and other malware against over a quarter of a million Microsoft Exchange servers belonging to tens of thousands of organizations around the world since early March.
Affected versions
The CVE-2021-42321 security issue affects Exchange Server 2016 and Exchange Server 2019.
Mitigation
Customers are advised to refer to the Microsoft Advisory for information about this vulnerability.
Qualys Detection
Qualys customers can scan their devices with QID 50116 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://support.microsoft.com/help/5007409
https://www.helpnetsecurity.com/2021/11/09/cve-2021-42321-cve-2021-42292/
https://www.bleepingcomputer.com/news/microsoft/microsoft-urges-exchange-admins-to-patch-bug-exploited-in-the-wild/
https://techcommunity.microsoft.com/t5/exchange-team-blog/released-november-2021-exchange-server-security-updates/ba-p/2933169