Progress Software has released patches to address a critical severity vulnerability impacting MOVEit File Transfer. Tracked as CVE-2024-5806, the vulnerability has a CVSS score of 9.1.
This is an improper authentication vulnerability that exists in the SFTP module of the MOVEit Transfer. Successful exploitation of the vulnerability may lead to an authentication bypass.
MOVEit Transfer is a managed file transfer (MFT) solution available in an on-premises solution. It offers file encryption security, activity tracking, tamper-evident logging, centralized access controls, and ensuring management and control. The tool provides smooth file transfer between business partners and customers using SFTP, SCP, and HTTP-based uploads. It is compatible with SLAs, internal governance requirements, and regulations like PCI, HIPAA, CCPA/CPRA, and GDPR.
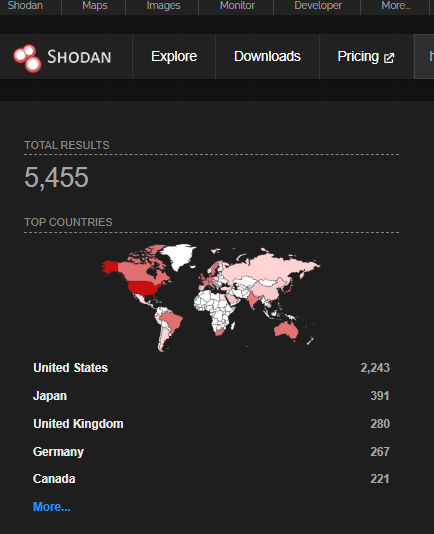
A quick search revealed more than 5,000 targets on Shodan at the time of writing.
Vulnerability Analysis
The vulnerability arises due to MOVEit’s implementation of SSH key pair authentication. Using SSH keys to authenticate is a common practice and is also recommended by security experts. The SSH public key passed by the attacker or client is processed without authentication. This allows an attacker to control the SSH key without passing legitimate credentials.
If an attacker passes a file path instead of an SSH key, the application tries to access the path. This vulnerability leads to the following two attack scenarios:
- Forced Authentication
An attacker with a valid username can pass the path to a remote SMB server and capture the NTLM hash for the moveitsvc using a responder. However, sending a file path instead of an SSH key violates SSH protocol, and no SSH library would allow this in default settings. On passing a path to a remote SMB server, the MOVEit application connects back to the SMB server, and the responder can capture the NTLM hash. An attacker can use cracking software like John the Ripper or Hashcat to crack the NTLM hash.
- Assuming the identity of arbitrary users
When trying to connect to an SSH server via key pair, the client must provide the user with a private SSH key. The public key pair to the private key is stored on the server in the user’s home directory. When connecting to an SSH server with a private key, the server verifies if the signature of the private key is correct and the private key is the legitimate pair to the user’s public key.
As this can be tough to implement, MOVEit uses a third-party library called IPWorks SSH. The library is responsible for the complex implementation of SSH authentication, while MOVEit handles user management.
An attacker with permission to upload files to the MOVEit server can upload his public key to the server’s filesystem. This allows the attacker to pass a file name instead of a public key, which, when read by IPWorks, passes an empty string to MOVEit, allowing the attacker to authenticate. This allows a user who can upload files to upload a public key and authenticate to the server, enabling full read, write, and delete access to the user.
- Fileless exploitation
Instead of an attacker uploading the public key via the MOVEit interface, one can pass the SSH key in an HTTP request, and the key is logged into the system logs. Once logged in to the system logs, the attacker can pass the path to these logs, allowing them to authenticate without uploading the public key. The security researchers at watchtower Labs exploited the flaw and uploaded their public key in the logs by passing the key in PPK format via an HTTP POST request.
Affected Versions
- From v2023.0.0 before v2023.0.11
- From v2023.1.0 before v2023.1.6
- From v2024.0.0 before v2024.0.2
Mitigation
Customers must upgrade to the following versions to patch the vulnerability:
- MOVEit Transfer 2023.0.11
- MOVEit Transfer 2023.1.6
- MOVEit Transfer 2024.0.2
NOTE: Customers must only upgrade to a patched release using the full installer.
For more information, please refer to the MOVEit Transfer Security Alert Bulletin.
Qualys Detection
Qualys customers can scan their devices with QID 379959 to detect vulnerable assets and QID 152013 to detect vulnerable web applications.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
