Kibana, a data visualization tool, released a patch to address a critical severity flaw that may allow an attacker to perform arbitrary code execution on target systems. Tracked as CVE-2024-37287, the vulnerability has a CVSS score of 9.9.
Based on searches using Fofa, we have identified over two hundred ninety-eight thousand potentially vulnerable Kibana instances exposed to the Internet at the time of writing.
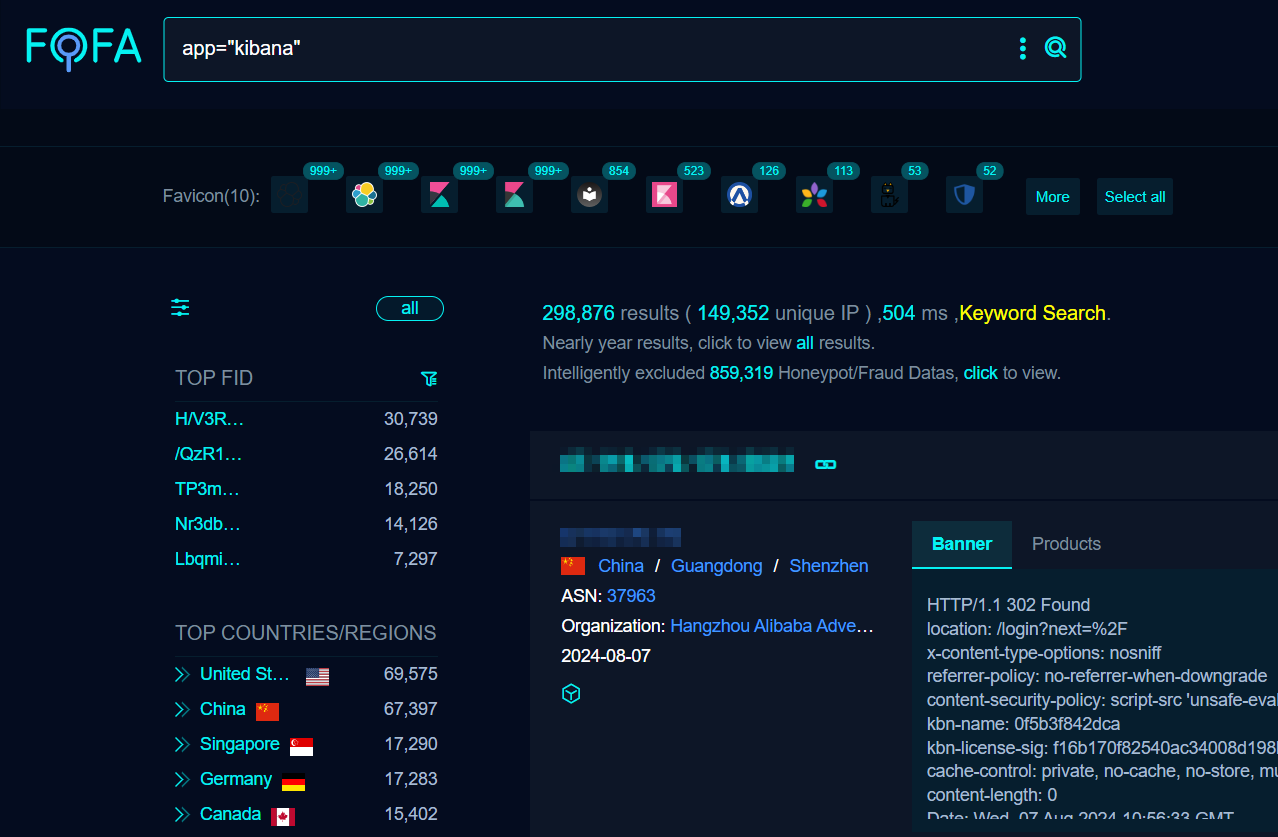
Kibana is a data visualization and exploration tool that allows users to create dashboards, reports, and visualizations from various data sources. Kibana processes and stores events in Elasticsearch then accesses the logs and displays them to the user through visualizations like line graphs, bar graphs, and pie charts.
Vulnerability Details
An attacker must have access to ML and Alerting connector features to exploit this prototype pollution vulnerability. Along with the access to ML connector features, an attacker must also have write access to internal ML indices.
Affected Environments
The vulnerability impacts:
- Self-managed Kibana installations on host Operating Systems
- Self-managed Kibana instances running the Kibana Docker image, but code execution is limited to the Kibana Docker container. An attacker may not further exploit the vulnerability, such as container escape, which is prevented by seccomp-bpf.
- Kibana instances running on Elastic Cloud, but code execution is limited to the Kibana Docker container. An attacker may not further exploit the vulnerability, such as container escape, which is prevented by seccomp-bpf and AppArmor profiles.
- Kibana instances running on Elastic Cloud Enterprise (ECE), but code execution is limited to the Kibana Docker container. An attacker may not further exploit the vulnerability, such as container escape, which is prevented by seccomp-bpf and AppArmor profiles.
- Kibana instances running on Elastic Cloud on Kubernetes (ECK), but code execution is limited to the Kibana Docker container. An attacker may not further exploit the vulnerability, such as container escape, which is prevented by seccomp-bpf when configured and supported.
Affected Versions
- Kibana 8.x versions prior to 8.14.2
- Kibana 7.x versions prior to 7.17.23
Mitigation
Customers must upgrade to Kibana version 8.14.2 and 7.17.23 or later to patch the vulnerability.
For more information, please refer to the Kibana Security Advisory.
Qualys Detection
Qualys customers can scan their devices with QID 380288 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References
https://discuss.elastic.co/t/kibana-8-14-2-7-17-23-security-update-esa-2024-22/364424