Introduction:
The success of an exploit kit depends on many parameters infecting effective targets, avoiding honeypots, sandboxes and researchers who are always on the lookout for new exploit kits and expose it to world. An exploit kit that is stealthy will have a longer life time and gains more reputation. This is reflected in an EK’s capability to fingerprint targets and determine which exploit to serve and importantly try to check if the machine is bait.
A normal users machine is probably not packed with analysis tools, but someone who is in the business of analyzing exploits, vulnerabilities, malware etc. tend to use certain tools of the trade like Wireshark, Fiddler, Sysinternal suite and many more. The EK tries to detect the presence of these tools and evades them. EK could use browser vulnerabilities to leak information about the files on the target machines. Two such vulnerabilities were discovered in the wild and disclosed by Proofpoint – CVE-2016-3351 and CVE-2016-3298. Both of which have been patched by Microsoft in September and October 2016 respectively. Both these exploit were seen as part of malvertising campaigns leading to Angler EK landing page.
Vulnerability:
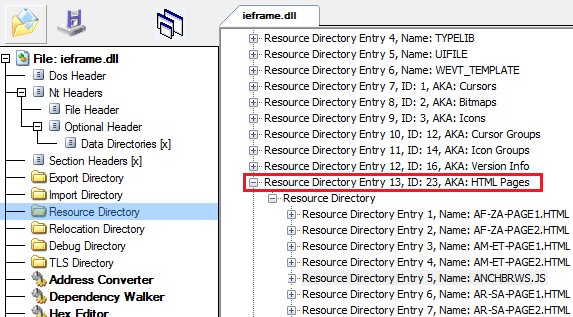
CVE-2016-3351 uses MIME type checks to discover if certain file associations are linked to particular programs like .pcap associated with Wireshark, .saz file to Fiddler etc. more information about this can be found here. On the other hand, CVE-2016-3298 exploits the res protocol to detect files on the machine. In this article we will be taking a closer look at CVE-2016-3298. The gist of the vulnerability is that the res protocol can be used to load resources from the local machine, to be more specific it loads from the resource section (.rsrc) of a PE file. In the Windows universe it is the standard binary file format for an Executable or DLL . The image below shows the resource section of ieframe.dll. Each entry in the resource section has a pre-defined type, which describes what kind of resource it is. For e.g. in the image below type 23 means HTML resources, consisting of the built-in html pages.
The official name for the res protocol is Microsoft HTML Resource pluggable protocol, it is a URL protocol meaning its functionality is accessed via special crafted url e.g. res://<path>. A pluggable protocol is one of the many ways windows extends the functionality of Internet explorer. There are two basic types, Asynchronous Pluggable Protocols & Application Protocols. An application protocol enables Internet Explorer to launch the corresponding application and passes the URL as input to the application e.g. res,file etc.
Exploit:
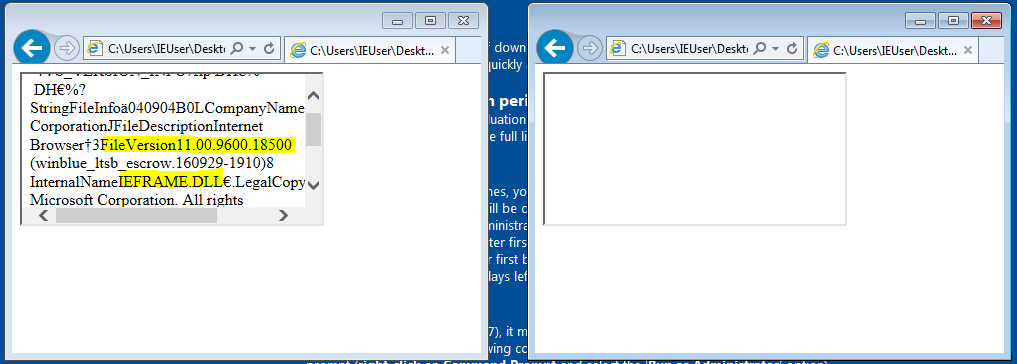
To exploit this vulnerability, we will try to load the resource in an iframe and check for the corresponding iframe event to fire. A minimal PoC demonstrates the exploit. In the image below we are loading the file version resource from the calculator executable in to an iframe.
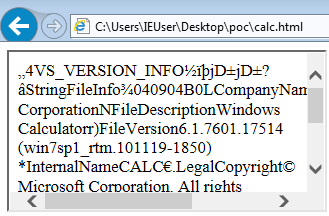
In practical cases the iframe itself will may not be visible or is has abnormal dimensions, the EK could serve the exploit based on the result of the res URL. As mentioned before the resources have a predefined type for the resource. File version (RT_VERSION) is a frequently used value. A sample request may look like “res://C:\\windows\\system32\\calc.exe/16/1”.
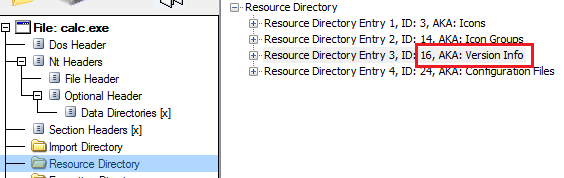
Notice the ’16’ in the mage above and the sample request. This field will exist for all legitimate files like .exe, .dll, .sys etc. on a windows machine. An EK could query for dll versions for fingerprinting. This vulnerability was actively exploited in the ‘GooNky’ malvertising campaign, which checked for ‘invguestie.dll. Furthermore, the AdGholas campaign checked for file version of driver ‘pci.sys’ in different drives. Microsoft has patched this vulnerability in October 2016 after which the res protocol can load resources only from ieframe.dll.
Conclusion:
Enumerating application and files on the targets increases the chance of infecting said targets by an exploit kit and evading honeypots, sandboxes , AV products etc. increases the stealth factor, which in return increases the lifetime and financial gains earned through the exploit kit. Though these exploits do not affect the integrity of the system on their own, they could however lead to complete system compromise when bundled with a sophisticated EK. We request our customers to scan their network with QID 91284, 100297. Vista and Windows Server 2008 require both 3191492 and 3193515 to resolve this vulnerability.
References:
Massive AdGholas Malvertising Campaigns Use Steganography and File Whitelisting to Hide in Plain Sight
CVE-2016-3298
MS16-118: Cumulative security update for Internet Explorer
MS16-126: Security update for Microsoft Internet Messaging API