Zyxel has released patches to address five vulnerabilities in two NAS products that have reached end-of-vulnerability-support. Successful exploitation of the vulnerabilities may result in command injection and remote code execution. The vulnerabilities have been given medium and critical severity ratings. Timothy Hjort from Outpost24 has discovered and reported the vulnerabilities to Zyxel. The security researcher published a write-up with the proof-of-concept exploit code.
NAS is Zyxel’s cloud storage series, which provides expanded disk space for all networking devices. These cloud-enabled products allow access to data anytime, anywhere, and on any device.
A quick search revealed more than 30,000 targets on Fofa at the time of writing.
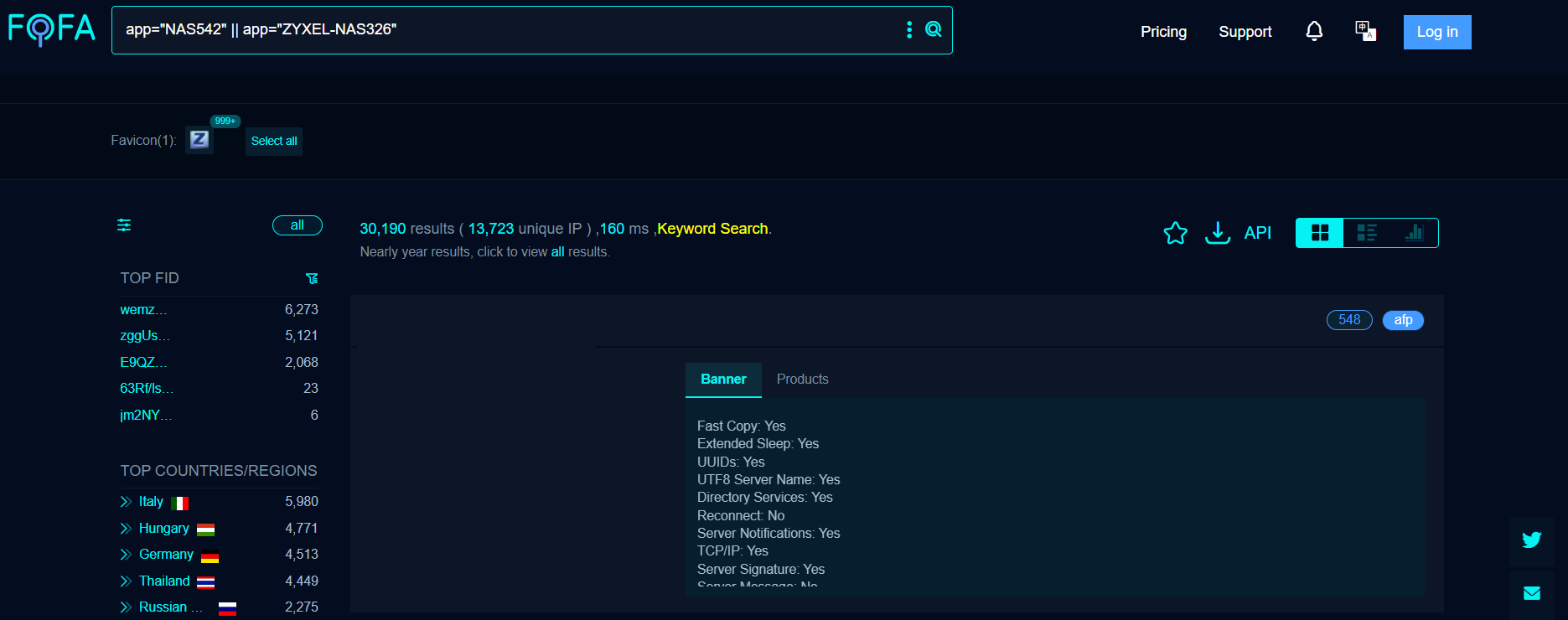 Image Source: Fofa
Image Source: Fofa
CVE-2024-29972
The vulnerability is given critical severity with a CVSS score of 9.8. The command injection vulnerability exists in the CGI program remote_help-cgi in Zyxel NAS326 and NAS542 devices. An unauthenticated attacker may exploit the vulnerability by sending a crafted HTTP POST request. An attacker may execute some operating system (OS) commands on successful exploitation.
CVE-2024-29973
The vulnerability is given critical severity with a CVSS score of 9.8. The command injection vulnerability exists in the setCookie parameter in Zyxel NAS326 and NAS542 devices. An unauthenticated attacker may exploit the vulnerability by sending a crafted HTTP POST request. An attacker may execute some operating system (OS) commands on successful exploitation.
Some exploitation attempts have been linked to a Mirai-like botnet, a notorious malware family that hijacks vulnerable devices to create massive botnets. These botnets are often used to launch distributed denial-of-service attacks.
CVE-2024-29974
The vulnerability is given critical severity with a CVSS score of 9.8. The remote code execution vulnerability exists in the CGI program file_upload-cgi in Zyxel NAS326 and NAS542 devices. An unauthenticated attacker may exploit the vulnerability to execute arbitrary code by uploading a crafted configuration file to a vulnerable device.
CVE-2024-29975
The improper privilege management vulnerability exists in the SUID executable binary in Zyxel NAS326 and NAS542 devices. An authenticated local attacker with administrator privileges may exploit the vulnerability to execute some system commands as the “root” user on a vulnerable device.
CVE-2024-29976
The improper privilege management vulnerability exists in the command show_allsessions in Zyxel NAS326 and NAS542 devices. The vulnerability may allow an authenticated attacker to obtain a logged-in administrator’s session information containing cookies on an affected device.
The Qualys Threat Research Unit was able to reproduce and verify the vulnerabilities.
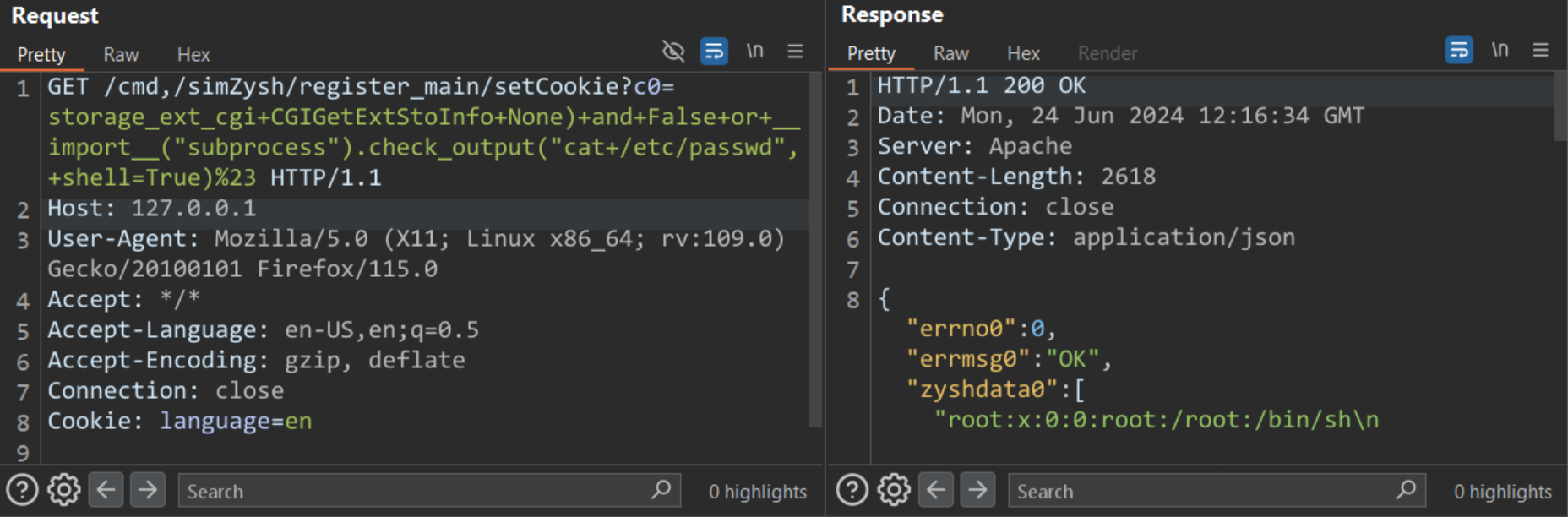 Image Source: Qualys Threat Research Unit (TRU)
Image Source: Qualys Threat Research Unit (TRU)
Affected and Patched Versions
| Affected model | Affected version | Patch availability |
| NAS326 | V5.21(AAZF.16)C0 and earlier | V5.21(AAZF.17)C0 |
| NAS542 | V5.21(ABAG.13)C0 and earlier | V5.21(ABAG.14)C0 |
For more information, please refer to the official Zyxel Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 731597 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://outpost24.com/blog/zyxel-nas-critical-vulnerabilities/
https://www.zyxel.com/global/en/support/security-advisories/zyxel-security-advisory-for-multiple-vulnerabilities-in-nas-products-06-04-2024
