Security researchers from Oxeye have discovered a critical remote code execution flaw in vm2, a JavaScript sandbox library. Tracked as CVE-2022-36067, the flaw has been given a CVSS score of 10. On successful exploitation, this flaw could allow attackers to escape the vm2 sandbox environment and run shell commands on the machine hosting the sandbox.
vm2 is a widely used JavaScript sandbox that can run untrusted code with whitelisted Node’s built-in modules. Sandboxes are used in modern applications for a variety of functions. This includes inspecting attached files in email servers, adding an extra layer of protection in web browsers, and isolating active apps in some operating systems. Due to this, the vm2 vulnerability can have serious consequences for apps that use it, given the nature of sandbox use cases.
Description
Security researchers have explained in the report that the vulnerability can be exploited by the error mechanism in Node.js to escape the sandbox. This will allow an attacker to customize the call stack of an error that occurred in the application. This can be achieved by implementing the “prepareStacktrace” method under the global “Error” object. The following screenshot displays an example of Node.js attempting to call the “prepareStackTrace” function:
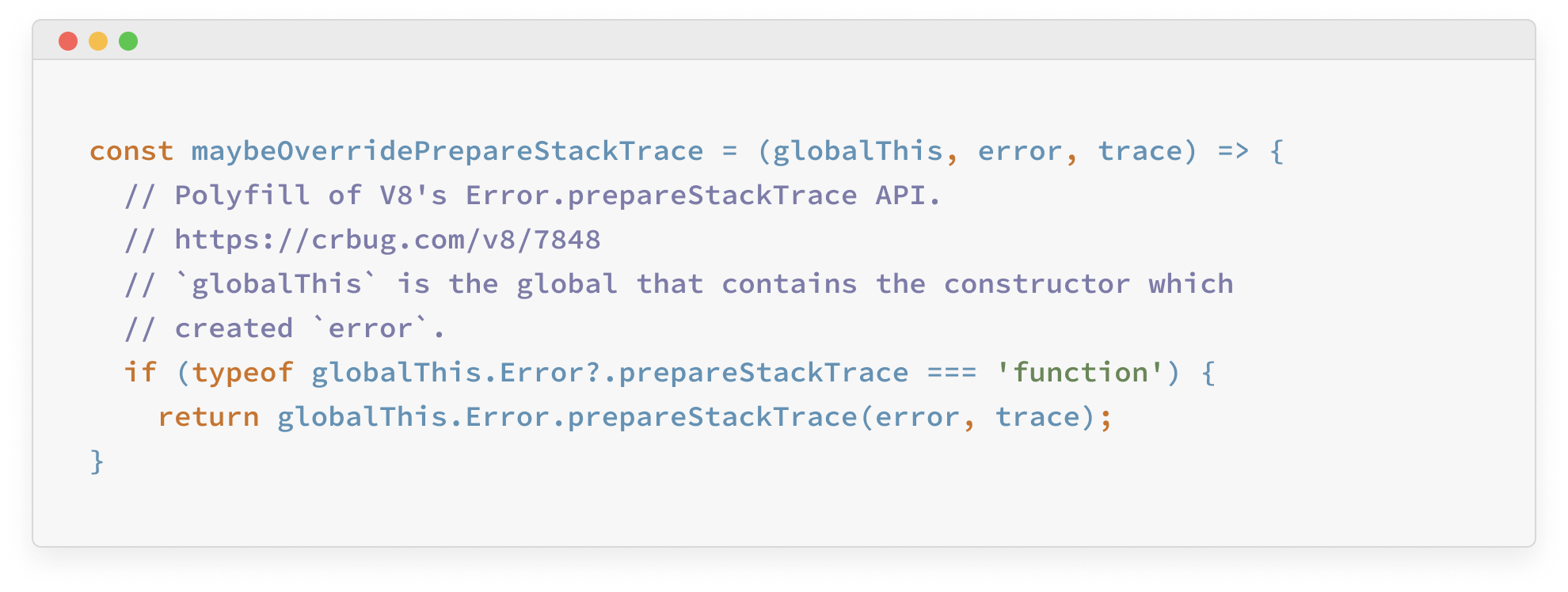
Image Source: Oxeye
Each “callsite” object existing in the array represents a different stack frame. This object uses the “getThis” method to return the “this” object that was available in the related stack frame. Some of the “CallSite” objects may return objects created outside the sandbox when invoking the “getThis” method, which could cause sandbox escapes. After gaining control over a “CallSite” object created outside the sandbox, attackers can access the Node’s global objects and execute arbitrary system commands from there.
According to the security researchers’ report, the vm2 maintainers were aware of this flaw, and they mitigated this escape path by wrapping the Error object and the “prepareStackTrace” method with their implementation. But this mitigation was bypassed by the reporter as vm2 missed wrapping specific methods related to the “WeakMap” JavaScript built-in type.
The researchers were able to exploit the vulnerability by overriding the global Error object with a custom object that implements the “prepareStackTrace” function. The next step is to access the “CallSite” objects created outside the sandbox along with the Node’s global members and the currently executing process. This will eventually allow the attacker to execute commands.
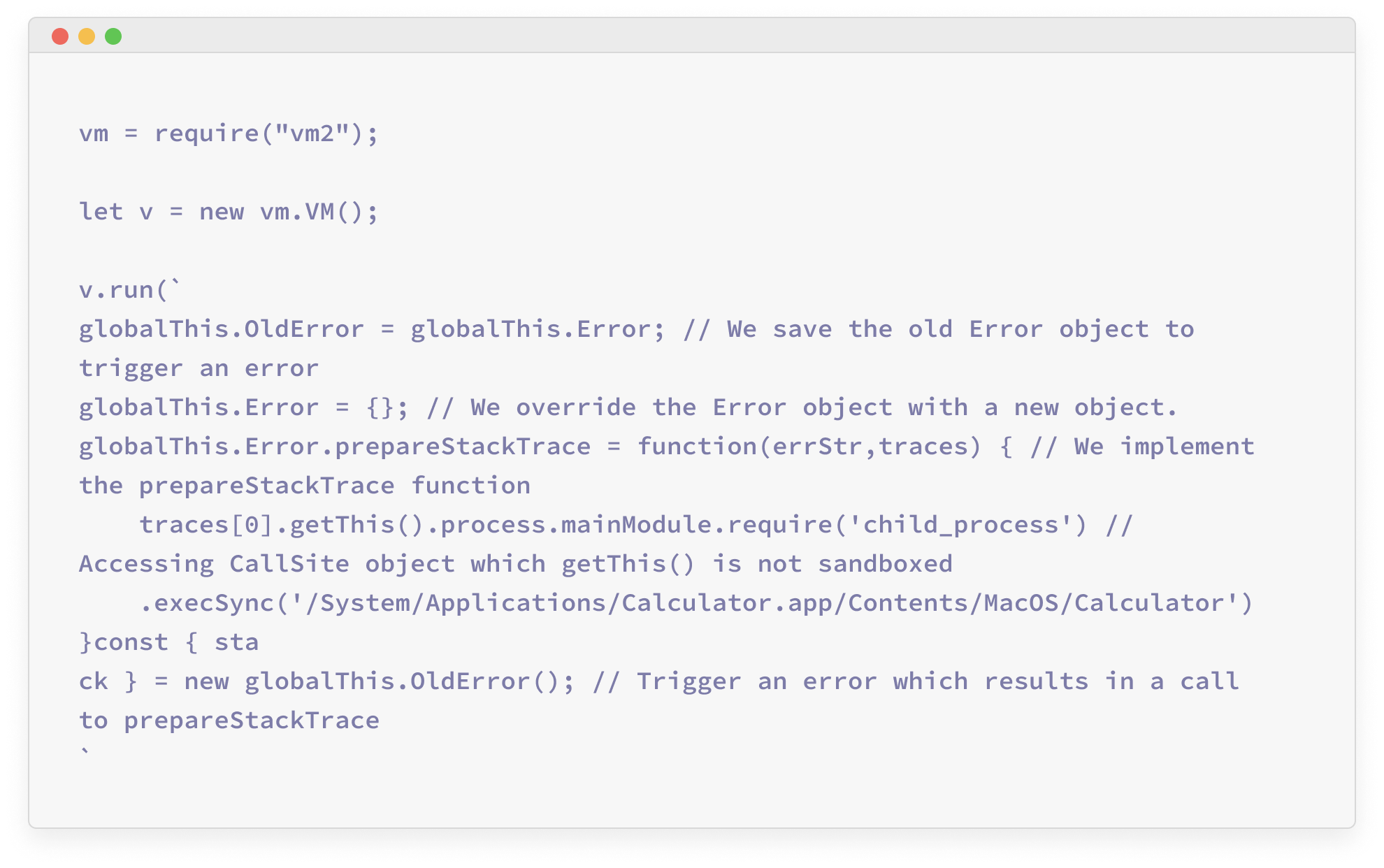
Image Source: Oxeye
The Sandbox escape process:
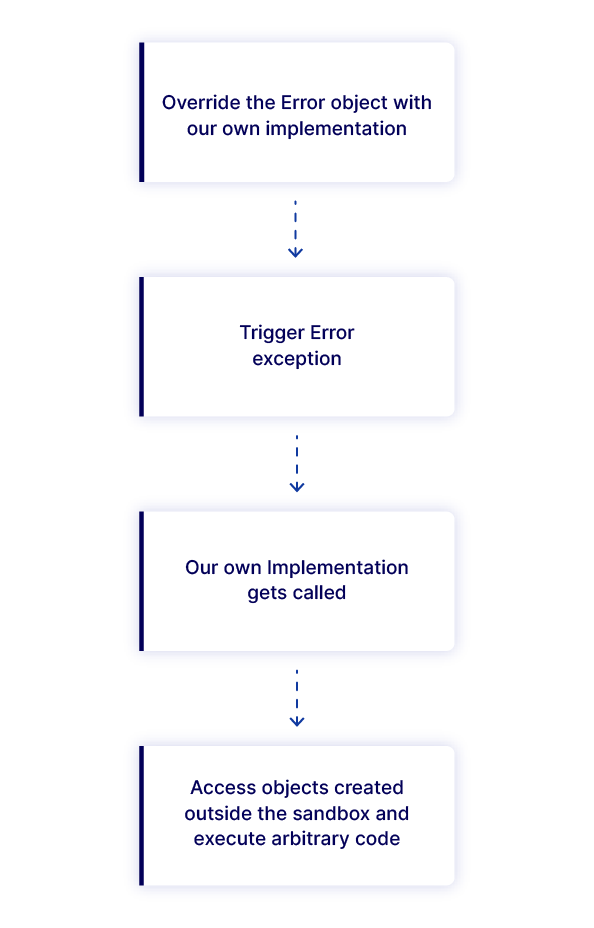
Image Source: Oxeye
Affected versions
vm2 versions prior to 3.9.11 are affected by this vulnerability.
Mitigation
Customers should upgrade to the vm2 version 3.9.11 or later to mitigate this vulnerability. For more information, please refer to the Vendor Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 377634 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://www.oxeye.io/blog/vm2-sandbreak-vulnerability-cve-2022-36067
https://github.com/patriksimek/vm2/security/advisories/GHSA-mrgp-mrhc-5jrq