Microsoft’s August Patch Tuesday updates are out, and they address a range of vulnerabilities across multiple products. Let’s dive into the key updates and their implications.
Microsoft Patch’s Tuesday, August 2024 edition addressed 102 vulnerabilities, including nine critical and 77 important severity vulnerabilities.
In this month’s updates, Microsoft has addressed six actively exploited vulnerabilities, along with three publicly disclosed zero-day vulnerabilities (CVE-2024-21302, CVE-2024-38202, and CVE-2024-38199). There is a tenth publicly disclosed zero-day vulnerability (CVE-2024-38200) for which Microsoft has not released any patch.
Microsoft has addressed 12 vulnerabilities in Microsoft Edge (Chromium-based), which were patched earlier this month.
Microsoft Patch Tuesday, August edition includes updates for vulnerabilities in Microsoft Office and Components, Microsoft Windows DNS, Windows TCP/IP, Microsoft Teams, Windows Secure Boot, Windows Secure Kernel Mode, Windows Security Center, Windows SmartScreen, Windows App Installer, Windows Scripting, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Cross-site Scripting (XSS), Information Disclosure, Security Feature Bypass, and Remote Code Execution (RCE).
The August 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 5 | Important: 5 |
| Denial of Service Vulnerability | 6 | Important: 6 |
| Elevation of Privilege Vulnerability | 34 | Critical: 1 Important: 33 |
| Information Disclosure Vulnerability | 7 | Critical: 1 Important: 6 |
| Remote Code Execution Vulnerability | 28 | Critical: 4 Important: 24 |
| Security Feature Bypass Vulnerability | 4 | Important: 2 |
| Cross-site Scripting Vulnerability | 1 | Critical: 1 |
Zero-day Vulnerabilities Patched in August Patch Tuesday Edition
CVE-2024-38178: Scripting Engine Memory Corruption Vulnerability
An attacker may exploit the vulnerability by convincing an authenticated user to a specially crafted URL to be compromised by the attacker.
CISA acknowledged the active exploitation of CVE-2024-38178 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
CVE-2024-38193: Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
The Windows Ancillary Function Driver (AFD) for WinSock (afd.sys) is a kernel entry point for the Winsock API.
An attacker who successfully exploits the vulnerability could gain SYSTEM privileges.
CISA acknowledged the active exploitation of CVE-2024-38193 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
CVE-2024-38213: Windows SmartScreen Security Feature Bypass Vulnerability
Windows SmartScreen, also known as Microsoft Defender SmartScreen or SmartScreen Filter, is a cloud-based service that helps protect users from malicious websites, applications, and downloads.
An attacker must send the user a malicious file and convince them to open it. On successful exploitation, an attacker could bypass the SmartScreen user experience.
CISA acknowledged the active exploitation of CVE-2024-38213 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
CVE-2024-38106: Windows Kernel Elevation of Privilege Vulnerability
The Windows kernel is the core of the Windows operating system (OS). It is a computer program that provides essential services for the OS, including low-level operations, scheduling threads, routing hardware interruptions, and more.
An attacker must win a race condition to exploit the vulnerability successfully. An attacker who successfully exploits the vulnerability could gain SYSTEM privileges.
CISA acknowledged the active exploitation of CVE-2024-38106 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
CVE-2024-38189: Microsoft Project Remote Code Execution Vulnerability
Microsoft Project is project management software designed to assist a project manager in developing a schedule, assigning resources to tasks, tracking progress, managing the budget, and analyzing workloads.
The vulnerability can be exploited in two types of attacks:
- Email attack scenario: In this attack, an attacker must convince users to open a malicious file sent to them in an email attachment.
- Web-based attack scenario: In this attack, an attacker can host a website containing a malicious file designed.
CISA acknowledged the active exploitation of CVE-2024-38189 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
CVE-2024-38107: Windows Power Dependency Coordinator Elevation of Privilege Vulnerability
Power Dependency Coordinator (PDC is a component of Modern Standby.
On successful exploitation, an attacker could gain SYSTEM privileges.
CISA acknowledged the active exploitation of CVE-2024-38107 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before September 3, 2024.
Critical Severity Vulnerabilities Patched in August Patch Tuesday Edition
CVE-2024-38159 & CVE-2024-38160: Windows Network Virtualization Remote Code Execution Vulnerability
Windows Network Virtualization (WNV) allows developers to send on-demand policy requests to a data center management server or orchestrator. These requests can respond to virtual machine life cycle events, such as provisioning and live migration.
An attacker may exploit the vulnerability by leveraging the unchecked return value in the wnv.sys component of Windows Server 2016. An attacker may cause unauthorized memory writes or even free a valid block currently in use by manipulating the Memory Descriptor List (MDL) content. Successful exploitation of the vulnerability may lead to a critical guest-to-host escape.
CVE-2023-40547: Shim RCE in HTTP boot support may lead to secure boot bypass
The vulnerability exists in Linux Shim boot. Successful exploitation of the vulnerability could lead to remote code execution, crash, denial of service, and exposure of sensitive data under specific circumstances.
CVE-2024-38063: Windows TCP/IP Remote Code Execution Vulnerability
Transmission Control Protocol/Internet Protocol (TCP/IP) is an industry-standard protocol suite designed for large networks of network segments connected by routers. TCP/IP is the core protocol suite used on the Internet.
An unauthenticated attacker may send IPv6 packets, including specially crafted packets, to a Windows machine, which can lead to remote code execution.
CVE-2024-38140: Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability
Reliable multicast transport is a computer networking protocol that sends messages from one sender to multiple receivers in a distributed system, ensuring that all intended recipients receive the message accurately and in the correct order.
An unauthenticated attacker may exploit the vulnerability by sending specially crafted packets to a Windows Pragmatic General Multicast (PGM) open socket on the server. Exploitation of the vulnerability does not require any user interaction.
CVE-2024-38166: Microsoft Dynamics 365 Cross-site Scripting Vulnerability
Microsoft Dynamics 365 is an integrated suite of enterprise resource planning and customer relationship management applications offered by Microsoft. It combines various functions such as sales, customer service, field service, operations, finance, marketing, and project service automation into a single platform.
An unauthenticated attacker may exploit improper neutralization of input during web page generation in Microsoft Dynamics 365 to spoof over a network. An attacker must convince a user to click on a link to exploit the vulnerability successfully.
CVE-2024-38206: Microsoft Copilot Studio Information Disclosure Vulnerability
Microsoft Copilot Studio is a graphical, low-code tool for creating and maintaining copilots. A copilot is an AI-powered conversational interface based on large language models (LLMs) and additional sources of knowledge.
An authenticated attacker may bypass Server-Side Request Forgery (SSRF) protection in Microsoft Copilot Studio to disclose sensitive information over a network.
CVE-2024-38109: Azure Health Bot Elevation of Privilege Vulnerability
An authenticated attacker may exploit a Server-Side Request Forgery (SSRF) vulnerability in Microsoft Azure Health Bot. On successful exploitation, an attacker may elevate privileges over a network.
CVE-2022-3775: Heap-based out-of-bounds write when rendering certain Unicode sequences
Microsoft has not released any information about the vulnerability.
Other Microsoft Vulnerability Highlights
- CVE-2024-38196 is an elevation of privilege vulnerability in the Windows Common Log File System Driver. On successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2024-38198 is an elevation of privilege vulnerability in Windows Print Spooler. An attacker must win a race condition to exploit the vulnerability. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38125 is an elevation of privilege vulnerability in Kernel Streaming WOW Thunk Service Driver. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38133 is an elevation of privilege vulnerability in Windows Kernel. An attacker may exploit the vulnerability by convincing a user to send a request to a malicious server. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2024-38141 is an elevation of privilege vulnerability in Windows Ancillary Function Driver for WinSock. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38144 is an elevation of privilege vulnerability in Kernel Streaming WOW Thunk Service Driver. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2024-38147 is an elevation of privilege vulnerability in Microsoft DWM Core Library. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges. To exploit this vulnerability, an attacker must log on to the system.
- CVE-2024-38148 is a denial-of-service vulnerability in Windows Secure Channel.
- CVE-2024-38150 is an elevation of privilege vulnerability in Windows DWM Core Library. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38163 is an elevation of privilege vulnerability in the Windows Update Stack. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Kerberos, Microsoft Office, Azure Connected Machine Agent, Windows Kernel, Windows Power Dependency Coordinator, Azure Stack, Azure Health Bot, Windows IP Routing Management Snapin, Windows NTFS, Microsoft Local Security Authority Server (lsasrv), Windows Routing and Remote Access Service (RRAS), Microsoft Bluetooth Driver, Microsoft Streaming Service, Windows Network Address Translation (NAT), Windows Clipboard Virtual Channel Extension, Windows NT OS Kernel, Windows Resource Manager, Windows Deployment Services, Reliable Multicast Transport Driver (RMCAST), Windows Ancillary Function Driver for WinSock, Windows WLAN Auto Config Service, Windows Layer-2 Bridge Network Driver, Windows DWM Core Library, Windows Transport Security Layer (TLS), Microsoft WDAC OLE DB provider for SQL, Azure IoT SDK, Windows Network Virtualization, Windows Mobile Broadband, Windows Update Stack, Windows Compressed Folder, Microsoft Dynamics, .NET and Visual Studio, Microsoft Office Visio, Microsoft Office Excel, Microsoft Office PowerPoint, Microsoft Office Outlook, Windows Kernel-Mode Drivers, Microsoft Office Project, Azure CycleCloud, Windows Common Log File System Driver, Windows Print Spooler Components, Line Printer Daemon Service (LPD), Microsoft Copilot Studio, Windows Mark of the Web (MOTW), Windows Cloud Files Mini Filter Driver, Microsoft Edge (Chromium-based), and Windows Initial Machine Configuration.
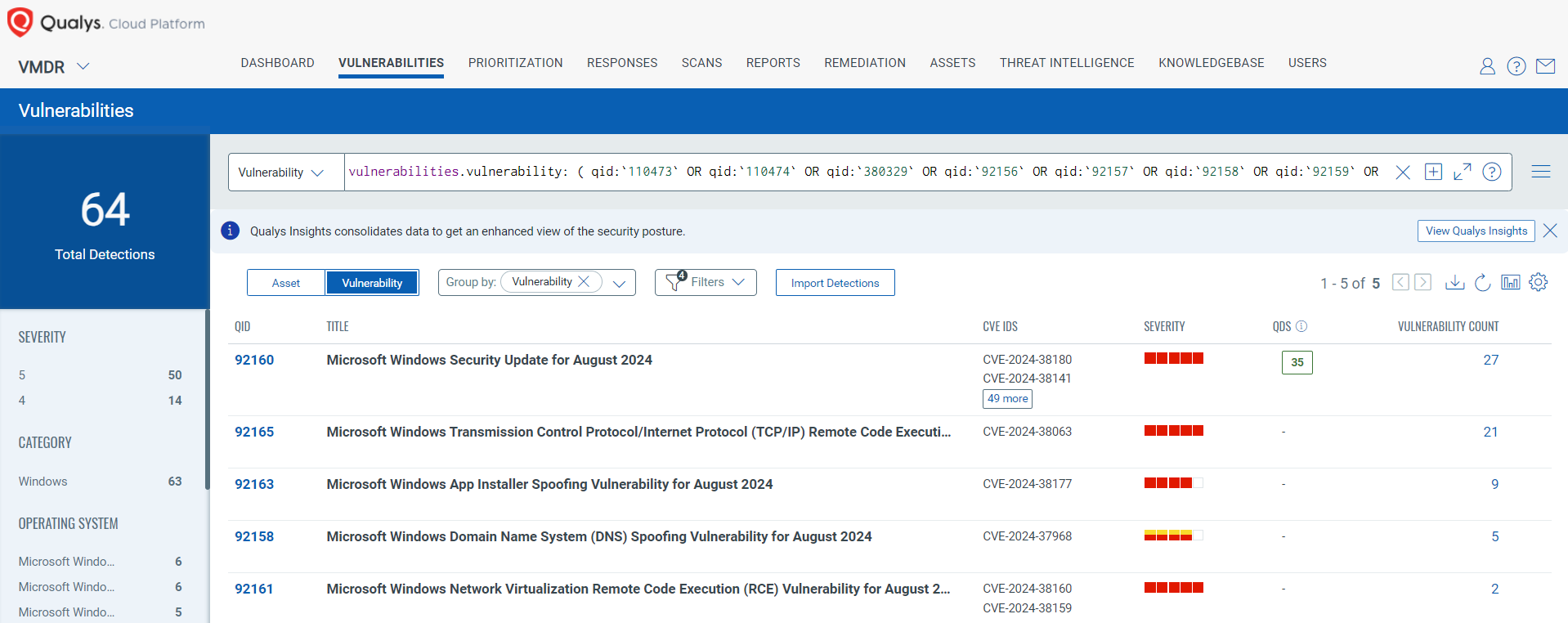
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110473` OR qid:`110474` OR qid:`380329` OR qid:`92156` OR qid:`92157` OR qid:`92158` OR qid:`92159` OR qid:`92160` OR qid:`92161` OR qid:`92162` OR qid:`92163` OR qid:`92164` OR qid:`92165`)
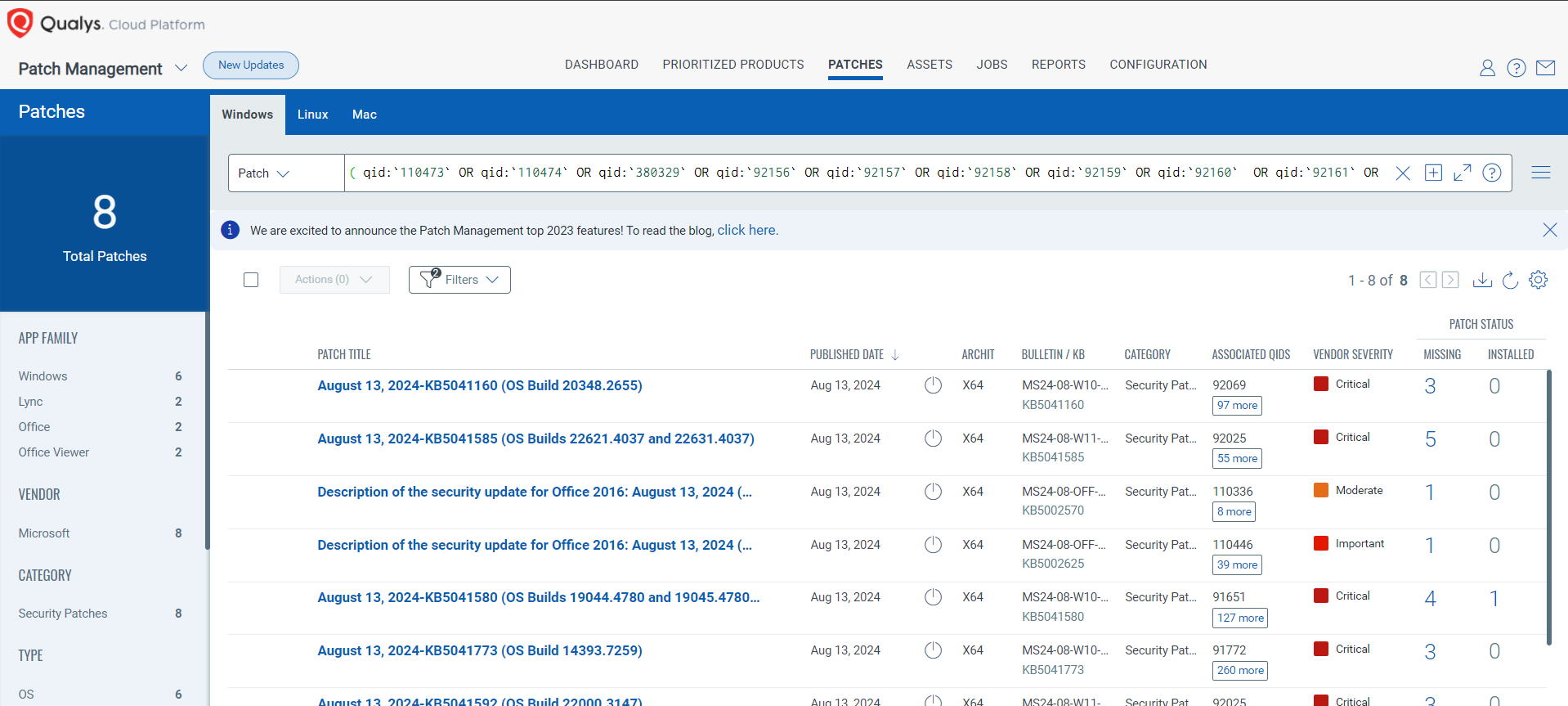
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110473` OR qid:`110474` OR qid:`380329` OR qid:`92156` OR qid:`92157` OR qid:`92158` OR qid:`92159` OR qid:`92160` OR qid:`92161` OR qid:`92162` OR qid:`92163` OR qid:`92164` OR qid:`92165`)
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now, these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
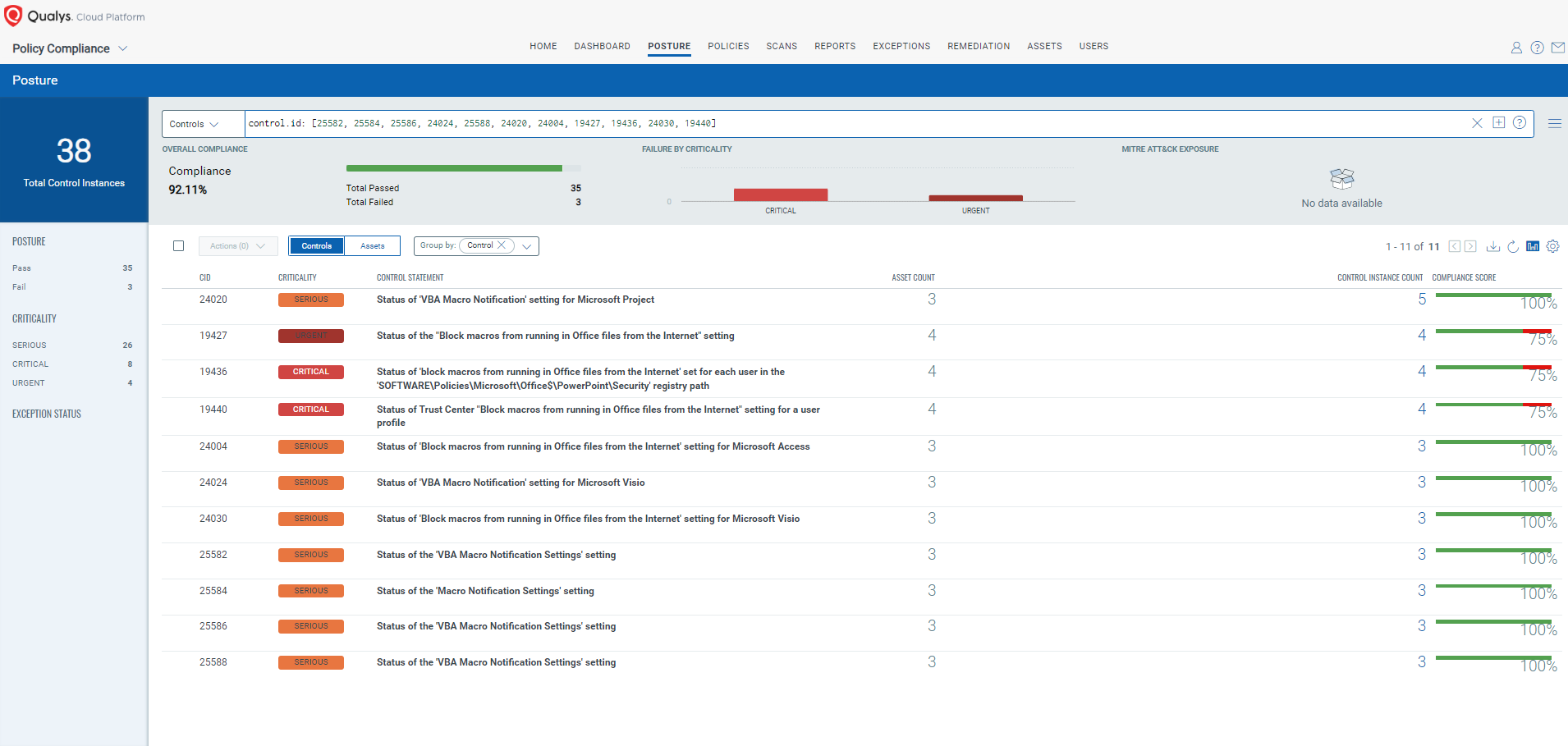
CVE-2024-38189: Microsoft Project Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 8.8 / 8.2
Policy Compliance Control IDs (CIDs):
- 25582 Status of the ‘VBA Macro Notification Settings’ setting
- 25584 Status of the ‘Macro Notification Settings’ setting
- 25586 Status of the ‘VBA Macro Notification Settings’ setting
- 24024 Status of ‘VBA Macro Notification’ setting for Microsoft Visio
- 25588 Status of the ‘VBA Macro Notification Settings’ setting
- 24020 Status of ‘VBA Macro Notification’ setting for Microsoft Project
- 24004 Status of ‘Block macros from running in Office files from the Internet’ setting for Microsoft Access
- 19427 Status of the “Block macros from running in Office files from the Internet” setting
- 19436 Status of ‘block macros from running in Office files from the Internet’ set for each user in the ‘SOFTWARE\Policies\Microsoft\Office$\PowerPoint\Security’ registry path
- 24030 Status of ‘Block macros from running in Office files from the Internet’ setting for Microsoft Visi0
- 19440 Status of Trust Center “Block macros from running in Office files from the Internet” setting for a user profile
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [25582, 25584, 25586, 24024, 25588, 24020, 24004, 19427, 19436, 24030, 19440]
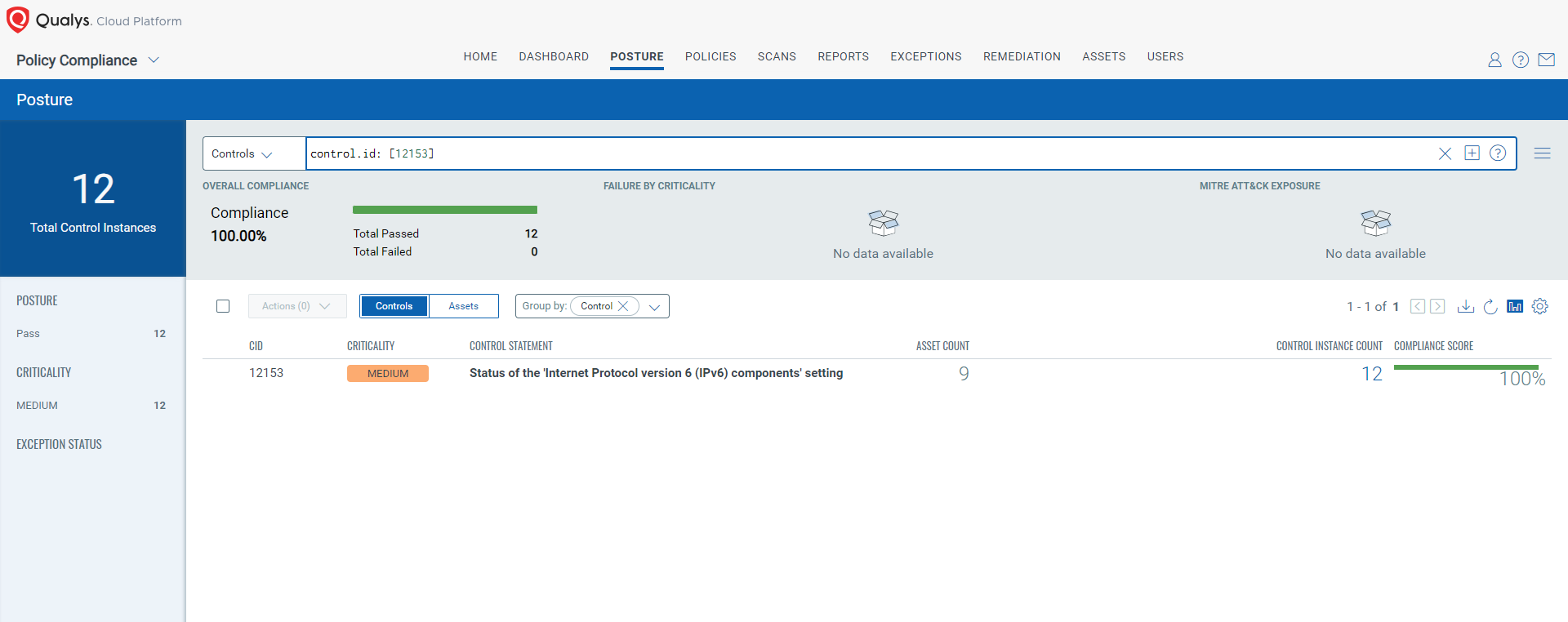
CVE-2024-38063: Windows TCP/IP Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 12153 Status of the ‘Internet Protocol version 6 (IPv6) components’ setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [12153]
CVE-2024-38159: Windows Network Virtualization Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.1 / 7.9
CVE-2024-38160: Windows Network Virtualization Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.1 / 7.9
Policy Compliance Control IDs (CIDs):
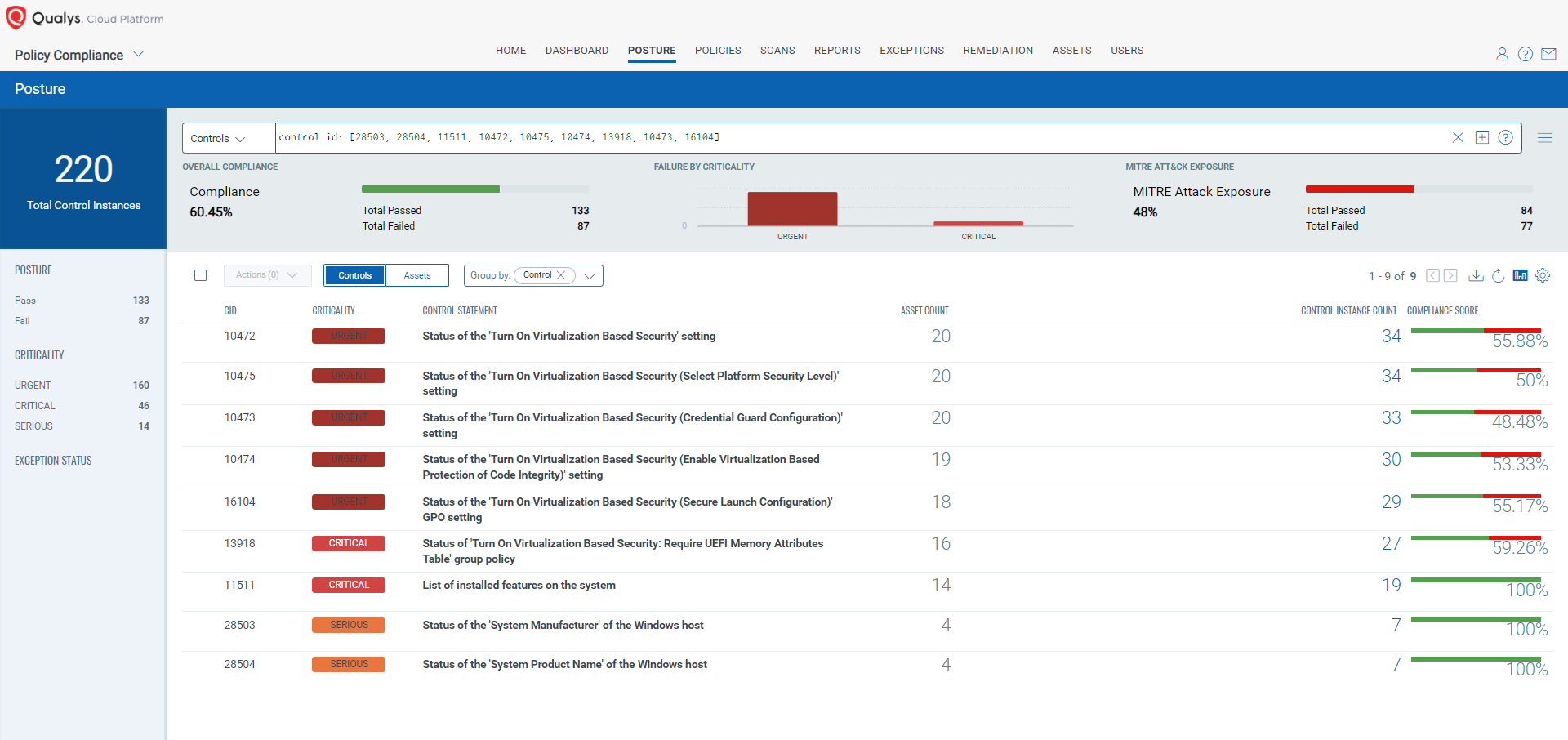
- 28503 Status of the ‘System Manufacturer’ of the Windows host
- 28504 Status of the ‘System Product Name’ of the Windows host
- 11511 List of installed features on the system
- 10472 Status of the ‘Turn On Virtualization Based Security’ setting
- 10475 Status of the ‘Turn On Virtualization Based Security (Select Platform Security Level)’ setting
- 10474 Status of the ‘Turn On Virtualization Based Security (Enable Virtualization Based Protection of Code Integrity)’ setting
- 13918 Status of ‘Turn On Virtualization Based Security: Require UEFI Memory Attributes Table’ group policy
- 10473 Status of the ‘Turn On Virtualization Based Security (Credential Guard Configuration)’ setting
- 16104 Status of the ‘Turn On Virtualization Based Security (Secure Launch Configuration)’ GPO setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [28503, 28504, 11511, 10472, 10475, 10474, 13918, 10473, 16104]
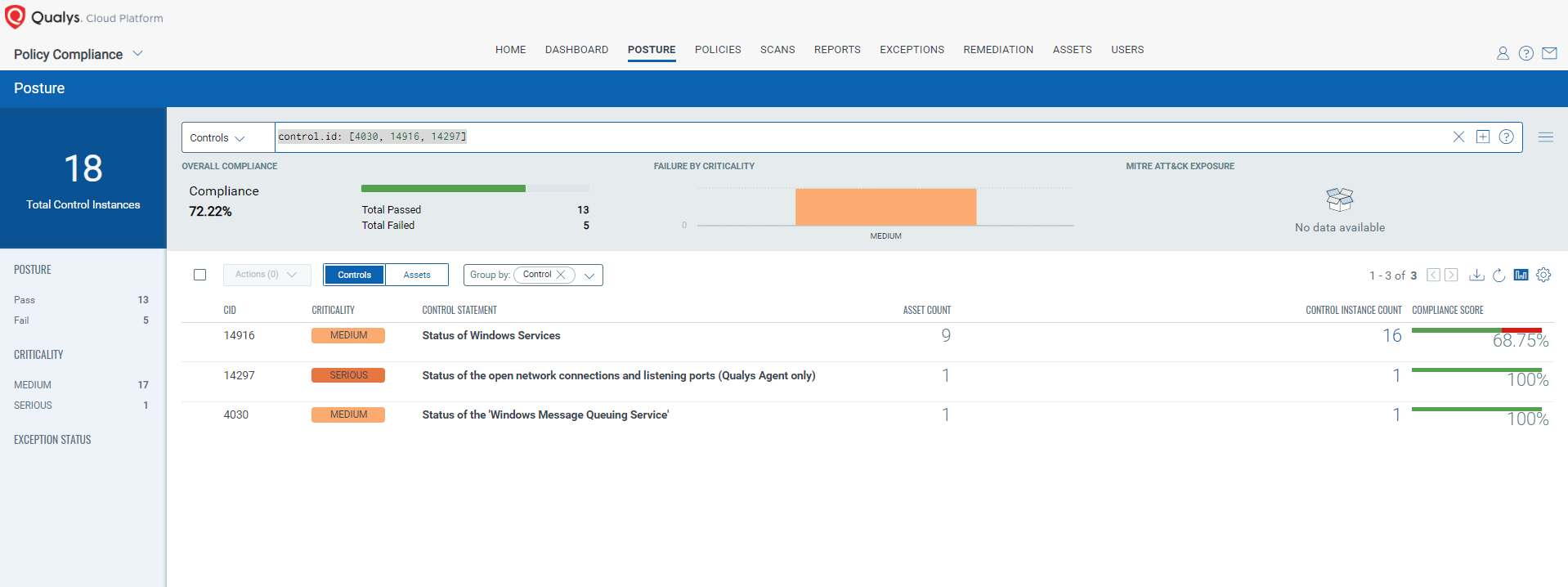
CVE-2024-38140: Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the ‘Windows Message Queuing Service’
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030, 14916, 14297]
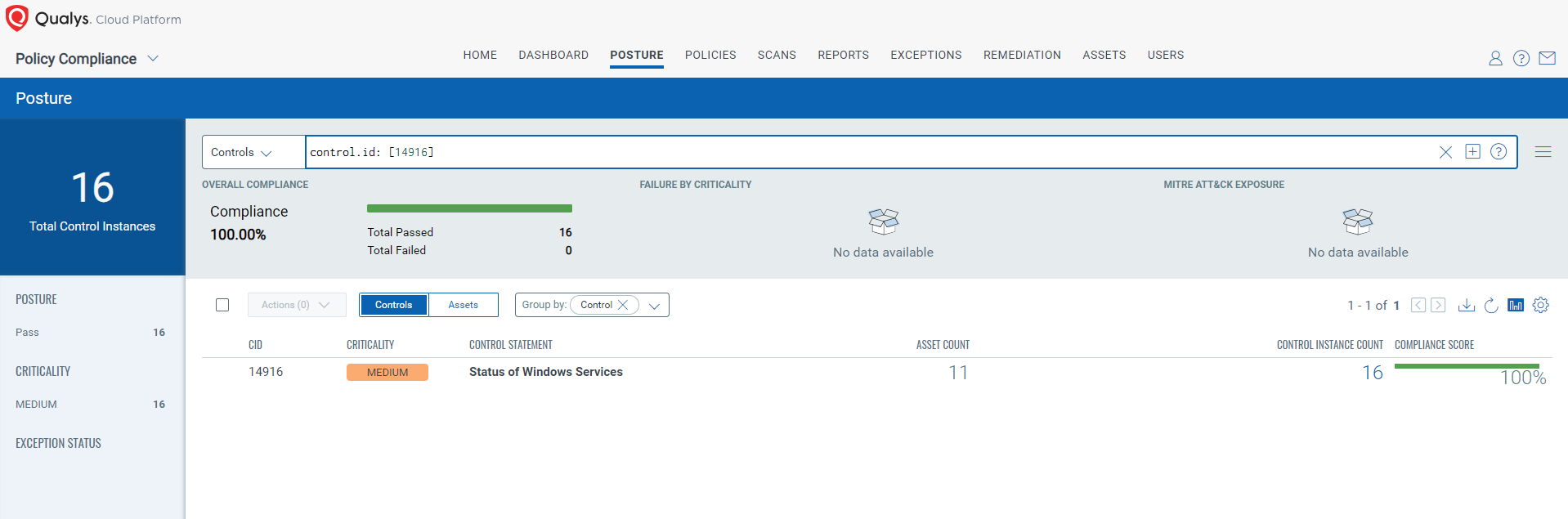
CVE-2024-38199: Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 14916 Status of Windows Services
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [14916]
Visit the August 2024 Security Updates page to access the full description of each vulnerability and the systems it affects.
Qualys customers can scan their network with QIDs 110473, 110474, 380329, 92156, 92157, 92158, 92159, 92160, 92161, 92162, 92163, 92164, and 92165 to detect vulnerable assets.
Please continue to follow Qualys Threat Protection for more coverage of the latest vulnerabilities.
References:
https://msrc.microsoft.com/update-guide
https://msrc.microsoft.com/update-guide/releaseNote/2024-Aug
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2022-3775
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38109
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38206
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38166
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38200
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38140
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38063
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2023-40547
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38160
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38159
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38107
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38189
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38106
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38213
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38193
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-38178